

Android-based Pwn Phone is prepared to do evil for your network’s own good. Mobile technology has made it possible for people to do an amazing amount with tablets and smartphones within the workplace—including hacking the living daylights out of the corporate network and other people’s devices.
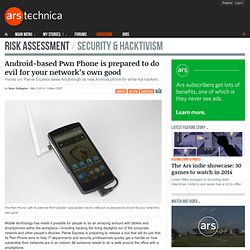
Pwnie Express is preparing to release a tool that will do just that. Its Pwn Phone aims to help IT departments and security professionals quickly get a handle on how vulnerable their networks are in an instant. All someone needs to do is walk around the office with a smartphone. Pwnie Express’ Kevin Reilly gave Ars a personal walk-through of the latest Pwn Phone, the second generation of the company’s mobile penetration testing platform. While the 2012 first-generation Pwn Phone was based on the Nokia N900 and its Maemo 5 Linux-based operating system, the new phone is based on LG Nexus 5 phone hardware.
Info.publicintelligence.net/NCCIC-DDoS-Guide. Building a Mesh Networked Conference Badge. Sniffing Vending Machine Buses. Sniping 2.4GHz. How Heartbleed transformed HTTPS security into the stuff of absurdist theater. If you want to protect yourself against the 500,000 or so HTTPS certificates that may have been compromised by the catastrophic Heartbleed bug, don't count on the revocation mechanism built-in to your browser.
It doesn't do what its creators designed it to do, and switching it on makes you no more secure than leaving it off, one of the Internet's most respected cryptography engineers said over the weekend. For years, people have characterized the ineffectiveness of the online certificate status protocol (OCSP) as Exhibit A in the case that the Internet's secure sockets layer and transport layer security (TLS) protocols are hopelessly broken. Until now, no one paid much attention. System performance benchmark. Pentest lab vulnerable servers-applications list. This article is translated to Serbo-Croatian language by Jovana Milutinovich from Webhostinggeeks.com.
Photo by: extraketchup In this post I’m going to present some useful resources to learn about penetration testing and where to use exploitation tools and techniques in a safe and legal environment. Nikto v2.1.5 - The Manual. CIRT.net. How to mitigate tracking risks: wrap your phone in tinfoil, quit Google. WASHINGTON, DC—When author Julia Angwin has to post a photo of herself online, she now prefers to use a stencil image of her face in order to avoid detection by facial recognition software.
Heartbleed Explanation. Heartbleed Bug. A Real Malware In A Mouse. Malware In A Mouse. How the NSA plans to automatically infect "millions" of computers with spyware. A new Snowden leak, detailed in a long, fascinating piece in The Intercept, explains the NSA's TURBINE initiative, intended to automate malicious software infections.
These infections -- called "implants" in spy jargon -- have historically been carried out on a narrow, surgical scale, targeted at people of demonstrated value to spies, due to the expense and difficulty of arranging the attacks. But TURBINE, which was carried out with other "Five Eyes" spy agencies as part of the NSA's $67.6M "Owning the Net" plan, is intended to automate the infection process, allowing for "millions" of infections at once.
Everything You Need to Know About the New Privacy-Focused Smartphones. Can this $70 dongle stem the epidemic of password breaches? Security researchers have developed a password storage system that uses inexpensive hardware to prevent the cracking of passwords—even the most common and weak ones such as "123456," "password," and "letmein.
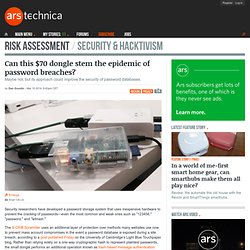
" The S-CRIB Scrambler uses an additional layer of protection over methods many websites use now to prevent mass account compromises in the event a password database is exposed during a site breach, according to a post published Friday on the University of Cambridge's Light Blue Touchpaper blog. Rather than relying solely on a one-way cryptographic hash to represent plaintext passwords, the small dongle performs an additional operation known as hash-based message authentication code (HMAC).
The secret 10 32-character key used to generate the HMAC resides solely on the dongle. Because it's not included in password tables that are stored on servers, the key could remain secret even in the event of a major security breach. How_to_use_scramble_scrib [Documentation] S-CRIB Scrambler is our latest product (January 2014).
![how_to_use_scramble_scrib [Documentation]](http://cdn.pearltrees.com/s/pic/th/scramble-scrib-documentation-79660003)
It helps protect user passwords stored on servers by scrambling them with a secret key that is only present in a hardware device connected or used by servers. You can actually purchase S-CRIB Scrambler and become an early adopter. We would love to test the concept and implementation in real systems. Edward Snowden's magnificent testimony to the EU. NSA whistleblower Edward Snowden has submitted written testimony [PDF] to an EU committee investigating mass surveillance.

Glyn Moody's Techdirt post gives a great tl;dr summary of the document, but you should really read it for yourself. It's ten single-spaced pages, but Snowden turns out to be an extremely talented writer who beautifully lays out his arguments, managing the trick of being dispassionate while simultaneously conveying the import of his subject matter. Snowden makes the point that his testimony doesn't disclose anything that the press hasn't already published, but there's been so much that it's worth reviewing some of it. He directs our attention to something I'd missed: the NSA's Foreign Affairs Division (FAD) spends an extraordinary amount of time lobbying EU nations (and other countries) to change their laws so that the NSA can legally spy on everyone in the country.
Speedtest.net by Ookla - The Global Broadband Speed Test. PRISM : les slides de la NSA revues et corrigées ! Le programme de surveillance PRISM fait scandale depuis plusieurs jours.
Suite à la publication de certaines slides provenant d’une présentation PowerPoint de la NSA, la presse s’est emparée de l’affaire. Mais un aspect reste assez peu évoqué : ces pages de présentation sont absolument hideuses. Un designer français, Emiland De Cubber, a décidé d’agir. How Covert Agents Infiltrate the Internet to Manipulate, Deceive, and Destroy Reputations. One of the many pressing stories that remains to be told from the Snowden archive is how western intelligence agencies are attempting to manipulate and control online discourse with extreme tactics of deception and reputation-destruction.
It’s time to tell a chunk of that story, complete with the relevant documents. Over the last several weeks, I worked with NBC News to publish a series of articles about “dirty trick” tactics used by GCHQ’s previously secret unit, JTRIG (Joint Threat Research Intelligence Group). These were based on four classified GCHQ documents presented to the NSA and the other three partners in the English-speaking “Five Eyes” alliance.
Today, we at the Intercept are publishing another new JTRIG document, in full, entitled “The Art of Deception: Training for Online Covert Operations.” Other tactics aimed at individuals are listed here, under the revealing title “discredit a target”: TrustyCon - Live from San Francisco. Security Features of the HTTP Headers for soccerway.com. List of Safari User Agent Strings. Complete List of iOS User-Agent Strings. Bemasher/rtlamr. Italy defined The National Strategic Framework for cyberspace security. The Italian Government has published his cyber strategy, the Presidency of Council of Ministers has issued the “National Strategic Framework for cyberspace security”, it is an important document that for the first time reveals the cyber strategy for the next biennium.
The document propose in a first part an overview of the evolving trends of the cyber threat making reference to the vulnerabilities of the National ICT Infrastructures, in the second chapter it exposes tools and procedures to improve national cyber defence capabilities. Web Semantics: Cyberspace security glossary.
*It’s from the Italian government in their recent document “National Strategic Framework for Cyberspace Security.” This certainly is written in some excellent, technically-aware English. The English in this Italian document is far more lucid than most English that comes out of Brussels. L'agence de cyberdéfense française montre ses muscles. Le Monde.fr | • Mis à jour le | Par Martin Untersinger. GPS Tracking Via The Cloud. Python for Hackers - Networkers Primer (Sockets, Webserver Scapy!)
Cryptography Breakthrough Could Make Software Unhackable - Wired Science. As a graduate student at the Massachusetts Institute of Technology in 1996, Amit Sahai was fascinated by the strange notion of a “zero-knowledge” proof, a type of mathematical protocol for convincing someone that something is true without revealing any details of why it is true. As Sahai mulled over this counterintuitive concept, it led him to consider an even more daring notion: What if it were possible to mask the inner workings not just of a proof, but of a computer program, so that people could use the program without being able to figure out how it worked?
The idea of “obfuscating” a program had been around for decades, but no one had ever developed a rigorous mathematical framework for the concept, let alone created an unassailable obfuscation scheme. Over the years, commercial software companies have engineered various techniques for garbling a computer program so that it will be harder to understand while still performing the same function. Too Powerful to Exist. Meet Mask, possibly the most sophisticated malware campaign ever seen. Calling it the most sophisticated malware-driven espionage campaign ever discovered, researchers said they have uncovered an attack dating back to at least 2007 that infected computers running the Windows, OS X, and Linux operating systems of 380 victims in 31 countries. The "Mask" campaign, which gets its name from a string of text found in one of the malware samples, includes a variety of components used to siphon encryption keys, key strokes, Skype conversations, and other types of sensitive data off infected computers.
There is also evidence that the Spanish-speaking attackers had malware that ran on devices running both Apple's iOS and Google's Android mobile operating systems. Victims include government agencies, embassies, research institutions, private equity firms, activists, energy companies, and companies in other industries. The attackers relied on highly targeted spear phishing e-mails to lure targeted individuals to malicious websites.
