

A TINY BIT about Cryptography. Bullrun - NSA planting backdoors into cryptography. National Cryptologic Museum. The National Cryptologic Museum is the National Security Agency's principal gateway to the public. It shares the Nation's, as well as NSA's, cryptologic legacy and place in world history. Located adjacent to NSA Headquarters, Ft. George G. Ellis. Elliptic curve cryptography. Elliptic curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields.
Elliptic curves are also used in several integer factorization algorithms that have applications in cryptography, such as Lenstra elliptic curve factorization. The use of elliptic curves in cryptography was suggested independently by Neal Koblitz[1] and Victor S. Miller[2] in 1985. Elliptic curve cryptography algorithms entered wide use in 2004 to 2005. Introduction[edit] The primary benefit promised by ECC is a smaller key size, reducing storage and transmission requirements, i.e. that an elliptic curve group could provide the same level of security afforded by an RSA-based system with a large modulus and correspondingly larger key – e.g., a 256-bit ECC public key should provide comparable security to a 3072-bit RSA public key (see key sizes below). The U.S. Cryptographic schemes[edit] with an elliptic curve: Implementation considerations[edit] Cryptography. 6.5 \ The Navajo Code Talkers. Navajo Code Talkers' Dictionary. WW II Codes and Ciphers. Imperial War Museums.
Bletchley Park. Bletchley Park - Virtual Tour. The Code Book. When I wrote my first book, Fermat’s Last Theorem, I made a passing reference to the mathematics of cryptography.
Cryptography. When I wrote my first book, Fermat’s Last Theorem, I made a passing reference to the mathematics of cryptography.
The Enigma cipher machine. 158,962,555,217,826,360,000 - Numberphile. Alan Turing Scrapbook - The Enigma War. Alan Turing and the Battle of the Atlantic The Bombe was used with success from the summer of 1940 onwards, to break messages enciphered on the simpler Enigma system used by the German Air Force.
But the most important messages were those to and from the U-boat fleet, and these were enciphered on a much more secure Enigma system. Alan Turing took on this problem, going against the prevailing view that it would prove unbreakable. Although he had crucial new ideas at the end of 1939, not much practical progress could be made. In 1940 they were desperate. See the October 1940 Operation Ruthless plan devised by Ian Fleming, later the creator of 'James Bond', to capture such information for Turing's work. Flaw in the Enigma Code - Numberphile. Research, education & online exhibitions. A basic flaw in the design of Enigma was that no letter of the alphabet could ever be represented by itself once enciphered - a could never be a, z could never be z.

Together with errors in sent messages and the German habit of using standard phrases at the start of each communication, this allowed cryptanalysts to establish informed ‘guesses’. History - Enigma (pictures, video, facts & news) Allies capture German Enigma machine, May 9, 1941. How Enigma Machines Work. The underlying principle of an Enigma machine cipher is that of letter substitution, meaning that each letter of our plaintext (undeciphered message) is substituted by another letter.

The Enigma machine is an electro-mechanical device. It is mechanically operated, with an electric signal passed through wires and various mechanical parts. The easiest way to explain the mechanics is to follow the journey of a single letter from keyboard to lampboard. The diagram below (figure 1) shows the path the signal takes from pressing the letter 'T' on the keyboard to the 'G' lamp lighting up. Figure 1: How one letter is changed into another letter at each stage as it passes through an Enigma machine.
Keyboard. Enigma Simulator. This software is an exact simulation of the 3-rotor Wehrmacht (Heer and Luftwaffe) Enigma, the 3-rotor Kriegsmarine M3, also called Funkschlussel M, and the famous 4-rotor Kriegmarine M4 Enigma cipher machine, used during World War II from 1939 until 1945.
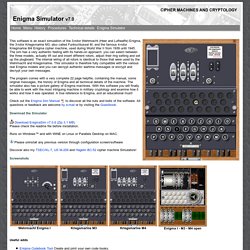
The sim has a very authentic feeling with its hands-on approach: you can select between the three models, actually lift out and insert different rotors, adjust their ring setting and set up the plugboard. The internal wiring of all rotors is identical to those that were used by the Wehrmacht and Kriegsmarine. This simulator is therefore fully compatible with the various real Enigma models and you can decrypt authentic wartime messages or encrypt and decrypt your own messages. The program comes with a very complete 22 page helpfile, containing the manual, some original messages, the history of Enigma and all technical details of the machine. The simulator also has a picture gallery of Enigma machines.
Introduction to Cryptography Basic Principles. Whenever we come across the term cryptography, the first thing and probably the only thing that comes to our mind is private communication through encryption.

There is more to cryptography than just encryption. In this article, we will try to learn the basics of cryptography. The Basic Principles 1. Crypto.