

Neurosurgery-with-meterpreter. (automating msf) UAV-slides.pdf. Nmap. Sambascan2 - SMB scanner. Sambascan2 is a small bash-script, which can scan for SMB-shares in a given Netz.
It currently needs nmap, find, smbclient, sed and grep. If you know a less agressive way for scanning on port 139, please tell me, because I thing nmap is not so polite :). Network Scanner. SoftPerfect Network Scanner is a free multi-threaded IP, NetBIOS and SNMP scanner with a modern interface and many advanced features.
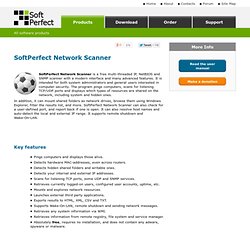
It is intended for both system administrators and general users interested in computer security. The program pings computers, scans for listening TCP/UDP ports and displays which types of resources are shared on the network, including system and hidden ones. In addition, it can mount shared folders as network drives, browse them using Windows Explorer, filter the results list, and more. SoftPerfect Network Scanner can also check for a user-defined port, and report back if one is open. It can also resolve host names and auto-detect the local and external IP range. Key features Pings computers and displays those alive. OpenVAS. Nessus Community. From the beginning, we've worked hand-in-hand with the security community.
We continuously optimize Nessus based on community feedback to make it the most accurate and comprehensive vulnerability assessment solution in the market. 20 years later and we're still laser focused on community collaboration and product innovation to provide the most accurate and complete vulnerability data - so you don't miss critical issues which could put your organization at risk. Today, Nessus is trusted by more than 27,000 organizations worldwide as one of the most widely deployed security technologies on the planet - and the gold standard for vulnerability assessment. Nexpose Community. Retina Community. Nessus/nmap (older) Hping3 cheatsheet. Nmap 5 (new) MSF, Fgdump, Hping. Metasploit meterpreter cheat sheet reference.
By Mark Baggett Scenario: You are doing a penetration test.

The client's internet face is locked down pretty well. No services are exposed externally and only HTTP/HTTPS are allowed OUT of the corporate firewall. You email in a carefully crafted email with the meterpreter attacked. An accommodating users is more than happy to click your attachment giving you meterpreter access to their machine. The Players Attacker 172.16.186.132 Victim 172.16.186.126 Step 1 - After you have meterpreter access install OpenSSH on the victim's computer.
Step 2 - After you've installed OpenSSH and setup your account use Meterpreters PORTFWD command to forward a port from the attacker's machine to the SSH listener on the victim's machine. Meterpreter> portfwd add -L 172.16.186.132 -l 8000 -r 172.16.186.128 -p 22 This command sets up a listener on port 8000 of the attacker's IP (172.16.186.132) and forwards packets to port 22 on the victim's machine (172.16.186.128).
Netcat cheat sheet. DNSTRACER man-page. Maltego 3. Document-metadata-silent-killer_32974 (application/pdf Object) [strike out] [ This page must be viewed with a browser that is capable of rendering visually distinct output for strikethrough and underline attributes.
![[strike out]](http://cdn.pearltrees.com/s/pic/th/strike-out-36973057)
Some text-based browsers (links) may not handle this properly, and so you are advised to switch to graphics. ] UPDATE (03/04/2004): The tool used to prepare data for this article is now available for download. Liked the article? How about a book of mine? This is not an exciting story: I happened to be browsing aimlessly through case studies and other publications released by Microsoft as a part of their "Get the facts" initiative. A pointless idea came to my mind that instant: why not run a gentle web spider against all Microsoft sites in English, specifically looking for other instances of tracking data not removed from documents? NOTE: Although some of the findings discussed here may be moderately embarassing for the company in question, I am not trying to make Microsoft look bad, and I do not think they are particularly evil.
(Nasirah Chaudhry) ExifTool by Phil Harvey. Read, Write and Edit Meta Information! Also available --> Utility to fix Nikon NEF images corrupted by Nikon software ExifTool is a platform-independent Perl library plus a command-line application for reading, writing and editing meta information in a wide variety of files. ExifTool supports many different metadata formats including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, ICC Profile, Photoshop IRB, FlashPix, AFCP and ID3, as well as the maker notes of many digital cameras by Canon, Casio, DJI, FLIR, FujiFilm, GE, GoPro, HP, JVC/Victor, Kodak, Leaf, Minolta/Konica-Minolta, Motorola, Nikon, Nintendo, Olympus/Epson, Panasonic/Leica, Pentax/Asahi, Phase One, Reconyx, Ricoh, Samsung, Sanyo, Sigma/Foveon and Sony.
Metagoofil - Metadata analyzer - Information Gathering. Security and Networking - Blog - Metadata Enumeration with FOCA. One very important part of any pentest is the gathering of information of the target network that will be attack and on area that is gaining a lot of traction is the enumeration thru metadata.

A tool I recently learned about by listening to the great podcast Exotic Liability where they mentioned the FOCA tool by Informatica64 when talking about their presentation at Blackhat Europe 09 you can either download the FOCA tool or you can use the webpage to summit your document for analysis. I do prefer to do most of my analysis locally since on almost all pentests I have conducted all information is confidential and the sharing of information with third parties is not permitted . After downloading run the setup executable and the tool will be available in the start menu under programs.
Once you execute the application you should see a screen line this one: But what if the file type you are looking for is not in the options like PNG or JPG? BeEF. BlindElephant Web Application Fingerprinter. XSSer: automatic tool for pentesting XSS attacks against different applications. Download RIPS software for free at SourceForge.net. Latest News Sun May 13 19:41:30 EDT 2007 - Daniel Black, a Gentoo developer, has been very helpful in bringing the autoconf setup up to date.
He also provided a fix for a crash caused by providing an absolute path to —username-file. Other than that, this release isn’t too execiting. I promise the next one will include time travel and a paradox solver. Mon Feb 12 19:39:59 EST 2007 - Well, I suppose it is about time for another release. Previously I had mentioned that I started a new version of authforce.
Attack and Defense Labs - Tools. Ravan is a JavaScript Distributed Computing system that uses HTML5 WebWorkers to perform brute force attacks on salted hashes in background JavaScript threads across a farm of workers.
Salted and plain versions of the following hashing algorithms are currently supported: MD5 SHA1 SHA256 SHA512 Try it online Description. Browser_Exploitation_for_Fun&Profit. Using sqid (SQL Injection Digger) to look for SQL Injection. Pinata-CSRF-tool. Overview: - The tool will generate proof of concept CSRF HTML given an HTTP request.
It will automatically check whether it is a GET or a POST request and with further validation for standard POST and Multipart/form POST. - The tool will then create an HTML corresponding to the type of the request. - The GET CSRF HTML includes IMG tag with SRC set to the URL being tested. XSSer: automatic tool for pentesting XSS attacks against different applications. Cross Site "Scripter" (aka XSSer) is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based applications.

It contains several options to try to bypass certain filters, and various special techniques of code injection. TIP: type: 'xsser --gtk' to start from shell. Clickjacker. Unicode-fun.txt Packet Storm. WebService-Attacker. w3af - Web Application Attack and Audit Framework. Skipfish - Project Hosting on Google Code. Sqlmap: automatic SQL injection tool. SQID - SQL Injection digger. SQID sql injection digger. WindowsAttack - fimap - Windows Attacking Example - Project Hosting on Google Code. Fm-fsf - Project Hosting on Google Code. Websecurify. Rfiscan Packet Storm. Lfi-rfi2 scanner Packet Storm. Inspathx Tool For Finding Path Disclosure Vulnerabilities. DotDotPwn - The Directory Traversal Fuzzer 2.1 Packet Storm. Koto/squid-imposter - GitHub.