

Public-key cryptography. An unpredictable (typically large and random) number is used to begin generation of an acceptable pair of keys suitable for use by an asymmetric key algorithm.
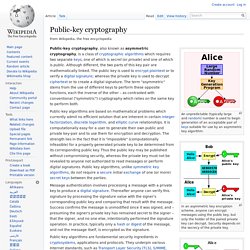
In an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of the private key. In the Diffie–Hellman key exchange scheme, each party generates a public/private key pair and distributes the public key. After obtaining an authentic copy of each other's public keys, Alice and Bob can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher. Cryptography. Cryptography Breakthrough Could Make Software Unhackable. As a graduate student at the Massachusetts Institute of Technology in 1996, Amit Sahai was fascinated by the strange notion of a “zero-knowledge” proof, a type of mathematical protocol for convincing someone that something is true without revealing any details of why it is true.
As Sahai mulled over this counterintuitive concept, it led him to consider an even more daring notion: What if it were possible to mask the inner workings not just of a proof, but of a computer program, so that people could use the program without being able to figure out how it worked? The idea of “obfuscating” a program had been around for decades, but no one had ever developed a rigorous mathematical framework for the concept, let alone created an unassailable obfuscation scheme.
Over the years, commercial software companies have engineered various techniques for garbling a computer program so that it will be harder to understand while still performing the same function. Too Powerful to Exist. A (relatively easy to understand) primer on elliptic curve cryptography. Author Nick Sullivan worked for six years at Apple on many of its most important cryptography efforts before recently joining CloudFlare, where he is a systems engineer.
He has a degree in mathematics from the University of Waterloo and a Masters in computer science with a concentration in cryptography from the University of Calgary. This post was originally written for the CloudFlare blog and has been lightly edited to appear on Ars. Readers are reminded that elliptic curve cryptography is a set of algorithms for encrypting and decrypting data and exchanging cryptographic keys. Dual_EC_DRBG, the cryptographic standard suspected of containing a backdoor engineered by the National Security Agency, is a function that uses elliptic curve mathematics to generate a series of random-looking numbers from a seed.
This primer comes two months after internationally recognized cryptographers called on peers around the world to adopt ECC to avert a possible "cryptopocalypse. " Cryptography - Wikibooks, open books for an open world. Cryptography From Wikibooks, open books for an open world Jump to: navigation, search Welcome to Cryptography, the study of transforming information in order to make it secure from unintended recipients or use.
Part I: Introducing Cryptography Part II: Designing Cryptosystems Part III: Cryptanalysis Part IV: Using Cryptosystems. Journey into cryptography. Cryptography Links. An Overview of Cryptography. As an aside, the AES selection process managed by NIST was very public.

A similar project, the New European Schemes for Signatures, Integrity and Encryption (NESSIE), was designed as an independent project meant to augment the work of NIST by putting out an open call for new cryptographic primitives. NESSIE ran from about 2000-2003. While several new algorithms were found during the NESSIE process, no new stream cipher survived cryptanalysis. As a result, the ECRYPT Stream Cipher Project (eSTREAM) was created, which has approved a number of new stream ciphers for both software and hardware implementation.
Similar — but different — is the Japanese Government Cryptography Research and Evaluation Committees (CRYPTREC) efforts to evaluate algorithms submitted for government and industry applications. CAST-128/256: CAST-128, described in Request for Comments (RFC) 2144, is a DES-like substitution-permutation crypto algorithm, employing a 128-bit key operating on a 64-bit block. 3.3. A Brief History of Cryptography. Cryptology is a young science.

Though it has been used for thousands of years to hide secret messages, systematic study of cryptology as a science (and perhaps an art) just started around one hundred years ago. The first known evidence of the use of cryptography (in some form) was found in an inscription carved around 1900 BC, in the main chamber of the tomb of the nobleman Khnumhotep II, in Egypt. The scribe used some unusual hieroglyphic symbols here and there in place of more ordinary ones. The purpose was not to hide the message but perhaps to change its form in a way which would make it appear dignified. Though the inscription was not a form of secret writing, but incorporated some sort of transformation of the original text, and is the oldest known text to do so.
Fast forwarding to around 100 BC, Julius Caesar was known to use a form of encryption to convey secret messages to his army generals posted in the war front. To conclude, history teaches us: