

Technical surveillance counter-measures - Wikipedia. TSCM (technical surveillance counter-measures) is the original United States Federal government abbreviation denoting the process of bug-sweeping or electronic countersurveillance.
It is related to ELINT, SIGINT and electronic countermeasures (ECM). The United States Department of Defense defines a TSCM survey as a service provided by qualified personnel to detect the presence of technical surveillance devices and hazards and to identify technical security weaknesses that could aid in the conduct of a technical penetration of the surveyed facility. A TSCM survey will provide a professional evaluation of the facility's technical security posture and normally will consist of a thorough visual, electronic, and physical examination in and about the surveyed facility. This definition is however lacking some of the technical scope involved. Methodology[edit] Radio frequencies[edit] What the Law Says about Distributing a Virus or Malware.
The Internet allows an individual to either inadvertently or purposely disseminate malware (such as a virus) to other systems globally.
The potential impact could encompass the “infection” or compromise of millions of hosts. This has occurred. A “harmless experiment” by Cornell University student Robert Morris involved the release onto the Internet of a type of malware called a “worm” that compromised over 6,000 computers and required millions of dollars worth of time to eradicate. Spyware Laws and Legal Issues. Attempting or gaining access to someone's computer without their consent or knowledge is criminally illegal according to computer crime laws, such as the United States Computer Fraud and Abuse Act and the United Kingdom's Computer Misuse Act.
Does this mean that spyware is illegal? Not necessarily. Though law enforcement has often pursued the creators of malware like viruses, spyware developers have been largely un-prosecuted under criminal law, though they occasionally do face lawsuits. Many spyware companies even operate as legitimate businesses. Spyware creators remain largely untouched because of the way spyware generally finds itself on your computer. Regin: Top-tier espionage tool enables stealthy surveillance. Malware Targets Scandinavia via Dropbox Abuse - AppRiver. Early this morning, Denmark, Germany and several surrounding Scandinavian countries were hit with a large volume malware attack.
The attack leveraged the legitimate cloud storage service Dropbox to host their malware payloads while attempting to disguise the links with random strings of characters and varying filenames. In the past 12 hours, we have quarantined thousands of these messages, which only represents a small percentage of the total message volume. Security in-a-box. Rapid Responses For Compromised Phones. Tips, Tools and How-tos for Safer Online Communications.
FBI Surveillance Hacks Android Devices, Laptops. In recent months, Americans were aghast to learn that their phone calls were secretly being recorded and collected by a government agency, the NSA, when the extent of their indiscriminate wiretapping program was leaked to the public.

But if you think that’s an invasion of privacy, you’d better hope the NSA never gets its hands on FBI surveillance techniques and tactics…such as the ability to remotely turn on the microphones in laptops and Android devices without you knowing it. How’s that for Big Brother? Because what’s a little espionage between family? We’ve all watched enough TV to know that wiretapping is no problem for the mishmash of acronymic government agencies (FBI, CIA, NSA, NASA, etc.), but those same shows have taught us certain assumptions about wiretapping, like the necessity of a warrant, and the necessity of the phone actually being in a call. New Links~ 'Hacker News'. Data Breaches and How to Secure Against Them. Applications and operating systems are easily reinstalled.
However, your data is quite a bit more unique. This means that it is the most critical thing that you have on your network or computer. Everything You Wanted to Know about TOR & the Deep Web. The Real Science Behind Cracking Passwords. b46f685f85e0af830d82ddbbe795eff3 By adding a unique salt, I can do something about that.
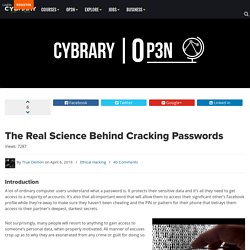
I created a quick Javascript program that takes the user’s name, and pulls the first and last three letters from their username and makes them into a salt. Then, the program takes the salt, plus the user’s password, and runs them through the MD5 algorithm and produces the hash that will be their password. Take a look at the results below. Username | Password | HASH. New Trojan Turns Linux Devices into Botnet. New Linux Trojan turns infected Linux Devices and websites into P2P botnets and threatens users with DDoS and ransom!
