

Finite field. Every finite division ring is a finite field by Wedderburn's little theorem.
Finite fields are fundamental in a number of areas of mathematics and computer science, including number theory, algebraic geometry, Galois theory, cryptography and coding theory. Classification[edit] Statement[edit] The finite fields are classified as follows (Jacobson 2009, §4.13, p. 287): This classification justifies using a naming scheme for finite fields that specifies only the order of the field.
Or Fpn. A prime power field with p = 2 is also called a binary field. Elliptic curve cryptography. Elliptic curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields.
Elliptic curves are also used in several integer factorization algorithms that have applications in cryptography, such as Lenstra elliptic curve factorization. The use of elliptic curves in cryptography was suggested independently by Neal Koblitz[1] and Victor S. Miller[2] in 1985. Elliptic curve cryptography algorithms entered wide use in 2004 to 2005. Introduction[edit] The primary benefit promised by ECC is a smaller key size, reducing storage and transmission requirements, i.e. that an elliptic curve group could provide the same level of security afforded by an RSA-based system with a large modulus and correspondingly larger key – e.g., a 256-bit ECC public key should provide comparable security to a 3072-bit RSA public key (see key sizes below). The U.S. The DES Algorithm Illustrated. The DES (Data Encryption Standard) algorithm is the most widely used encryption algorithm in the world.

For many years, and among many people, "secret code making" and DES have been synonymous. And despite the recent coup by the Electronic Frontier Foundation in creating a $220,000 machine to crack DES-encrypted messages, DES will live on in government and banking for years to come through a life- extending version called "triple-DES. " How does DES work? This article explains the various steps involved in DES-encryption, illustrating each step by means of a simple example.
Since the creation of DES, many other algorithms (recipes for changing data) have emerged which are based on design principles similar to DES. The Enigma Wiki - FeistelCipher. Feistel cipher. In cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German-born physicist and cryptographer Horst Feistel who did pioneering research while working for IBM (USA); it is also commonly known as a Feistel network.
A large proportion of block ciphers use the scheme, including the Data Encryption Standard (DES). The Feistel structure has the advantage that encryption and decryption operations are very similar, even identical in some cases, requiring only a reversal of the key schedule. Number_Theory_I_ClickandClimb.com. Introduction to encryption with DES. April 2014 DES, secret-key decryption On 15 May 1973, the NBS (National Bureau of Standards, now called NIST - National Institute of Standards and Technology) published a request in the Federal Register for an encryption algorithm that would meet the following criteria: have a high security level related to a small key used for encryption and decryption be easily understood not depend on the algorithm's confidentiality be adaptable and economical be efficient and exportable In late 1974, IBM proposed "Lucifer", which, thanks to the NSA (National Security Agency), was modified on 23 November 1976 to become the DES (Data Encryption Standard).
Rotor machine. A series of three rotors from an Enigma machine, used by Germany during World War II In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting secret messages.
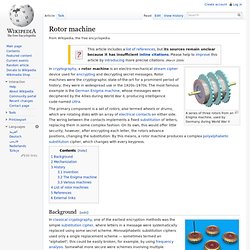
Rotor machines were the cryptographic state-of-the-art for a prominent period of history; they were in widespread use in the 1920s–1970s. The most famous example is the German Enigma machine, whose messages were deciphered by the Allies during World War II, producing intelligence code-named Ultra. The primary component is a set of rotors, also termed wheels or drums, which are rotating disks with an array of electrical contacts on either side.
Rail Fence Cipher. "Rail Fence Cipher" (also called a zigzag cipher) generally refers to a form of transposition cipher.
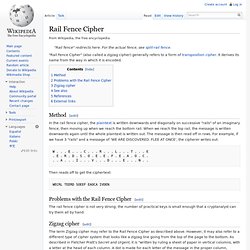
It derives its name from the way in which it is encoded. Method[edit] In the rail fence cipher, the plaintext is written downwards and diagonally on successive "rails" of an imaginary fence, then moving up when we reach the bottom rail. When we reach the top rail, the message is written downwards again until the whole plaintext is written out. Vernam. Encryption: Episode 2 - The Vernam Cipher from AT&T Labs.
One-time pad. Autokey cipher. In modern cryptography, self-synchronizing stream ciphers are autokey ciphers.
History[edit] The first autokey cipher was invented by Girolamo Cardano, and contained a fatal defect. Like many autokey ciphers it used the plaintext to encrypt itself; however, since there was no additional key, it is no easier for the intended recipient to read the message than anyone else who knows that the cipher is being used.[1] A number of attempts were made by other cryptographers to produce a system that was neither trivial to break nor too difficult for the intended recipient to decipher. Eventually one was invented in 1564 by Giovan Battista Bellaso using a "reciprocal table" with five alphabets of his invention and another form was described in 1586 by Blaise de Vigenère with a similar reciprocal table of ten alphabets. Giovan Battista Bellaso used the first letter of each word as a primer to start his text autokey.
Plaintext: ATTACK AT DAWN... Cryptanalysis[edit] We have a lot to work with now. Kasiski examination. In cryptanalysis, Kasiski examination (also referred to as Kasiski's Test or Kasiski's Method) is a method of attacking polyalphabetic substitution ciphers, such as the Vigenère cipher.
It was first published by Friedrich Kasiski in 1863,[1] but seems to have been independently discovered by Charles Babbage as early as 1846.[2] How it works[edit] Vigenere Cipher. Playfair Cipher Explained.