

How I used Heartbleed to steal a site’s private crypto key. Hacking the hospital: medical devices have terrible default security. How Heartbleed transformed HTTPS security into the stuff of absurdist theater. Flying the world's fastest plane: Behind the stick of the SR-71. Edward Snowden's magnificent testimony to the EU. NSA whistleblower Edward Snowden has submitted written testimony [PDF] to an EU committee investigating mass surveillance.

Ron Paul Launches Snowden Clemency Petition. Credit: Gage Skidmore/wikimedia Today, it was reported that former Rep.
Ron Paul (R-Texas) launched a petition calling for NSA whistle-blower Edward Snowden to be granted clemency. Key management - Is using a numbers station to transmit a one-time-pad as key actually insecure. "Pseudo random generators are quick but predictable": well, that's true only in an ethereal, mathematical sense.
In practice, if your PRNG is cryptographically secure and seeded with some initial randomness of large enough entropy (128 bits are enough), then it won't be predictable. However, if a PRNG is involved, this is not true "One-Time Pad" but a mere "stream cipher". OTP is a nice theoretical toy but it has no practical advantage over a properly used stream cipher. For some reason, a lot of people have fantasies of OTP being the ultimate answer for the Real World, and this leads to many misguided designs. US drones could be killing the wrong people because of metadata errors. The Intercept, the "fearless, adversarial journalism" venture launched by Pierre Omidyar's First Look Media, launched with a big boom today.
Lead story on the site right now, which is https by default (and straining under launch day load at the moment) explores "The NSA’s Secret Role in the U.S. Assassination Program. " The Intercept will initially focus on NSA stories based on documents provided by Edward Snowden, and this is one such story. "The National Security Agency is using complex analysis of electronic surveillance, rather than human intelligence, as the primary method to locate targets for lethal drone strikes," Jeremy Scahill and Glenn Greenwald report, "An unreliable tactic that results in the deaths of innocent or unidentified people. " Sophisticated Spy Tool 'The Mask' Rages Undetected for 7 Years. Image: Getty PUNTA CANA, Dominican Republic – Researchers have uncovered a sophisticated cyber spying operation that has been alive since at least 2007 and uses techniques and code that surpass any nation-state spyware previously spotted in the wild.
The attack, dubbed “The Mask” by the researchers at Kaspersky Lab in Russia who discovered it, targeted government agencies and diplomatic offices and embassies, before it was dismantled last month. It also targeted companies in the oil, gas and energy industries as well as research organizations and activists. Kaspersky uncovered at least 380 victims in more than two dozen countries, with the majority of the targets in Morocco and Brazil.
New surveillance technology can track everyone in an area for several hours at a time. DAYTON, Ohio — Shooter and victim were just a pair of pixels, dark specks on a gray streetscape.
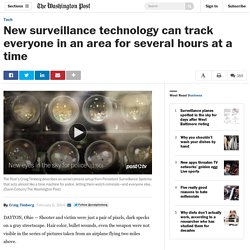
Hair color, bullet wounds, even the weapon were not visible in the series of pictures taken from an airplane flying two miles above. But what the images revealed — to a degree impossible just a few years ago — was location, mapped over time. Second by second, they showed a gang assembling, blocking off access points, sending the shooter to meet his target and taking flight after the body hit the pavement. When the report reached police, it included a picture of the blue stucco building into which the killer ultimately retreated, at last beyond the view of the powerful camera overhead.
New documents: NSA provided 2-3 daily “tips” to FBI for at least 3 years. According to newly declassified court orders from the Foreign Intelligence Surveillance Court (FISC), the National Security Agency was (and may still be) tipping off the FBI at least two to three times per day going back at least to 2006.
Hours after President Barack Obama finished his speech last Friday on proposed intelligence and surveillance reforms, the Office of the Director of National Intelligence (ODNI) declassified a number of documents from the nation’s most secretive court. Data Scraping Highlights Risks Of Image Theft Online. TORONTO - When a photo of the late Rehtaeh Parsons was used for a dating website's advertisement on Facebook last year, the callous misappropriation of her image shocked those who saw it.
It should've also been seen as a warning, say privacy experts. Having a photo stolen and reposted elsewhere online could just as easily happen to any of the millions of Canadians who regularly post images to the web without a second thought. "Many of us are sharing images without considering how others may use them or how we may lose control," says Marian Merritt, the Internet safety advocate for security software maker Norton. N.S.A. Devises Radio Pathway Into Computers. Photo WASHINGTON — The National Security Agency has implanted software in nearly 100,000 computers around the world that allows the United States to conduct surveillance on those machines and can also create a digital highway for launching cyberattacks.
While most of the software is inserted by gaining access to computer networks, the N.S.A. has increasingly made use of a secret technology that enables it to enter and alter data in computers even if they are not connected to the Internet, according to N.S.A. documents, computer experts and American officials. Coalition to fight mass Internet surveillance declares global day of action, Feb 11. A broad coalition of organizations -- including Boing Boing -- have joined forces to declare February 11 a day of action in memory of Aaron Swartz and against NSA Internet spying and mass surveillance.
