

Scientists open a new window into quantum physics with superconductivity in LEDs. A team of University of Toronto physicists led by Alex Hayat has proposed a novel and efficient way to leverage the strange quantum physics phenomenon known as entanglement.
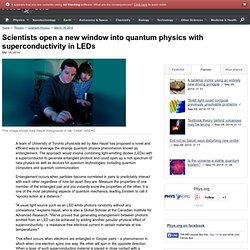
The approach would involve combining light-emitting diodes (LEDs) with a superconductor to generate entangled photons and could open up a rich spectrum of new physics as well as devices for quantum technologies, including quantum computers and quantum communication. Entanglement occurs when particles become correlated in pairs to predictably interact with each other regardless of how far apart they are. Measure the properties of one member of the entangled pair and you instantly know the properties of the other. Hardware Trick Could Keep Cloud Data Safe. One thing is certain in this day and age: Somewhere out there, somebody wants your data. So how do you make sure all of it stays protected, especially now that ever more computing is done in the cloud? At MIT, researchers say they’ve designed a chip that solves this problem. They presented it last June at the International Symposium on Computer Architecture , in Tel Aviv. Dubbed Ascend, the component hides the way CPUs request information in cloud servers, making it immensely difficult for attackers to glean information about the data stored there.
Such a hardware-reliant scheme is an unusual proposition in the realm of cloud security, which is dominated by software solutions. The researchers assume that sensitive data on cloud servers is already encrypted—typically the first line of defense when it comes to data security. What Ascend does instead is alter the pattern of memory-access events. Johns Hopkins University cryptography researcher Matthew D. The Future of Cryptography Is Outdated Nokia Phones?
The hidden champion of online privacy is the random number.
When you’re making a credit card purchase online or simply sending an email, you rely on encryption techniques that use long strings of random numbers to conceal your information. But there’s a big problem with this approach: True randomness is incredibly difficult to create digitally. Computers are not random. “It’s actually impossible for a computer, following a predefined algorithm, to generate a truly random number,” says Bruno Sanguinetti, as physicist at the University of Geneva in Switzerland. And any technique to try to get a machine to spit out a random number is duplicable, leaving room for someone to crack the code to the random number generator and get to your data. "Rather, if you want to generate proper random numbers, you must rely on some randomness that originates from the outside world,” Sanguinetti says. Paperweight, or Cryptographic Tool? Best Free Drive Encryption Utility. TrueCrypt Gizmo's Freeware award as the best product in its class!
Runs as a stand-alone program on a user's computer A seasoned, widely-used encyption program. Use TrueCrypt to either encrypt the Windows boot partition or the entire boot disk. TrueCrypt's open source status allows the all-important peer review of the source code required for a trustworthy encryption program. It takes some time to learn how to use TrueCrypt if you've never used any sort of encryption program before. 32 and 64 bit versions available Open source freeware A portable version of this product is available from the developer.
Windows 2000/2003/XP/Vista/7 Runs on Windows 8, but may not be compatible for full disk encryption; Mac OS X; Linux FREE CompuSec Pre boot access control. You won't be able to use standard methods for double-booting if you install this software. Unrestricted freeware There is no portable version of this product available. Encryption is Not Enough. A few facts Inconvenient fact #1 - Cryptography is harder than it looks: Not just any encryption program will do.
Most any competent programmer could grab the open-source code for a block cipher (cryptographic protocol) -- say AES -- and put together an encryption process to get from password entry to ciphertext. But there is a special Murphy's Law for budding cryptographers: Somewhere else in the naive coder's encryption process - key generation, random number generation, hash processes, etc. - there will almost certainly be one or more fatal flaws. A skilled hacker can often find and break process vulnerabilities without much effort. Best Free Encryption Utility for Cloud Storage. Cloudifile is a new cloud encryption entry from an established organization.
I have applied my criteria for encryption software, and while it is new I am comfortable including Cloudifile in this encryption category. Cloudifile is offered by Cloud Labs, which is a product spin-off of Apriorit. Apriorit has extensive experience in security projects that relate to a product like Cloudifile. Here's how it works: Cloudifile creates a new folder in Dropbox, and encrypts and moves the files you want to store in the cloud to that Dropbox folder. It also creates a virtual drive where you can access the files (when you are logged in). Tresorit is a significant entry in the "client plus cloud" encryption arena, with a free 5 GB plan. Tresorit support is comprehensive and well written, and they have added tutorials for all platforms. I've been using Tresorit for my most important data since September, 2013, and it has performed flawlessly.