

Tor (anonymity network) Tor (previously an acronym for The Onion Router)[4] is free software for enabling online anonymity and censorship resistance.
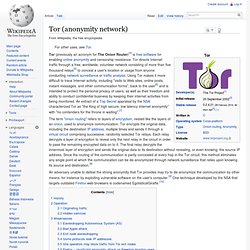
Tor directs Internet traffic through a free, worldwide, volunteer network consisting of more than five thousand relays[5] to conceal a user's location or usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity, including "visits to Web sites, online posts, instant messages, and other communication forms", back to the user[6] and is intended to protect the personal privacy of users, as well as their freedom and ability to conduct confidential business by keeping their internet activities from being monitored. An extract of a Top Secret appraisal by the NSA characterized Tor as "the King of high secure, low latency Internet anonymity" with "no contenders for the throne in waiting".[7] Alice's Tor client picks a random path to destination server Steven J.
Law enforcement seized Tor nodes and may have run some of its own. In a blog post written on November 9, Tor Project director Andrew Lewman went over the possible ways that over 400 hidden services on dozens of servers were located by law enforcement during Operation Onymous.

While some of the servers were related to criminal activity (such as Silk Road 2.0), at least some of the servers were not—including several that were acting as infrastructure for Tor’s anonymizing network. And the only answer Lewman could currently offer as to how the sites were exposed was “We don’t know.” That's unnerving not just to people like the operators of the many illicit sites that were taken down by Operation Onymous, it’s also of concern to anyone using Tor to evade surveillance by more oppressive governments. Activists, dissidents, and journalists, for example, all rely on the same Tor infrastructure. Again, some of the sites taken down may not have been criminal at all. Rogue nodes snoop on TOR traffic. Researchers have uncovered more evidence that the TOR anonymiser network is being misused by hackers, and quite likely government intelligence agencies.
TOR (The Onion Router) is a network of proxy nodes set up to provide some privacy and anonymity to its users. Originally backed by the US Naval Research Laboratory, TOR became an Electronic Frontier Foundation (EFF) project three years ago. The system provides a way for whistleblowers and human rights workers to exchange information with journalists, among other things.
The system also provides plenty of scope for mischief. The presence of rogue nodes on the network was recently highlighted by security researcher Dan Egerstad, who controversially posted details of login credentials of about 1,000 email addresses, including at least 100 accounts belonging to foreign embassies, obtained by listening to traffic passing through five exit nodes under his control. Tor Exit Nodes Mapped and Located. Tor Exit Nodes are the gateways where encrypted Tor traffic hits the Internet.
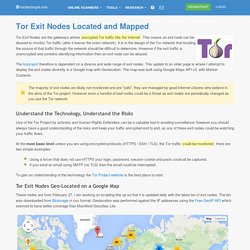
This means an exit node can be abused to monitor Tor traffic (after it leaves the onion network). It is in the design of the Tor network that locating the source of that traffic through the network should be difficult to determine. However if the exit traffic is unencrypted and contains identifying information then an exit node can be abused. The torproject therefore is dependent on a diverse and wide range of exit nodes. This update to an older page is where I attempt to display the exit nodes diversity in a Google map with Geolocation.
Chaos Computer Club bolsters NSA spying complaint with Tor snooping evidence. The German Chaos Computer Club said Wednesday that it has added to its legal complaint about U.S. spying on German citizens evidence that the NSA allegedly snooped on at least one of its Tor servers.
The CCC filed a complaint with Germany’s federal prosecutor, Harald Range, in February, demanding an investigation into the German government’s alleged involvement in the U.S. National Security Agency’s mass surveillance of German citizens. However, while Range started an investigation into the alleged tapping of Merkel’s phone by the NSA in June, he said there wasn’t enough evidence to start a similar investigation into the widely reported mass surveillance of German citizens. FBI shuts alleged online drug marketplace, Silk Road. After Silk Road Raid, the Dark Net Is 'Darker Than Ever'
has done little to slow the drug, weapon, and stolen identity trade on the dark net—in fact, shutting down the relatively tame Silk Road created a vacuum that was immediately filled with sites that are "more dangerous in their nature," according to a new analysis by a group called the Digital Citizens Alliance.
Since the early November raid that shut down Silk Road, BlueSky Marketplace, Cannabis Road, Alpaca Marketplace, and several other dark net drug markets, the overall number of drug listings available on the dark net is down by roughly 30 percent. That might seem like a win for the FBI, but the overall number of drug listings on the dark net is more than 32,000—so it's still not exactly very difficult to trade Bitcoin for illegal drugs. What's more, new marketplaces have obviously popped up, with many of them willing to sell things that Silk Road wasn't willing to touch, such as weapons and stolen identities.
Image: Digital Citizens Alliance.