

Jean marc manach (@manhack) Cash Investigation : Le business de la peur - France 2 - 21 septembre 2015 - En replay. Aujourd’hui, les lecteurs d’empreintes digitales sont partout : pour ouvrir la porte de chambres d’hôtel, le portail d’une crèche ou déverrouiller un téléphone portable.
Ils servent aussi dans les centrales nucléaires ou pour le contrôle aux frontières. Pourtant, un peu d’ingéniosité et de colle à bois suffisent aux enquêteurs de "Cash Investigation" pour démontrer que ces capteurs soi-disant hyperfiables peuvent être facilement piratés. Démonstration : l'équipe de "Cash Investigation" a réussi à tromper les portiques de sécurité de l’aéroport Charles-de-Gaulle.
Des chiffres bidon Le commerce de la sécurité est fondé sur la peur. La vie privée, un problème de vieux cons ? Le livre. En résumé : La vie privée, un problème de « vieux cons » ?
(le livre) peut donc être commandé sur Amazon, la Fnac, l'AppStore (pour iPhone & iPad), et dans toutes les bonnes librairies... Depuis que j'ai écrit cet article intitulé La vie privée, un problème de vieux cons ? , en mars 2009, je ne compte plus le nombre de gens qui sont persuadés d'être des "vieux cons", alors que non : la vie privée, ce n'est pas un problème de "vieux cons", la preuve : jamais on en avait autant parlé que depuis que l'internet est arrivé.
A contrario, depuis que j'ai aussi écrit Vie privée : le point de vue des “petits cons”, je ne compte plus le nombre de gens qui m'ont remercié d'avoir ainsi décrit ce que les internautes vivent et sont, au-delà des clichés dont ils sont affublés... mais qui n'ont pas forcément pour autant pris la mesure de la "société de surveillance" qui, pour le coup, attente gravement à nos libertés. Grandes oreilles et bras cassés. On the Internet, nobody knows you're a dog. L’internet et les « pédo-nazis » : le best of. J'en avais rêvé, Stéfan l'a fait : sur son blog, 36 15 ma vie, il a compilé une dizaine de reportages passés aux JT de France Télévision dans les années 90, qu'il a débusqué dans les archives de l'Ina et qui tous présentent l'internet comme un repère de pédophiles, de nazis, de trafiquants de drogue et de médicaments, de terroristes aussi.
Bref, de pédo-nazis, comme on avait fini par les surnommer en cette fin de siècle dernier. Au risque de choquer certains : non seulement c'est (bien évidemment très -très très- exagéré), mais c'est tant mieux, et on aurait tort de s'en priver, pour la simple et bonne raison que le fait qu'ils se montrent permet, aussi, de les débusquer (voir aussi le billet que j'avais déjà écrit à ce sujet : Les pédophiles sont sur le Net. Nous aussi. Et tant mieux.). Trêve de bavardage, passons maintenant à la télévision, et à l'excellent billet de Stéfan, qu'il m'a autorisé à reproduire ici-bas : Pedonazi. Darkweb. What Was Silk Road? Refresh Your Memory as Ross Ulbricht Goes to Trial. The Official Site of the Ulbricht Family. Plongée dans l'Internet criminel. Oubliez Google ou Yahoo, laissez tomber les extensions familières en .com, .fr ou .net.
Sous la partie émergée d'Internet, loin, très loin dans les profondeurs de la Toile, se cache un monde interlope dont le commun des internautes ignore tout, où jamais il ne descendra. Dans ces bas-fonds du Web, tout se négocie le plus discrètement du monde et les accroches commerciales ne font pas dans la nuance. Savez-vous « éviscérer un voisin sans en gâter la viande » ? Connaissez-vous les plus insoupçonnables associations médicamenteuses pour condamner vos ennemis au silence éternel ?
Pour garder les mains propres, des professionnels se chargent de la basse besogne : comptez 5 000 € pour faire disparaître un proche, le triple pour un journaliste. C'est par ce biais que fut révélée la véritable identité du « dépeceur de Montréal », Luka Magnotta. Bienvenu dans le dark Web. Newsletter DSEZP : Free Download, Borrow, and Streaming. Deep web. Le renseignement militaire et les «petits pédés» de 4chan. Web profond.
Un article de Wikipédia, l'encyclopédie libre.
Ne doit pas être confondu avec darknet. Ne pas confondre[modifier | modifier le code] Ressources profondes[modifier | modifier le code] Les robots d'indexation sont des programmes utilisés par les moteurs de recherche pour parcourir le web. Afin de découvrir de nouvelles pages, ces robots suivent les hyperliens. On peut classer les ressources du web profond dans une ou plusieurs des catégories suivantes : contenu dynamique ;contenu non lié ;contenu à accès limité ;contenu de script ;format non indexable. Voir aussi la section raisons de la non-indexation qui donne plus de précision. Darknet. Un article de Wikipédia, l'encyclopédie libre.
