

Iranian Cyberspies Pose as Journalists Online To Ensnare Their Targets. Cyberspying campaign out of Iran combines social engineering and social media to steal credentials from a wide array of US and Israeli military, government, and defense contractors.
A Study in Bots: Newscaster. In many malware cases, the infection method can be far more elaborate than the actual malware being installed.
This is the case with Newscaster, a campaign believed to have Iranian origins and targeting US defense contractors, high ranking military officials, and government officials. With an infection vector so involved, and malware as simple as it is, this campaign was able to avoid detection since it began in 2011. Spreading the news In a report for the recently exposed attack dubbed “Newscaster” by iSIGHT Partners (documented here) highlight how social networks, combined with social engineering efforts continue to be a highly successful attack vector. The level of effort, time and detail expended, combined with the profile of the victims was significant. Fake news site that was used in the attacks Potential Facebook site used in the attacks The attacks in this campaign came from an attacker posing as a legitimate persona, sharing common interests or business goals.
VirusTotal analysis. Iranian hackers are targeting U.S. officials through social networks, report says. A group of Iranian hackers has waged a creative campaign of cyber-espionage, targeting hundreds of high-ranking U.S. defense, diplomatic and other officials who are lured to fake Web sites through an elaborate social media network that features a bogus online news site, according to a new report.
Since at least 2011, the hackers have targeted current and former senior military officials, including a four-star admiral; current and former foreign policy officials who work on nonproliferation issues; as well as personnel from more than 10 U.S. and Israeli defense contractors, according to iSight Partners, a cybersecurity research firm. Iranian hackers use fake news site, social media to spy on US, Israel leaders – report. CBC News - Iranian hackers use Facebook to spy on U.S. Iranian 'Newscaster' cyber spies snooped on US and Israeli officials. Iran-based hackers used fake personas on Facebook, Twitter, LinkedIn, Google+, YouTube and Blogger to mount a far-reaching cyber espionage campaign targeting US and Israeli officials.
Security firm iSight Partners tracked the campaign to a group of Iranian hackers which it claims has ensnared as many as 2,000 victims across the globe in an operation dubbed 'Newscaster'. "This campaign, working undetected since 2011, targets senior US military and diplomatic personnel, congressional personnel, Washington DC area journalists, US think tanks, defence contractors in the US and Israel, as well as others who are vocal supporters of Israel to covertly obtain log-in credentials to the email systems of their victims," read the report. The attacks targeted people with requests from fake online personas claiming to work in journalism, government and defence contracting. "Accounts were then targeted with 'spear-phishing' messages.
"We are unable to say with complete visibility. Operation Cleaver: Iran's state-sponsored hackers infiltrate airport and airline security. A group of hackers based in Iran called Tarh Andishan, backed by the Iranian government, are carrying out a co-ordinated and sophisticated campaign of cyber-attacks against critical infrastructure organisations around the world, which could be putting the lives of millions of airline passengers in danger.
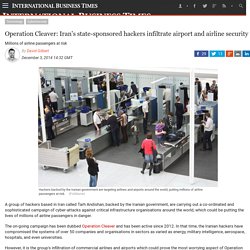
The on-going campaign has been dubbed Operation Cleaver and has been active since 2012. In that time, the Iranian hackers have compromised the systems of over 50 companies and organisations in sectors as varied as energy, military intelligence, aerospace, hospitals, and even universities. However, it is the group's infiltration of commercial airlines and airports which could prove the most worrying aspect of Operation Cleaver.
Cylance, the security company which has been tracking the hackers, says in its 56-page report into the hacking campaign that "there is a possibility that this campaign could affect airline passenger safety". "Bone-chilling evidence" "The end goal is not known" Newscaster, l'opération iranienne. La société américaine de sécurité et de renseignement informatique iSight Partners vient de mettre en lumière une opération de cyber-espionnage de grande envergure ciblant de nombreuses personnalités américaines, israéliennes, britanniques et saoudiennes.
Newscaster a débuté en 2011 en s'appuyant sur les réseaux sociaux, sur la création de profils fictifs et sur la construction d'un site d'information accrochant puis piégeant ses cibles. L'étude technique menée par iSight Partners attribue l'opération à un groupe professionnel de hackers iraniens. Déployée dans la durée, son niveau de complexité, sa furtivité (active durant trois ans) et les moyens employés, suggèrent clairement une expertise et une supervision étatique. La montée en puissance de l'opération a été très progressive. Certains y verront la réponse iranienne à l'agression « Stuxnet » subie par Téhéran en 2010. Les cibles. Iranian Hackers Targeted US Officials in Elaborate Social Media Attack Operation. Iranian threat actors, using more than a dozen fake personas on popular social networking sites, have been running a wide-spanning cyber espionage operation since 2011, according to cyber intelligence firm iSIGHT Partners.
The recently uncovered activity, which iSIGHT Partners calls NEWSCASTER, was a “brazen, complex multi-year cyber-espionage that used a low-tech approach to avoid traditional security defenses–exploiting social media and people who are often the ‘weakest link’ in the security chain.” Using the fake personas, including at least two (falsified) legitimate identities from leading news organizations, and young, attractive women, the attackers were supported by a fictitious news organization called NewsOnAir.org (Do Not Visit) and were successful in connecting or victimizing over 2,000 individuals.
Podcast: Inside the 'NEWSCASTER' Cyber Espionage Campaign Other victims targeted were in the U.K., Saudi Arabia, Iraq and also included vocal supporters of Israel. NEWSCASTER - An Iranian Threat Inside Social Media - iSIGHT Partners. On May 29th, iSIGHT Partners released a report focused on a new threat – dubbed NEWSCASTER – targeting the public and private sector in the U.S., Israel, UK and beyond using social media.
We believe the threat originates from Iran. Below you will find key details related to this disclosure. A full copy of the iSIGHT Partners report is available upon request by registering here. For any media related inquires on the NEWSCASTER Threat please contact Adrienne Reitz, newscaster@okco.com Here is what you need to know… What is the news? Iran : les cyber-espions utilisaient Facebook et un faux site d'infos. Le Parisien | 30 Mai 2014, 08h34 L'opération aurait commencé au moins en 2011. iSight Partners l'a nommée «Newscaster» (présentateur du journal télévisé), car elle repose en partie sur l'utilisation d'un faux site d'information : NewsOnAir.org.
Le but des pirates ? Pénétrer des réseaux informatiques militaires et gouvernementaux, voire y installer des programmes informatiques malveillants. Le moyen ?