

Cryptography - Windows 7 Password Hash Security. List of Rainbow Tables. This page lists the rainbow tables we generated.
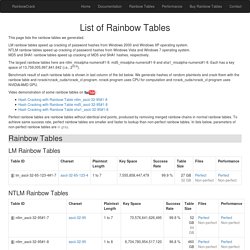
LM rainbow tables speed up cracking of password hashes from Windows 2000 and Windows XP operating system. NTLM rainbow tables speed up cracking of password hashes from Windows Vista and Windows 7 operating system. MD5 and SHA1 rainbow tables speed up cracking of MD5 and SHA1 hashes, respectively. The largest rainbow tables here are ntlm_mixalpha-numeric#1-9, md5_mixalpha-numeric#1-9 and sha1_mixalpha-numeric#1-9. Each has a key space of 13,759,005,997,841,642 (i.e., 253.6). Benchmark result of each rainbow table is shown in last column of the list below.
Free Rainbow Tables » Distributed Rainbow Table Generation » LM, NTLM, MD5, SHA1, HALFLMCHALL, MSCACHE. Labs. Group Policy for Beginners. If you are an IT pro who has never used Group Policy to control computer configurations, this white paper is for you.
Group Policy is the essential way that most organizations enforce settings on their computers. It is flexible enough for even the most complex scenarios; however, the essential features are easy to use in simple scenarios, which are more common. Group Policy. How-To Geek - For Geeks, By Geeks. HTG Explains: The Difference Between WEP, WPA, and WPA2 Wireless Encryption (and Why It Matters) Even if you know you need to secure your Wi-Fi network (and have already done so), you probably find all the encryption acronyms a little bit puzzling.
Read on as we highlight the differences between encryption standards like WEP, WPA, and WPA2–and why it matters which acronym you slap on your home Wi-Fi network. What Does It Matter? You did what you were told to do, you logged into your router after you purchased it and plugged it in for the first time, and set a password. What does it matter what the little acronym next to the security encryption standard you chose was? As it turns out, it matters a whole lot: as is the case with all encryption standards, increasing computer power and exposed vulnerabilities have rendered older standards at risk. WEP, WPA, and WPA2: Wi-Fi Security Through the Ages Since the late 1990s, Wi-Fi security algorithms have undergone multiple upgrades with outright depreciation of older algorithms and significant revision to newer algorithms. InfoSec Handlers Diary Blog - Hashing Passwords. After talking about SQL Injection, this is the second part of the mini series to help you protect yourself from simple persistent attacks as we have seen them in the last couple months.
A common MO employed in these attacks is to steal passwords from a database via sql injection. Later, the attacker will try to use these passwords to break into other sites for which users may choose the same password. Of course, part of the problem is password reuse. But for now, we will focus on the hashing of passwords to make it harder for an attacker to retrieve a users plain text password. Storing Passwords - done right! Written by: Christoph Wille Translated by: Bernhard Spuida First published: 1/5/2004 Viewed 257725 times. 1766 ratings, avg. grade 4.76 In very many - not to say almost all - Web applications user data is administered, from Web forum to Web shop.
These user data encompass login information of the users which contain the password besides the user name - and this in plain text. A security leak par excellence. Why is storing the user name and password in plain text a security leak? Well, imagine a cracker gaining system access through eventual OS or server software errors, and being able to read the user database.
CyberCIEGE Educational Video Game. An innovative video game and tool to teach computer and network security concepts CyberCIEGE enhances information assurance and cyber security education and training through the use of computer gaming techniques such as those employed in SimCity™.

In the CyberCIEGE virtual world, users spend virtual money to operate and defend their networks, and can watch the consequences of their choices, while under attack. Difference between WEP, WPA and WPA2 (Which is Secure) BESbswyBESbswy AddThis What's Next Recommended for you www.guidingtech.com AddThis.
Assignments. Wi-Fi Protected Setup Flaws Make Wireless Network Brute-force Attacks Feasible. Design flaws in the Wi-Fi Protected Setup (WPS) wireless standard can make it easier for attackers to obtain access codes for secured wireless networks by brute force.
The vulnerabilities identified by security researcher Stefan Viehbock affect a large number of WPS-enabled routers and wireless access points. The WPS standard was created in 2007 by the Wi-Fi Alliance in order to provide non-technical users with a simple method of setting up wireless networks. The standard supports several Wi-Fi authentication methods including one that requires pushing a physical button on the router and one that uses a predefined PIN number printed on a sticker by the device manufacturer.
The PIN-based method is mandatory for WPS-certified devices, which support it by default. Devices that are WPS-capable, but aren't certified, are also likely to use the method. The WPS PIN is an eight-digit random number. The main problem lies with how devices respond to failed WPS authentication attempts. The U.S. Wireshark Lab 1.