— This Trojan is one of its kind! Linux is considered as one of the most secure operating systems but things seem to be changing as cyber criminals are equipping themselves with the latest tools. That’s why recently, researchers at Doctor Web have discovered a Linux trojan that can turn an infected Linux device and websites into a P2P botnets. Usually, a malware is designed to infect devices in order to steal financial and personal data but ”Linux.Rex.1” malware has the ability to perform DDoS attacks from the infected device, send malicious messages and distribute itself to others networks. Computer acting funny? It may be infected with a virus! One great thing about computers is that they often warn us when something is wrong.
Sometimes they suddenly slow down to a crawl, other times they start to freeze up or even crash for what seems to be no reason at all. Most of the time though, there is a reason why our computers start to act funny. One of those reasons is due to malware and viruses. 5 Terrifying Smartphone Hacks You Won't Believe Are Possible. Sometimes we fail to appreciate the fact that today, right now, we're living in a sci-fi universe.
The smartphone is a miracle of mathematics and engineering genius, converting a little over 4 ounces of inert matter into a Star Trek-level wondercomputer. Simple Steps to Hack a Smartphone. What kind of information do you have on your business card? Company name? Check. Android 4.4 KitKat also affected by Master Key vulnerability. The flaw known as “Android Master Key vulnerability” is considered a nightmare for Android OS, last July it was discovered for the first time and experts revealed that 99% of Android devices are vulnerable. The Master Key vulnerability allows hackers to modify any legitimate and digitally signed application in order to include malicious code that can be used to steal data or to gain remote control of the mobile device. The Master Key vulnerability was discovered and responsibly disclosed by Bluebox Labs that demonstrated that the Android vulnerability allows app modification preserving signatures.
The flaw was fixed later with Android 4.3 Jelly Bean version, Google adopted as countermeasure the modification of app submission process to the Play Store to avoid the publishing of malicious application that have been packaged using such exploit. Hackers Exploit Default Apps to Install Malware on Samsung Galaxy S4. Researchers Demonstrate Exploits Against Mobile Platforms at Mobile Pwn2Own 2013 This week at the Mobile Pwn2Own hacking contest taking place at the PacSec Applied Security Conference in Tokyo, Japan, a team of security researchers demonstrated exploits against several applications installed by default on Samsung Galaxy S4 smartphones that enabled them to silently install a malicious application and steal sensitive data.
Team MBSD, of Japanese firm Mitsui Bussan Secure Directions, Inc., earned $40,000 for their exploit efforts which enabled them to successfully compromise the Samsung device running Google’s Android. “This team exploited multiple apps, installed by default on the Samsung Galaxy S4 to install malware and steal confidential data,” HP’s Heather Goudey explained in a blog post. “In order for the exploit to be successful, the affected user must first be lured to an attacker-controlled malicious website. The vulnerability was disclosed to Samsung, HP said. Black Hat: Top 20 hack-attack tools. Network World - Turn someone else’s phone into an audio/video bug. Check. Use Dropbox as a backdoor into corporate networks. Check. Suck information out of pacemakers. Check. The Black Hat conference convening in Las Vegas next week offers hacker tools for all of those plus more.
The Web's #1 Hacking Tools Directory - with tutorial videos! Hacking Tools Directory with Video Tutorials By Henry Dalziel | Information Security Blogger | Concise Courses We are big fans of blogging about Hacker Tools – for one major reason: if you are serious about working in cyber security you need to be able to use these tools like a boss. Hacking tools are what boxing gloves are to a boxer or what a spanner is to a plumber. A pentester (or ethical hacker) can be judged by their ability to use these tools, frameworks and programs, so get to know them! Tips, Tools and How-tos for Safer Online Communications. Data Breaches and How to Secure Against Them.
How to block the companies tracking you on Facebook. Researchers crack the world’s toughest encryption by listening to the tiny sounds made by your computer’s CPU. Security researchers have successfully broken one of the most secure encryption algorithms, 4096-bit RSA, by listening — yes, with a microphone — to a computer as it decrypts some encrypted data. The attack is fairly simple and can be carried out with rudimentary hardware. The repercussions for the average computer user are minimal, but if you’re a secret agent, power user, or some other kind of encryption-using miscreant, you may want to reach for the Rammstein when decrypting your data.
