

CrypTool-Online. The origins of modern cryptography date back approximately 3000 years.
The procedures used to encrypt messages before 1900 were primitive compared to modern approaches, but they are easy to understand and provide a good basis to study the more complicated methods. In recent times, especially after the emergence of telecommunication equipment, more complex encryption methods have become necessary. Scytale Decoder. Decrypting text. Decabit-Impulsraster. Solve an Aristocrat or Patristocrat. Universal online Cyrillic decoder - recover your texts. Adyghe – ISO 9 transliteration system. Adyghe – ISO 9 transliteration system Adyghe virtual keyboard The Adyghe virtual keyboard allows you to enter characters with a click of your mouse.
There’s no need to change your keyboard layout anymore.
Ascii Table - ASCII character codes and html, octal, hex and decimal chart conversion. Freeware Hex Editor XVI32. [Overview] [Features] [What's New] [Screenshots] [User Reviews] [Download] [Installation] [Other Freeware] [Home] Overview XVI32 is a freeware hex editor running under Windows 9x/NT/2000/XP/Vista/7.

The name XVI32 is derived from XVI, the roman notation for the number 16. XVI32 and all of its components are developed by myself. The current release 2.55 is available since June 26, 2012. Binary to Text (ASCII) Conversion. TRANSLATOR, BINARY. Hollerith punched card. An 80-column punched card of the type most widely used in the 20th century. The size of the card was 7 3⁄8 in × 3 1⁄4 in (187.325 mm × 82.55 mm). This example displays the 1964 EBCDIC character set, which added more special characters to earlier encodings. A punched card, punch card, IBM card, or Hollerith card is a piece of stiff paper that contained either commands for controlling automated machinery or data for data processing applications.
Both commands and data were represented by the presence or absence of holes in predefined positions. As of 2012, some voting machines still utilize punched cards to record data.[2] History[edit] Punched cards were first used around 1725 by Basile Bouchon and Jean-Baptiste Falcon (fr) as a more robust form of the perforated paper rolls then in use for controlling textile looms in France. Baudot Paper Tape Code. This table presents a programmer's quick reference to the "Baudot" character set.
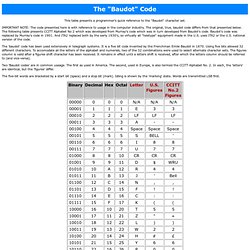
IMPORTANT NOTE: The code presented here is with reference to usage in the computer industry. The original, true, baudot code differs from that presented below. The following table presents CCITT Alphabet No 2 which was developed from Murray's code which was in turn developed from Baudot's code. Baudot's code was replaced by Murray's code in 1901. And ITA2 replaced both by the early 1930's, so virtually all "teletype" equipment made in the U.S. uses ITA2 or the U.S. national version of the code. The 'baudot' code has been used extensively in telegraph systems. Two 'Baudot codes' are in common useage. Purple Hell Riddle Tools - Index. Trifid Cipher. The Trifid Cipher is the Bifid Cipher taken to one more dimension.
Instead of using a 5x5 Polybius Square, you use a 3x3x3 cube. Otherwise everything else remains the same. As with the Bifid Cipher, the cube can be mixed to add an extra layer of protection, but for these examples we not be using a mixed alphabet cube. Enigma Simulation. Download Enigma Simulator. This software is an exact simulation of the 3-rotor Wehrmacht (Heer and Luftwaffe) Enigma, the 3-rotor Kriegsmarine M3, also called Funkschlussel M, and the famous 4-rotor Kriegmarine M4 Enigma cipher machine, used during World War II from 1939 until 1945.
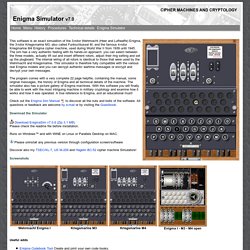
The sim has a very authentic feeling with its hands-on approach: you can select between the three models, actually lift out and insert different rotors, adjust their ring setting and set up the plugboard. The internal wiring of all rotors is identical to those that were used by the Wehrmacht and Kriegsmarine. This simulator is therefore fully compatible with the various real Enigma models and you can decrypt authentic wartime messages or encrypt and decrypt your own messages. The program comes with a very complete 22 page helpfile, containing the manual, some original messages, the history of Enigma and all technical details of the machine.
The simulator also has a picture gallery of Enigma machines. Fialka M-125. Pigpen Cipher Variants. Playfair Cipher. The Playfair cipher encrypts pairs of letters (digraphs), instead of single letters.
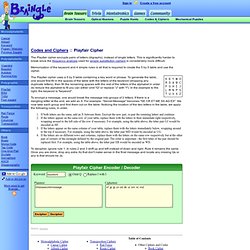
This is significantly harder to break since the frequency analysis used for simple substitution ciphers is considerably more difficult. Rot13.com. ROT-X : Encryption/Decryption. Cipher Tools. Cipher Statistics. Cryptography. When I wrote my first book, Fermat’s Last Theorem, I made a passing reference to the mathematics of cryptography.
Although I did not know it at the time, this was the start of a major interest in the history and science of codes and code breaking, which has resulted in a 400-page book on the subject, an adaptation of the book for teenagers, a 5-part TV series, numerous talks and lectures, the purchase of an Enigma cipher machine and the development of an interactive crypto CD-ROM. In the Crypto Corner, you will find details about my book on cryptography (The Code Book), information about my TV series based on the book (The Science of Secrecy) and you can explore the Black Chamber, which is an interactive encryption and codebreaking section. You will also find a section about the Cipher Challenge, there are some cryptograms (coded messages) for you to try and crack, a free downloadable CD-ROM version of The Code Book, and a quick Q&A based on the questions I am most often asked. Keyed Caesar. One variation to the standard Caesar cipher is when the alphabet is "keyed" by using a word.
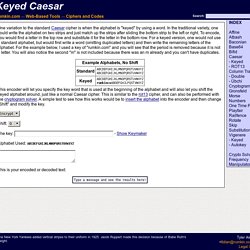
In the traditional variety, one could write the alphabet on two strips and just match up the strips after sliding the bottom strip to the left or right. To encode, you would find a letter in the top row and substitute it for the letter in the bottom row. For a keyed version, one would not use a standard alphabet, but would first write a word (omitting duplicated letters) and then write the remaining letters of the alphabet. For the example below, I used a key of "rumkin.com" and you will see that the period is removed because it is not a letter. You will also notice the second "m" is not included because there was an m already and you can't have duplicates. Steganography_Decode - Utility Mill - Utility. Sharky's Vigenere Cipher. This page is for amusement only.
Instructions are given below this form. instructions: Gronsfeld Cipher. Beaufort Cipher. Vigenere Variants. Introduction.