Un darknet (parfois appelé réseau friend-to-friend (F2F) : ami à ami) est un réseau privé virtuel dont les utilisateurs sont considérés comme des personnes de confiance. La plupart du temps, ces réseaux sont de petite taille, souvent avec moins de dix utilisateurs chacun. Un darknet peut être créé par n'importe quel type de personne et pour n'importe quel objectif, mais la technique est le plus souvent utilisée spécifiquement pour créer des réseaux de partage de fichiers en pair à pair[réf. nécessaire]. Onion Routing: Our Sponsors. This research was supported in part at NRL's Center for High Assurance Computer Systems (CHACS) by: Office of Naval Research (ONR), Basic R&D work in addition to support for the coding of all generation systems (0,1, and 2).
Support for deployment of generation 2 (Tor) testbed and open source development site. Defense Advanced Research Projects Agency (DARPA), High Confidence Networking Program, and Fault Tolerant Networks Program Support for system performance assessments and system improvements. Support for robustness, survivability, traffic management, and congestion control. Almost Everyone Involved in Developing Tor was (or is) Funded by the US Government. “The United States government can’t simply run an anonymity system for everybody and then use it themselves only.
Because then every time a connection came from it people would say, “Oh, it’s another CIA agent.” Anonymity Online. Tor and HTTPS. Click the "Tor" button to see what data is visible to eavesdroppers when you're using Tor.

Users – Tor Metrics. This graph shows the estimated number of directly-connecting clients; that is, it excludes clients connecting via bridges.
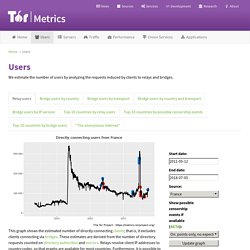
These estimates are derived from the number of directory requests counted on directory authorities and mirrors. Relays resolve client IP addresses to country codes, so that graphs are available for most countries. Furthermore, it is possible to display indications of censorship events as obtained from an anomaly-based censorship-detection system (for more details, see this technical report). For further details see these questions and answers about user statistics. Who uses Tor? Tor was originally designed, implemented, and deployed as a third-generation onion routing project of the Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Today, it is used every day for a wide variety of purposes by the military, journalists, law enforcement officers, activists, and many others.
Here are some of the specific uses we've seen or recommend. 4% (only) of the 12,189 recently updated darknet websites are dealing with drugs. Les stupéfiants représentent plus de 20 % (contre moins de 5 % pour les armes) des affaires liées au réseau Tor. Le darknet est trop compliqué pour les terroristes. « Ceux qui nous frappent utilisent le Darknet et des messages chiffrés pour accéder à des armes qu’ils acquièrent en vue de nous frapper », affirmait récemment Bernard Cazeneuve à l’Assemblée. Or, Cryptopolitik and the Darknet, une étude de Thomas Rid et Danny Moore, respectivement professeur et thésard en cybersécurité au département de la guerre du King’s College London, vient tempérer ce genre d’affirmations péremptoires. « La chose la plus surprenante fut de découvrir une si faible présence des militants et extrêmistes« , a déclaré Thomas Rid au magazine Quartz.
De fait, l’une des découvertes les plus notables de leur étude est précisément « notre confirmation de la quasi-absence de l’extrémisme islamique sur les services Tor cachés, avec moins d’une poignée de sites actifs ». The 7 Privacy Tools Essential to Making Snowden Documentary CITIZENFOUR. What needs to be in your tool belt if you plan to report on a massively funded and ultra-secret organization like the NSA? In the credits of her newly released CITIZENFOUR, director Laura Poitras gives thanks to a list of important security resources that are all free software. This is what a Tor Supporter looks like: Laura Poitras. The first thing that Laura Poitras has to say about Tor is that she couldn’t have made Citizenfour without it.
Making Connections to Facebook more Secure. 'Tor Stinks' presentation – read the full document. Partir en mission avec son téléphone, sa tablette ou son ordinateur portable. Recueil de Conseils : Utilisation de moyens de chiffrement à l’étranger - Club des Directeurs de Sécurité & de Sûreté Des Entreprises. Publié le 24 juin 2016 Ce recueil de conseil, réalisé par la commission Cyber sécurité du CDSE,propose des réponses par rapport aux situations liées à l’utilisation de moyens de chiffrement à l’étranger les plus courantes. Les conseils exposés dans ce guide vous permettront d’anticiper votre départ en mission et de vous familiariser avec les règles d’usage des moyens de chiffrement à l’étranger. Il est le complément du passeport de conseils aux voyageurs. Dans de nombreux pays étrangers, le cadre réglementaire peut instituer des contrôles aux frontières de vos équipements, limitant ou non l’introduction et l’usage de moyens de chiffrement : il vous faut vous conformer aux demandes des autorités du pays, afin d’éviter de vous exposer à des amendes, voire même à un emprisonnement.
Rendez-Vous - Agora des Directeurs Juridiques.