Dark Patterns - User Interfaces Designed to Trick People. The Two Component Random Number Generator. First there were CAPTCHAs, now there are GOTCHAs. Luis von Ahn and colleagues developed CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) in early 2000 to help fight against computer-generated spam. The test requires users to type in letters from a distorted image to prove that they're human. This system worked great for years, but as with many things on the Internet, there's always a hacker who wants to break the system. Nmap: beyond the basics. You probably have used nmap before, but did you know there are plenty of cool options to spice up your scanning sessions? Umit Project - Wiki - Umit Project. RadialNet.
How to trace MAC address. YAMAS for BackTrack 5 - Demonstration of how to sniff credentials. Notification : échec de DNS. How to: Man in the middle Attacks with Backtrack 5. How to: Man in the middle Attacks with Backtrack 5. UberHarvest Backtrack 5R3. Backtrack 5 - Maltego. Pour surfer anonymement et sans referrer ... Stolen Camera Finder - find your photos, find your camera. A (Relatively Easy To Understand) Primer on Elliptic Curve Cryptography. Elliptic Curve Cryptography (ECC) is one of the most powerful but least understood types of cryptography in wide use today. SoX - Sound eXchange. Baudline signal analyzer - FFT spectrogram. Www.dni.gov/files/documents/Intelligence Reports/2014 WWTA SFR_SSCI_29_Jan. Senior U.S. spies warn of future security threats. Hacking Snapchat's people verification in less than 100 lines. StevenHickson/FindTheGhost.
Chrome Bugs Lets Sites Listen to Your Private Conversations. Speech recognition hack turns Google Chrome into advanced bugging device. Users of Google's Chrome browser are vulnerable to attacks that allow malicious websites to use a computer microphone to surreptitiously eavesdrop on private conversations for extended periods of time, an expert in speech recognition said. The attack requires an end user to click on a button giving the website permission to access the microphone.
Most of the time, Chrome will respond by placing a blinking red light in the corresponding browser tab and putting a camera icon in the address bar—both indicating that the website is receiving a live audio feed from the visitor. Dynamic Internet Technology, Inc. Scientists detect “spoiled onions” trying to sabotage Tor privacy network. Computer scientists have identified almost two dozen computers that were actively working to sabotage the Tor privacy network by carrying out attacks that can degrade encrypted connections between end users and the websites or servers they visit.
Www.mindcert.com/resources/MindCert_Nmap_MindMap.pdf. Metasploit/MeterpreterClient. User Datagram Protocol. Analyzing UDP usage in Internet traffic. Home - GSMK. Transport Layer Security. Looking for Open Source Tripwire? Appelbaum: ‘Scary’ NSA will spy on you – every which way they can. Appelbaum: ‘Scary’ NSA will spy on you – every which way they can.
To Protect And Infect Part 2 (Jacob Applebaum ) Confidentialité et anonymat, pour tous et partout. To Protect And Infect Part 2 (Jacob Applebaum ) FIC2014 - Forum International de la Cybersécurité - OpenVAS - OpenVAS - Open Vulnerability Assessment System. NSA Hackers Get the 'Ungettable' With Rich Catalog of Custom Tools. NSA’s ANT Division Catalog of Exploits for Nearly Every Major Software/Hardware/Firmware. Bitmail, encrypted friend to friend email without central server. One year review of anonymous email service Countermail. Backdoor_description. Use Glitter Nail Polish to Make Your Laptop Tamper-Proof. Adobe credentials and the serious insecurity of password hints.
Searching the Snapchat data breach with “Have I been pwned?” Greyhats expose 4.5 million Snapchat phone numbers using “theoretical” hack (updated) How the NSA (may have) put a backdoor in RSA’s cryptography: A technical primer. Vulnerability assessment tools group test. Pirate Bay uploads up by 50% in 2013. Your USB cable, the spy: Inside the NSA’s catalog of surveillance magic. Notification : sécurité - risque lié aux programmes malveillants. Snapchat exploit may let hackers connect names and phone numbers in bulk. Spying on my brother tutorial. Backtrack 5 R2 - Setup a Backdoor. Backtrack 5 R2 - Setup a Backdoor.
Using Nmap & Zenmap on Backtrack 5 R1. Hackers who breached php.net exposed visitors to highly unusual malware. New attack steals e-mail decryption keys by capturing computer sounds. What a successful exploit of a Linux server looks like. How to encrypt your cloud storage for free. Create a Hidden Encrypted Volume on Your Computer to Hide Sensitive Data When You're Forced to Decrypt Your Machine. Raspberry Pi bot tracks hacker posts to vacuum up passwords and more.