

Backtrack 5: Penetration Testing with Social Engineering Toolkit. Social engineering attacks are one of the top techniques used against networks today.
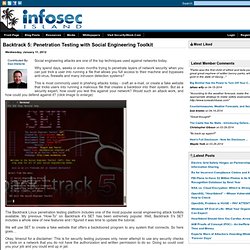
Why spend days, weeks or even months trying to penetrate layers of network security when you can just trick a user into running a file that allows you full access to their machine and bypasses anti-virus, firewalls and many intrusion detection systems? This is most commonly used in phishing attacks today - craft an e-mail, or create a fake website that tricks users into running a malicious file that creates a backdoor into their system. But as a security expert, how could you test this against your network? Would such an attack work, and how could you defend against it? (click image to enlarge) The Backtrack Linux penetration testing platform includes one of the most popular social engineering attack toolkits available. WebWise - BBC - WebWise - A to Z Glossary. Guice - Guice (pronounced 'juice') is a lightweight dependency injection framework for Java 5 and above, brought to you by Google. Versatile .CC Attacks. 02 Mar 11 Filed in Website exploits A few days ago I tweeted that “this year the most popular TLD for malicious sites is .CC“.
I conducted some research on the most prevalent attacks that use the .CC TLD and now want to elaborate on what is going on. Lately, the majority of websites with security problems (that people check on Unmask Parasites) have very similar “What happened when Google visited this site?” Sections on their Safe Browsing diagnostic pages. They mention several malicious site on .cc domains, e.g. Malicious software is hosted on 8 domain(s), including gsdg2g32 .co.cc/, asfiuweof .co.cc/, hndfdfnfdnxdnf .vv.cc/. Phishing. An example of a phishing email, disguised as an official email from a (fictional) bank.
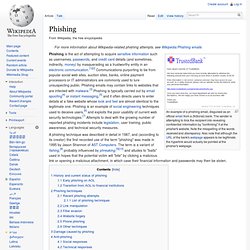
The sender is attempting to trick the recipient into revealing confidential information by "confirming" it at the phisher's website. Note the misspelling of the words received and discrepancy. Also note that although the URL of the bank's webpage appears to be legitimate, the hyperlink would actually be pointed at the phisher's webpage. A phishing technique was described in detail in 1987, and (according to its creator) the first recorded use of the term "phishing" was made in 1995 by Jason Shannon of AST Computers. The term is a variant of fishing,[8] probably influenced by phreaking,[9][10] and alludes to "baits" used in hopes that the potential victim will "bite" by clicking a malicious link or opening a malicious attachment, in which case their financial information and passwords may then be stolen. History and current status of phishing[edit] Early phishing on AOL[edit] Phishing techniques[edit]
The Little Black Book of Computer Viruses. Online BackTrack Security Training by Offensive Security. The Creators of BackTrack have developed training that will take you through all aspects of a penetration test.
Whether you are a seasoned penetration tester or just starting off, we have a course that can help you take your skills to the next level. Our online courses are designed to give you flexibility to work at your own pace. Our flagship course, Penetration Testing With Kali (PWB) will open your eyes to the skills needed to perform a penetration test from A to Z. After that you can move on to Cracking the Perimeter (CTP) – which focuses on exploitation using many of the skills you learned in the PWB class.
Our courses are designed to work with a combination of our videos, pdf’s and a full lab environment. List of Videos for Java. Top 10 Web hacking techniques of 2010 revealed. Network World - A Web hack that can endanger online banking transactions is ranked the No. 1 new Web hacking technique for 2010 in a top 10 list selected by a panel of experts and open voting.

Called the Padding Oracle Crypto Attack, the hack takes advantage of how Microsoft's Web framework ASP.NET protects AES encryption cookies. FROM THE SECURITY WORLD: Quirky moments at Black Hat DC 2011 If encryption data in the cookie has been changed, the way ASP.NET handles it results in the application leaking some information about how to decrypt the traffic. With enough repeated changes and leaked information, the hacker can deduce which possible bytes can be eliminated from the encryption key. Malicious Linux Commands - From (This article was originally published in Ubuntu Forums but was removed there.

Ubuntuguide feels that knowledge about these risks is more important than any misguided attempts to "protect the public" by hiding their potential dangers or protect the (K)Ubuntu/Linux image. The original article has therefore been re-created (and subsequently edited) here.) ATTENTION: It is worthwhile to have some basic awareness about malicious commands in Linux. The Best Hacking Tutorial Sites - Learn Legal Hacking - StumbleUpon. Writing shell scripts - Lesson 3: Here Scripts. Beginning with this lesson, we will construct a useful application.
This application will produce an HTML document that contains information about your system. I spent a lot of time thinking about how to teach shell programming, and the approach I have chosen is very different from most others that I have seen. Most favor a systematic treatment of shell features, and often presume experience with other programming languages. Although I do not assume that you already know how to program, I realize that many people today know how to write HTML, so our program will produce a web page.
As we construct our script, we will discover step by step the tools needed to solve the problem at hand. As you may know, a well formed HTML file contains the following content: <html><head><title> The title of your page </title></head><body> Your page content goes here. Now, with what we already know, we could write a script to produce the above content: