

4shared.com - free file sharing and storage. Hacker9 - Social media, Hacking & Security. The Best Hacking Tutorial Sites - Learn Legal Hacking. The Ethical Hacker Network. The Premium Security Portal for Ethical Hackers. Hacking. The Best Hacking Tutorial Sites - Learn Legal Hacking. Hacking programs. Top 10 Web hacking techniques of 2010 revealed. Network World - A Web hack that can endanger online banking transactions is ranked the No. 1 new Web hacking technique for 2010 in a top 10 list selected by a panel of experts and open voting.

Called the Padding Oracle Crypto Attack, the hack takes advantage of how Microsoft's Web framework ASP.NET protects AES encryption cookies. FROM THE SECURITY WORLD: Quirky moments at Black Hat DC 2011 If encryption data in the cookie has been changed, the way ASP.NET handles it results in the application leaking some information about how to decrypt the traffic. With enough repeated changes and leaked information, the hacker can deduce which possible bytes can be eliminated from the encryption key. That reduces the number of unknown bytes to a small enough number to be guessed. The developers of the hack -- Juliano Rizzo and Thai Duong -- have developed a tool for executing the hack. Here are the rest of the top 10 Web hacks voted in the competition: 2. 3. 4. 5. 6. How the NSA's Firmware Hacking Works and Why It's So Unsettling.
One of the most shocking parts of the recently discovered spying network Equation Group is its mysterious module designed to reprogram or reflash a computer hard drive’s firmware with malicious code.
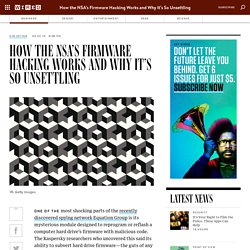
The Kaspersky researchers who uncovered this said its ability to subvert hard drive firmware—the guts of any computer—“surpasses anything else” they had ever seen. The hacking tool, believed to be a product of the NSA, is significant because subverting the firmware gives the attackers God-like control of the system in a way that is stealthy and persistent even through software updates.
The module, named “nls_933w.dll”, is the first of its kind found in the wild and is used with both the EquationDrug and GrayFish spy platforms Kaspersky uncovered. It also has another capability: to create invisible storage space on the hard drive to hide data stolen from the system so the attackers can retrieve it later. Hacking and Security Articles / Tutorials / White Papers at HellBound Hackers.
The Best Hacking Tutorial Sites - Learn Legal Hacking - StumbleUpon. Hacking. The Ethical Hacker Network. How to Hack: Ethical Hacking and Cyber Security. Top 10 Web hacking techniques of 2010 revealed. Hack This Site! Kali Linux "NetHunter" — Turn Your Android Device into Hacking Weapons. The developers of one of the most advance open source operating system for penetration testing, 'KALI Linux' have announced yesterday the release of a new Kali project, known as NetHunter, that runs on a Google Nexus device.
Kali Linux is an open source Debian-based operating system for penetration testing and forensics, which is maintained and funded by Offensive Security, a provider of world-class information security training and penetration testing services. It comes wrapped with a collection of penetration testing and network monitoring tools used for testing of software privacy and security. After making its influence in hacker and security circles, Kali Linux has now been published with Kali Nethunter, a version of the security suite for Android devices. The tool is a mobile distribution designed to compromise systems via USB when installed and run on an Android phone. Torrent search. Hacker. Hacking tutorials sites & tools. Torrents. The Peer to Peer Search Engine.
8 Good Password Cracking Tools For You. 1.RainbowCrack RainbowCrack is a general propose implementation of Philippe Oechslin's faster time-memory trade-off technique.
It crack hashes with rainbow tables. RainbowCrack uses time-memory tradeoff algorithm to crack hashes. It differs from brute force hash crackers. 2.NTAccess NTAccess can replace the administrator password of a Windows NT, Windows 2000, Windows XP, Windows Server 2003 or Windows Vista 32-Bit system by rebooting the computer with a special set of boot disks. Hackers_Hacking. Black Hat: Top 20 hack-attack tools. Network World - Turn someone else’s phone into an audio/video bug.
Check. Use Dropbox as a backdoor into corporate networks. Check. Suck information out of pacemakers. Best Hacker Tools Online and tutorials (video). Free Hacking Tools 2013 – 2014. Greeting BinusHacker Family, Berikut ini kita berbagi Peralatan / Tools yang biasanya dipakai oleh pentester, hacker, cracker, phiser dan bahkan Anonymous.
Hackerspace. BushTorrent.Com - Torrents from the White House.url. Torrent Search Engine Searcher - Torrent Scan (Powered by File Sharing. Torrent list.url. Bit-Torrent Torrent Downloads BITREACTOR.TO your Bit Torrent Resource. Torrent Portal Search results for - BitTorrent Search Index.url. Torrent Search Engine Searcher - Torrent Scan (Powered by File Sharing Z) Mininova : The ultimate BitTorrent source! h33t - quality torrents - free downloads - p2p file sharing PROPER.
FilesTube - Search for files on rapidshare and other download sites. AvaxHome. Torrent Search Engine Searcher - Torrent Scan (Powered by File Sharing Z) TehPARADOX.COM Online Sharing Community - No stupid slogans here, find out for yourself! Rapidshare-search-engine.com - Find files on rapidshare.
Orbit Downloader Start. Rapidshare Search Engine. FilesTube. Fulldls.com - Your Source For Daily Torrent Downloads.url. The Best Hacking Tutorial Sites - Learn Legal Hacking. How to Pirate Software Without Getting Caught. Welcome to Hellbound Hackers. Generate a Random Name - Fake Name Generator. The definitive glossary of hacking terminology. We live in an era of unprecedented cyberattacks, where malicious campaigns, both personal and governmental, are carried out across laptops and wireless networks.
Even if you are not technically minded, your day-to-day life is still probably pretty crowded with stories about hacking, whether you recognize them as such or not. Have you ever installed an antivirus tool on your computer? Read a story about WikiLeaks or the Arab Spring? Opened a bank account? Then hacking is important to you, even if remains largely in the background of your life. We’ve put together a glossary of what we believe to be the most important and current hacking terms you should know. Adware: Adware can mean the software that automatically generates advertisements in a program that is otherwise free, such as an online video game. Hacker9 - Social media, Hacking & Security. The Best Hacking Tutorial Sites - Learn Legal Hacking.
Hacking - Beginning txt. How To Become A Hacker. Copyright © 2001 Eric S.

Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker? ". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one. A lot of hackers now consider it definitive, and I suppose that means it is. Still, I don't claim to be the exclusive authority on this topic; if you don't like what you read here, write your own. If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document.
Numerous translations of this document are available: ArabicBelorussianChinese (Simplified), Czech, Danish, Dutch, Estonian, German, GreekItalianHebrew, Norwegian, PersianPortuguese (Brazilian), RomanianSpanish, Turkish, and Swedish. 1. 2. Learn Ethical Hacking Online - HackingLoops. There’s a seemingly endless number of free open-source tools for penetration testing, and most of them seem to gravitate around the Kali Linux distribution.
But with so many free tools, it’s easy to miss out on some of the best ones. So today we’re going to take a closer look at Armitage, define what it is, and define how it works. However, there’s a few things that you need to know before we start digging into the dirty details of how to use this tool. Naturally, I do have to give a brief warning before we get started, too. Don’t misuse or abuse any of the tools mentioned in this article for two reasons.
First of all, doing so would be unethical. Now that we’ve got that out of the way, let’s define what Armitage is and how it works. 80+ Best Free Hacking Tutorials. Learning to become hacker is not as easy as learning to become a software developer. I realized this when I started looking for learning resources for simple hacking people do. Even to start doing the simplest hack on own, a hacker requires to have in depth knowledge of multiple topics. Some people recommend minimum knowledge of few programming languages like C, Python, HTML with Unix operating system concepts and networking knowledge is required to start learning hacking techniques. Though knowing a lot of things is required, it is not really enough for you to be a competent and successful hacker. You must have a passion and positive attitude towards problem solving.
Google Hacks. How to Hack Someones IP Address 2014 - Come to Hack. Most of you may be curious to know how to find the IP address of your friend’s computer or to find the IP address of the person with whom you are chatting in Yahoo messenger or Gtalk.
Finding out someone's IP address is like finding their phone number, an IP address can be used to find the general location where that person lives. Now while most of the tutorials on the net teach you how to steal an ip address via MSN, or any other chat software, in this post I’ll show you how to find IP address of someones computer using script. Challenges - ThisisLegal.com. Generare un nome a caso - Fake Name Generator. Hackaday — Fresh hacks every day. How to Unlock a Computer Without a Password Reset Disk. Google Hacking Database, GHDB, Google Dorks. Hack This Site! The Peer to Peer Search Engine. Torrent Search Engine.
Torrents. Hacking. Torrents. Gigablast. Torrents. Evernote. Torrents. IsoHunt - BitTorrent & P2P torrent search engine. The Pirate Bay, renaissance et mutinerie annoncées. Si The Pirate Bay devrait renaître de ses cendres dans un jour maintenant, la forme allégée que le site va prendre ne plait pas aux administrateurs originaux qui veulent lancer un site concurrent. Une guerre semble engagée. Depuis la fermeture du TPB suite à une descente de police, la communauté des pirates accuse le coup. Néanmoins, très vite, l’espoir est apparu de voir The Pirate Bay renaitre de ses cendres. Confirmé par de petits indices laissés de ci de là et cette phrase empruntée à Schwarzinator : « I’ll be back ! ». Bonne nouvelle ? Plutôt qu’engager le combat en interne, les équipes étant disséminées à travers les continents, ces anciens pirates ont pris leurs distances avec thepiratebay.se et veulent lancer leur propre site concurrent.
. « J’aurais aimé avoir de meilleures nouvelles à vous annoncer. Et de prévenir, « Personnellement, je ne vais pas accepter ça, ce n’est ni la volonté de l’équipe qui a été active depuis près de 10-11 ans. Torrents. Context Gains Invaluable Life Hack and Business Content. Posted by Ronda Scott on 16 Mar 2015 Comment. Torrent search. Torrent Search Engine. About Hackers & Hacks. Peer Assessment with Google Forms and Filters. Cracks in the World (Novel Pranks, Mysteries, and Fun) Ethical hking. About Hackers & Hacks. H@cking.
How to Hack Someones IP Address 2014 - Come to Hack. The Best Hacking Tutorial Sites - Learn Legal Hacking. Hacking tutorials sites & tools. CTM Solutions. Torrent Crazy > page not found. Софт, аудио, видео, рисунки. Взлом. About us. Freepik is a search engine that helps graphic and web designers to locate high quality photos, vectors, icons, illustrations and PSD files for their creative projects. It’s an awesome tool that tracks and locates free graphic content on the Internet and it displays the results in an orderly layout for easy access. Also you will find a lot of free own and exclusive content, high quality, designed by the Freepik’s Team and updated every day.
Freepik makes it easier for you to find the files you need without manually searching dozens of websites. How does it work? Freepik Robots visit hundreds of web sites searching for free graphic resources, they read the contents of these sites and they select them if useful. Why is it free? The hard work at Freepik is not done by people. BitTorrent visualization. You can use the 's' and 'p' keys to add new seeds and peers to the swarm. Hitting 'r' will remove one of the seeds or peers at random, but it takes a few seconds before it activates, just like the original.
This visualization originally started off at aphid.org but that site doesn't seem to be up anymore. Jeff Atwood updated it to work with more recent versions of Processing (notably the 1.0 release which is theoretically API-stable and compatible with future versions). Once I saw processing.js, I knew that I had to get this working in it. Torrtilla.ru - Поиск по русским торрентам. Тысячи торрент файлов без регистрации и рейтинга. Torrent-trackers. Поисковик торрентов: фильмов, музыки, программ, файлов. Поиск по торрентам в DHT-сети. Мало найдётся людей среди пользователей и читателей Хабра, которым не доводилось бы пользоваться торрентами.