Criminal Record, Background Check, Trace email, Phone Number lookup, People search, cell phone number search, License Plate Search. Tips, Tools and How-tos for Safer Online Communications. How Hackers Protect Themselves From Getting Hacked. Top 50 Hacking Tools That You Must Have. The definitive glossary of hacking terminology. We live in an era of unprecedented cyberattacks, where malicious campaigns, both personal and governmental, are carried out across laptops and wireless networks. CELL PHONE HACKS. Since the popularity of text messages have significantly increased during the recent years, it has also become a popular channel for most people to exchange secret messages and engage in dubious activities. These text messages can. Free Anonymous Hacking Tools 2013 – 2014. Greeting BinusHacker Family, How To Search On Google Like Elite Hackers. Google is best search engine in the world. Start Hacking.
Mobile Spy - Monitor SMS Text Messages, Call Info and GPS Locati. Hackers Handbook. Operation DisBARLeiderman. Opt out of global data surveillance programs like PRISM, XKeyscore, and Tempora - PRISM Break. Internet Toolkit. Update Check. Anonymous Operating System. GNU hackers discover HACIENDA government surveillance and give us a way to fight back — Free Software Foundation — working together for free software. The Unpatchable Malware That Infects USBs Is Now on the Loose. SecTools.Org Top Network Security Tools. Experts crack nasty ransomware that locks your PC and your backup. The Web's #1 Hacking Tools Directory - with tutorial videos! Black Hat: Top 20 hack-attack tools.
Security Distributions. Linux Security - The Community's Center for Security. SecLists.Org Security Mailing List Archive. Insecure.Org - Tools & Hacking resources. Top Network Security Tools. Hacker Tools (Top Ten List of 2016) Nmap, Wireshark, Metasploit. Hacking - Beginning txt. Penetration Testing Explained, Part VII: Exfiltration and Conclusions. Penetration Testing Explained, Part VI: Passing the Hash. Penetration Testing Explained, Part V: Hash Dumping and Cracking. Penetration Testing Explained, Part IV: Making the Lateral Move. Penetration Testing Explained, Part III: Playing with RATs and Reverse Shells.
Penetration Testing Explained, Part II: RATs! Penetration Testing Explained, Part I: Risky Business. How to use Google for Hacking. Quantum cryptography system hacked. Trojan hides in Google Play games, uses steganography to find more malicious code to run. Android malware uses Google Cloud Messaging Service as C&C Server. Sophisticated Android Trojan Spreads Through Mobile Botnet. Android bug batters Bitcoin wallets. AndroRAT drives the rise for DIY Android hacking tools. Android Firefox Zero-Day exploit available on the underground. The Art of Human Hacking. dSploit: penetration test con Android. Mission Impossible: Hardening Android for Security and Privacy.
There's a Way to Protect Your Android from Malware, Theft & Privacy Gaps. Intercepter-NG - Wifi Packet Sniffer Android App. NASA HACKER FOUND EVIDENCE AMERICA HAS DEEP SPACE WARSHIPS. He can hack into your smartphone with 1 SMS. How to use Google for Hacking. Google Dorks & Google Hacking » Freakitude. How to View Passwords Hidden Under Asterisks [Video] From Missingno to Heartbleed: Buffer Exploits and Buffer Overflows. Hacking Websites with SQL Injection - Computerphile. YouTube Doesn't Know Your Password. The Link That Can Crash Chrome: The Attack That Could Disrupt The Whole Internet - Computerphile. Learn the Wget Command with 20 Practical Examples. How to Crack WPA2 WPS WiFi password. Wireless Penetration. Hacker Tools (Top Ten List of 2016) Nmap, Wireshark, Metasploit. The jaw-dropping promise — and brain-twisting challenge — of quantum computing. Raw. 6 Best Hacking Books You Must Read to be a Hacker.
80+ Best Free Hacking Tutorials. Hacking - Beginning txt. Security Response Removal Tools - Symantec Corp. Computer Viruses. 3 Best Resources To Find Known Sites With Spyware & Viruses. Professional. True.Crypt. Whois.net Lookup - Domain Names Search. Hacking Tip: How To Use Proxies. Hotspot Shield.