

Hacker: traçage Wind phone. Data Extraction to bypass password Michigan. Satelite encryption cracked. Privacy boss slams German police's mobile ta. US AT&T surveillance. Vulnerability known in 2005 T-Mob. Zuckerberg: Anonymity Online. Greg Miskiw to fly to UK for police talks. Life under digits. Update 20/03/2012 This could be titled ‘when reality catch up with science fiction’.
This week on Twitter Privacy Matter. Life under digit continues. Update 24/02/2013: Surveillance keeps expanding.
Drones proliferation, there cheap fabrications and tentative of regulation regularly on the news. I have been collecting many articles on the subjects of surveillance, tracking, spying, and drones on my Pearltrees for anyone interested to make its own opinion. I am reading today a very well analysed essay by Ian Brown, Oxford Universitty Institute of Internet, on Drones surveillance and identity, titled ‘Privacy, surveillance and technologies impact on identity.’ Hacker shows how he can intercept cell phone calls with $1,500 device (video) A security researcher showed in a live demo today how he can intercept cell phone calls on 80 percent of the world’s phones with just about $1,500 worth of equipment.
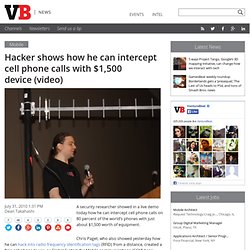
Chris Paget, who also showed yesterday how he can hack into radio frequency identification tags (RFID) from a distance, created a fake cell phone tower, or Global System for Mobile communications (GSM) base station. GSM is the protocol for 80 percent of the world’s phones and is used by T-Mobile and AT&T in the U.S. The demo was not, Paget said, a malicious attack in any way. Military and intelligence agencies can intercept cell phone calls with their wiretapping technology. But Paget simply wanted to show how vulnerable the cell phone network is and how hackers could intercept calls for a small amount of money. SourceWatch. Koch Spy Agency Led by Voter Fraud Huckster The Kochs have been complaining about a "lack of civility in politics" as they seek to boost their public image--but one of their top operatives helped propel perhaps the most egregious case of race-baiting voter fraud hucksterism in recent years.

At the same time that the Kochs have been on a PR blitz, publicly spinning an image of themselves as well-intentioned patriots trying to make the world a better place and decrying "character assassination," they've been quietly ramping up a clandestine surveillance and intelligence gathering operation focused on their perceived political enemies, Ken Vogel reports at Politico. At the helm of this "competitive intelligence" operation is a man named Mike Roman, Vice President of Research for Kochs' Freedom Partners and who was paid $265,000 last year, according to Freedom Partners' recent tax filing.
Privacy lawyer challenges police view of intercept law. The Met's Assistant Commissioner John Yates told MPs that the police force's legal advice was that it was not against the law to hack into messages that someone has already received.
Data protection law expert Rosemary Jay has challenged this interpretation of the law. Phone hacking report: see how the select committee voted on each amendment. The phone hacking report by the Commons culture, media and sport select committee is out today and it is pretty critical of both Rupert and James Murdoch, as well as many of the other players in the story so far.
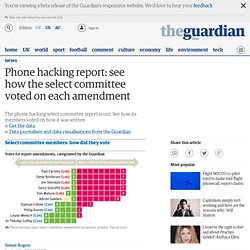
Writing today, Dan Sabbagh and Josh Haliday say that. US senator invokes website-hacking trial in call for Murdoch inquiry. In July 1999, two brothers called George and Richard Rebh, the founders of a small start-up company called Floorgraphics, were invited to lunch with the dominant firm in their new area of business.
The brothers were excited: they had invented a new product that involved sticking giant adverts on the floors of supermarkets, and were keen to show it off to the market leaders and talk about possible joint promotions. They met the two top executives from the big firm, News America Marketing, in a Cantonese restaurant called A Dish of Salt in midtown Manhattan. Data que les operateurs telephoniques peuvent transmettre.
LulzSec hack: News International removes remote access. News International took its remote access and webmail systems offline for 12 hours, and is resetting the passwords for all users after the company's systems were breached by members of the hacking group LulzSec.
The hackers appear to have gained access to the database with email and password details, some of which were published online last night on the Twitter accounts of some of LulzSec's members. Taking webmail and remote access offline was the only way that News International could be sure that nobody from the group who might have access to the details can log in and steal emails belonging to staff. In a note sent out to all News International staff at 11.05pm on Tuesday night, soon after LulzSec hacked a server in the company's systems to redirect people visiting the Sun's main web page to a faked story suggesting Rupert Murdoch had been found dead, the company said there has been a "security breach". Soundminer, un malware espionne et vole les données des smartphones Android.