

Colección de herramientas de "pentesting" para entornos Windows. Punching holes into firewalls. Or "Why firewalls shouldn't be considered a ultimate weapon for network security" or "Secure TCP-into-HTTP tunnelling guide" Introduction Firewalls are heavily used to secure private networks (home or corporate).

Usually, they are used to protect the network from: A web abissal e o ativismo digital. O Facebook não é uma plataforma segura para o ativismo na web.
Muito pelo contrário: a rede é conhecida por sua insistência em invadir a privacidade alheia e distribuir dados de usuários a empresas e agentes da lei. Por isso muitos ciberativistas têm recorrido à Deep Web, a web profunda. Nas redes sociais brasileiras, agora que os governos estaduais partiram para a ação dentro delas, já estão presentes menções a uma possível fuga para as profundezas da web invisível. A web profunda é composta por todos os sites não indexados em motores de busca. The Hacks of Mr. Robot: How to Hack Bluetooth. Episode 6 of Mr.
Robot has come and gone and, as usual, it did not disappoint. Once again our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us. In this episode, Elliot is being blackmailed by the ruthless and unrelenting drug dealer, Vera, to hack him out of jail.
NSA has VPNs in Vulcan death grip—no, really, that’s what they call it. The National Security Agency’s Office of Target Pursuit (OTP) maintains a team of engineers dedicated to cracking the encrypted traffic of virtual private networks (VPNs) and has developed tools that could potentially uncloak the traffic in the majority of VPNs used to secure traffic passing over the Internet today, according to documents published this week by the German news magazine Der Speigel.
A slide deck from a presentation by a member of OTP’s VPN Exploitation Team, dated September 13, 2010, details the process the NSA used at that time to attack VPNs—including tools with names drawn from Star Trek and other bits of popular culture. OTP’s VPN exploit team had members assigned to branches focused on specific regional teams, as well as a “Cross-Target Support Branch” and a custom development team for building specialized VPN exploits. Spam SMS. Buggedplanet.info. Stuxnet: Anatomy of a Computer Virus. Google Search 3T.
Computer Hacking. WikiLeaks e os conflitos no ciberespaço - Parte I. 19 de dezembro de 2010 Categoria: Mundo A revelação de documentos secretos da diplomacia dos Estados Unidos abre uma batalha pela liberdade da informação.
Por Passa Palavra. WikiLeaks e os conflitos no ciberespaço - Parte II. 21 de dezembro de 2010 Categoria: Mundo O estabelecimento do ciberespaço como uma dimensão da guerra abre a possibilidade de uma ofensiva militar contra a rede.
Por Passa Palavra. Brasil está entre os menos preparados contra hackers - Economia. HOWTO bypass Internet Censorship, a tutorial on getting around filters and blocked ports. Index of /content/downloads/pdf. Bypass Firewalls - Preserve your online Anonymity, Privacy & Security - HTTP Tunnel Corp. Bruce Schneier on how to choose secure passwords. Part of my job requires asking for people's passwords for their computer. in order to do diagnostics & repair.

They don't have to provide it if they don't want to. I can think of one person who opted for this, and he was a software developer, he encrypted everything, he had good backups — most people don't do that, either — and he preferred to have everything deleted rather than give out the password. Fair enough, all prudent practices. They're welcome to change it to a dummy value — blank, a dictionary word, etc — and change it back afterwards.
The percent that opts for this is probably in the single-digits. Screenshot Tour: How to crack a Windows password with Ophcrack Live CD. There are simpler ways to "crack" a password.
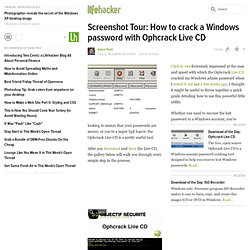
First you could try mspassview which you can download from Microsoft's website. It kinda assumes you already have limited access to the computer in question and the the antivirus/firewall can be turned off. UPDATE 2-FBI arrests 14 in probe of hacker group Anonymous. Hacking. Anonymous. WikiLeaks: Anonymous hierarchy emerges. They were described as a leaderless, anarchic group of "hacktivists" who briefly brought down MasterCard, Visa and PayPal after those companies cut off financial services to WikiLeaks.
But inside Anonymous, the Guardian has found that the organisation is more hierarchical – with a hidden cabal of around a dozen highly skilled hackers co-ordinating attacks across the web. The secretive group that directs the Anonymous network was also behind the assault on the Gawker websites in the US at the weekend, according to documents seen by the Guardian. That led to email addresses and passwords of more than 1.3 million Gawker users being made public, and spawned a spam attack on Twitter that is now being investigated by the FBI. In the last 10 days, Anonymous has also orchestrated Operation Payback, which attacked Visa, MasterCard and PayPal for cutting off financial services to WikiLeaks under pressure from the US government.
The darkness at the heart of Anonymous. Louise Mensch, the Conservative MP, didn't react as perhaps the sender of the threatening email she received on Monday had hoped.
Empty suit: the chaotic way Anonymous makes decisions. On February 16, the freewheeling hacker collective decided to take on the Kansas-based Westboro Baptist Church, best known for its "God Hates Fags" protests. The Anonymous hivemind, the "Voice of Free Speech & the Advocate of the People," has had enough of this sort of free speech and has decided to fight the church's "assembly of graceless sociopaths and maniacal chauvinists & religious zealots" who issue "venomous statements of hatred.
" The manifesto contains the trademark Anonymous prose style, one that might be summed up with the words "florid bombasticism. "