Just as we did with the SOPA fight, we're asking people who care about this to make their own personal expressions of resistance, and take the case for caring about this and fighting back to the people closest to them. Each of us knows the arguments that will convince our friends and loved ones. The Day We Fight Back sets out a number of ways you can participate, small and large. This is a fight we can win. David Segal, executive director of Demand Progress, which he co-founded with Swartz, said: "Today the greatest threat to a free Internet, and broader free society, is the National Security Agency's mass spying regime.
Oh Great, the NSA's Tracking Your Cell Phone's Every Move, Too. It's Insanely Cheap for Cops to Track Your Cell Phone. Who Will Dispose Of Your Porn And Sex Toys After You Die? Researchers warn of new, meaner ransomware with unbreakable crypto. Security researchers have uncovered evidence of a new piece of malware that may be able to take gigabytes' worth of data hostage unless end users pay a ransom. Discussions of the new malware, alternately dubbed PrisonLocker and PowerLocker, have been occurring on underground crime forums since November, according to a blog post published Friday by Malware Must Die, a group of researchers dedicated to fighting online crime. The malware appears to be inspired by CryptoLocker, the malicious software that wreaked havoc in October when it used uncrackable encryption to lock up victims' computer files until they paid hundreds of dollars for the decryption key.
You'll Never Guess Where This FBI Agent Left a Secret Interrogation Manual. In a lapse that national security experts call baffling, a high-ranking FBI agent filed a sensitive internal manual detailing the bureau's secret interrogation procedures with the Library of Congress, where anyone with a library card can read it. Congress: Are you spying on us? NSA: We don't spy on you except to the extent that we spy on everydamnbody.
When Senator Bernie Sanders asked the NSA whether it was spying on Congress, he was very clear: "gathering metadata on calls made from official or personal phones, content from websites visited or emails sent, or collecting any other data from a third party not made available to the general public in the regular course of business. " When the NSA answered, it was a lot less clear: "Members of Congress have the same privacy protections as all US persons. " So, we'll take that as a yes, then? FBI agent tries to copyright super-secret torture manual, inadvertently makes it public. Edward Snowden declares victory: "I defected from the government to the public" Edward Snowden granted a 14-hour interview to the Washington Post, commenting on his relationship to the NSA, Russia, and the USA.
The "screw you" effect and other perils of informed volunteers. The NSA's Trying to Build a Quantum Computer That Cracks All Encryption. The NSA Hated Civilian Encrypted Data Way Back in the 1970s. The NSA's Trying to Build a Quantum Computer That Cracks All Encryption. RSA’s Deal With The NSA Reflects A General Mistrust.
Apple Says It Has Never Worked With NSA To Create iPhone Backdoors, Is Unaware Of Alleged DROPOUTJEEP Snooping Program. The badBIOS Analysis Is Wrong. at RootWyrm's Corner. November 1st, 2013 by Phillip Jaenke. Meet “badBIOS,” the mysterious Mac and PC malware that jumps airgaps. Three years ago, security consultant Dragos Ruiu was in his lab when he noticed something highly unusual: his MacBook Air, on which he had just installed a fresh copy of OS X, spontaneously updated the firmware that helps it boot. Stranger still, when Ruiu then tried to boot the machine off a CD ROM, it refused. He also found that the machine could delete data and undo configuration changes with no prompting.
Your USB cable, the spy: Inside the NSA’s catalog of surveillance magic. The National Security Agency’s sophisticated hacking operations go way beyond using software vulnerabilities to gain access to targeted systems. NSA malware turns your iPhone into a spy device, obliterating your privacy. According to documents reported on by the German newspaper Der Spiegel, the NSA has a fool-proof and covert method of remotely installing malware onto iPhones. Senator Ron Wyden has warned publicly that the NSA has these capabilities, though he didn't name Apple or iPhone specifically. Previously, Der Spiegel reported that the NSA internally referred to iPhone users as "zombies" who "pay for their own surveillance.
" The newly disclosed malware tool, which the agency's Tailored Access Operations division calls DROPOUTJEEP, enables the NSA to both extract and implant information onto the Apple smartphones. New Leaks Detail How The NSA’s ‘TAO’ And ‘ANT’ Units Spy On Devices, Global Networks. New leaks emerged today in Germany’s Der Spiegel newspaper about the scope of electronic surveillance conducted by the United States’ National Security Agency. Report: NSA Intercepting Laptops Ordered Online, Installing Spyware. The most Kafkaesque paragraph from today’s NSA ruling. Earlier today a U.S. District Court judge, Justice William Pauley, dismissed an American Civil Liberties Union (ACLU) lawsuit alleging that the National Security Agency's phone records program was unconstitutional, based primarily on his interpretation of the 1979 Smith v. Maryland Supreme Court ruling. 53°44'N 0°26'W. Number Stations. Jochen Kopf. Asian comments. Radio jamming in China. Crypto Machine Menu Page.
OLFP ( One Time Figure Pads) and OTLP (One Time Letter Pads) Microsoft, Google, Apple call for end to NSA’s bulk data collection. New US spy satellite features world-devouring octopus. Report: NSA Considered Revealing Porn Habits To Discredit Radicals. The Mystery of the Creepiest Television Hack. UK spies were terrified that the willing cooperation of telcos would get out; understood they were breaking the law.
US bugged Merkel's phone from 2002 until 2013, report claims.