

Internetworking. Internet tools. Opt Out. MedIT. U.S. Department of State Freedom of Information Act (FOIA) This site is designed to assist you in making a request for records controlled by the U.S.
Department of State. If you would like to request records from another agency, you may wish to view a list of Other Federal Agencies’ FOIA Web Sites . Information Access Guide – if you would like to request Department of State Records, please follow the instructions in our comprehensive guide. Digital Due Process. FAQ – Privacy & Terms – Google. How are you implementing the recent Court of Justice of the European Union (CJEU) decision on the right to be forgotten?
The recent ruling by the Court of Justice of the European Union has profound consequences for search engines in Europe. The court found that certain users have the right to ask search engines like Google to remove results for queries that include the person's name. Neo Techno Ethica. Bit Coin Review. Match.com will find you someone who looks like your ex. New Web and email address options exploded this year with 469 new top-level domain names.
Next year, Google, Amazon and 10 others will bid for rights to oversee .app. In 2014, the renaming of the Net has begun in earnest. Three Day Rule, a modern take on matchmaking. ✉ Guerrilla Mail - Disposable Temporary E-Mail Address. Data Protection Officials Adopt Internet of Things Declaration and Big Data Resolution.
Home > International > Data Protection Officials Adopt Internet of Things Declaration and Big Data Resolution At the International Conference of Data Protection and Privacy Commissioners in Mauritius this week, representatives of the private sector and academia joined together to discuss the positive changes and attendant risks that the internet of things and big data may bring to daily life.

Network Advertising Initiative. Opt Out of Interest-Based Advertising NAI members are committed to transparency and choice.

The NAI opt-out tool was developed in conjunction with our members for the express purpose of allowing consumers to "opt out" of the Interest-Based Advertising delivered by our members. Some of the ads you receive on Web pages are customized based on predictions about your interests generated from your visits over time and across different Web sites. This type of ad customization — sometimes called “online behavioral” or “interest-based” advertising — is enabled through your computer browser and browser cookies.
NAI: Network Advertising Initiative. The RFID Ecosystem Project - University of Washington, CSE. The Internet Gets Physical. This snack-food corporation has a creepy plan to watch you in the grocery store. (20th Century Fox / Dreamworks Pictures) It's not quite "Minority Report"-levels of creepiness, but it's getting there.
Mondelez International, whose properties include Chips Ahoy, Nabisco, Ritz and other high-profile snack brands, says it's planning to debut a grocery shelf in 2015 that comes equipped with sensors to determine the age and sex of passing customers. Do Not Track - Universal Web Tracking Opt Out. Tracking Preference Expression (DNT) Abstract.
NSA uses Google cookies to pinpoint targets for hacking. A slide from an internal NSA presentation indicating that the agency uses at least one Google cookie as a way to identify targets for exploitation.
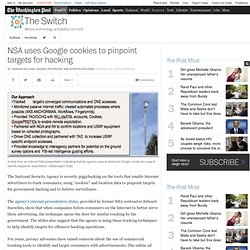
(Washington Post) The National Security Agency is secretly piggybacking on the tools that enable Internet advertisers to track consumers, using "cookies" and location data to pinpoint targets for government hacking and to bolster surveillance. The agency's internal presentation slides, provided by former NSA contractor Edward Snowden, show that when companies follow consumers on the Internet to better serve them advertising, the technique opens the door for similar tracking by the government.
The slides also suggest that the agency is using these tracking techniques to help identify targets for offensive hacking operations. For years, privacy advocates have raised concerns about the use of commercial tracking tools to identify and target consumers with advertisements. Who in Congress Supports SOPA and PIPA/PROTECT-IP? Frequently Asked Questions on Identity Cards » NO2ID. What is an ID card?

The government is planning to establish a system that will involve unprecedented collation and monitoring of personal information. The House of Lords said the Identity Cards Bills name is misleading. This is about more than plastic cards! An ID card, as part of the National Identity Scheme, will impose upon every adult legally resident in this country, including foreign nationals, a card which will link to the National Identity Register, holding fifty pieces of information about each of them. Anti-Counterfeiting Trade Agreement. What Is ACTA?
The Anti-Counterfeiting Trade Agreement (ACTA) is an agreement to create new global intellectual property (IP) enforcement standards that go beyond current international law, shifting the discussion from more democratic multilateral forums, such as the World Trade Organization (WTO) and the World Intellectual Property Organization (WIPO), to secret regional negotiations. Through ACTA, the US aims to hand over increased authority to enforcement agencies to act on their own initiative, to seize any goods that are related to infringement activities (including domain names), criminalize circumvention of digital security technologies, and address piracy on digital networks. ACTA was negotiated from 2007 through 2010 by the US, the EU, Switzerland, Canada, Australia, New Zealand, Mexico, Singapore, Morocco, Japan, and South Korea.
Eight out of the eleven negotiating countries signed the agreement in October 2011. About Ads on Search, Gmail and across the web - Ads Help. How shared endorsements work - Google+ Help. To ensure that your recommendations reach the people you care about, Google sometimes displays your reviews, recommendations and other relevant activity throughout its products and services. This sometimes includes shopping contexts, like the Google Play music store, and ads.
Self Regulatory Frameworks – Policies & Principles – Google. Only the unmeasured is free. How Apple and Amazon Security Flaws Led to My Epic Hacking. In the space of one hour, my entire digital life was destroyed. First my Google account was taken over, then deleted. Next my Twitter account was compromised, and used as a platform to broadcast racist and homophobic messages. And worst of all, my AppleID account was broken into, and my hackers used it to remotely erase all of the data on my iPhone, iPad, and MacBook. In many ways, this was all my fault. A Crashlytics Innovation. Engage. OAuth Community Site. Welcome to myOpenID. What is OpenID? OpenID allows you to use an existing account to sign in to multiple websites, without needing to create new passwords. You may choose to associate information with your OpenID that can be shared with the websites you visit, such as a name or email address.
OpenID Explained. The Data Liberation Front. Anonymity Online. Telecommunications data retention. In the field of telecommunications, data retention (or data preservation) generally refers to the storage of call detail records (CDRs) of telephony and internet traffic and transaction data (IPDRs) by governments and commercial organisations. In the case of government data retention, the data that is stored is usually of telephone calls made and received, emails sent and received and web sites visited. Location data is also collected. The primary objective in government data retention is traffic analysis and mass surveillance. By analysing the retained data, governments can identify the locations of individuals, an individual's associates and the members of a group such as political opponents.
Open Rights Group - Home. Defending civil liberties, protecting privacy. 2012 Law Enforcement Requests Report. Microsoft receives legal demands for customer data from law enforcement agencies around the world. In March 2013, as part of our commitment to increased transparency, Microsoft began publishing details of the number of demands we receive each year in our Law Enforcement Requests Report and clear documentation of our established practices in responding to government legal demands for customer data.
We update this report every six months, and each report includes the number of demands we receive and the number of accounts or identifiers that may be affected by these demands. We also provide details on the number of demands we complied with and, if we complied, whether we provided content or non-content data. This Law Enforcement Requests Report is focused only on law enforcement requests at this time and does not include data about national security requests. Windows Live ID. Manage your data – Good to Know – Google. FBI launch facial recognition program. European Data Protection Authorities Publish Guidelines Clarifying Exemptions to Cookie Consent Requirement : Privacy Law Blog. Home > Data Privacy Laws > European Data Protection Authorities Publish Guidelines Clarifying Exemptions to Cookie Consent Requirement On June 7, 2012, the Article 29 Working Party, an independent advisory body composed of representatives from the national data protection authorities of the EU Member States, the European Data Protection Supervisor and the European Commission, issued Opinion 04/2012 regarding which types of cookies are exempted from the informed user-consent requirement under Directive 2002/58 of the European Parliament (the E-Privacy Directive).
Article 5.3 of the E-Privacy Directive requires that websites must obtain informed consent from users prior to storing cookies on users’ equipment. WP 29 use of Location based data. Media : 10 Reasons To Delete Your Facebook Account. Facebook Privacy. Facebook reveals its evil plans. Remember how everyone said that after Facebook went public, it would one day begin to reveal its evil plans for turning your personal data into money? Audiences: Syndicated Segments for Online Consumer Targeting. Your Mom’s Guide to Those Facebook Changes, and How to Block The. Codes/processes - Simplify Facebook Wall. Protect Your Privacy Opt Out of Facebook’s New Instant Personali. Facebook does it again! FB asks users to identify friends. Facebook no longer lets users hide from search. Facebook is ending a feature that allowed users to hide from the social network's billion-plus members.
NeWeb Privacy. Web World Things. Cyber Security. NeWeb Security.