

Explainshell.com - match command-line arguments to their help text. Connecting to an LDAP Directory. Skip to end of metadataGo to start of metadata You can connect your Confluence application to an LDAP directory for authentication, user and group management.
Overview An LDAP directory is a collection of data about users and groups. Powerline-shell/README.md at master · milkbikis/powerline-shell. Thefuck/README.md at master · nvbn/thefuck. Thefuck/README.md at master · nvbn/thefuck. Why, oh WHY, do those #?@! nutheads use vi? The VI Gang Sign by Jon Beltran de Heredia, May 16th, 2007.

OpenSMTPD + UW IMAP как альтернатива тяжелым почтовым системам. Почти каждому, у кого есть сервера с привязанными к ним доменами, так или иначе приходится решать вопрос с почтой, как минимум с доступностью адресов вида webmaster/postmaster/abuse@domain.

Software architect Kristof Kovacs. Just a list of 20 (now 28) tools for the command line.
Bash users: What do you have for your $PS1? : programming. Eugeny/ajenti. Modern Microprocessors - A 90 Minute Guide! WARNING: This article is meant to be informal and fun!

Okay, so you're a CS graduate and you did a hardware course as part of your degree, but perhaps that was a few years ago now and you haven't really kept up with the details of processor designs since then. In particular, you might not be aware of some key topics that developed rapidly in recent times... pipelining (superscalar, OOO, VLIW, branch prediction, predication) multi-core and simultaneous multi-threading (SMT, hyper-threading) SIMD vector instructions (MMX/SSE/AVX, AltiVec, NEON) caches and the memory hierarchy Fear not! This article will get you up to speed fast.
But be prepared – this article is brief and to-the-point. More Than Just Megahertz The first issue that must be cleared up is the difference between clock speed and a processor's performance. Table 1 – Processor performance circa 1997. Upstart - event-based init daemon. How Mailgun Uses Docker And Contributes Back. There are a lot of good reasons to be excited about containers, a form of operating system-level virtualization with many applications.
At Mailgun, we’re excited about containers for four major reasons: Containers on our laptops are exactly the same as our staging and potentially production environments. This makes it easy to find and fix potential problems before we push to production and pulls together our dev and ops in a way that goes beyond buzzword compliance.We get more bang for our buck with containers instead of virtual machines. Because containers share operating systems, there’s no overhead from multiple OSs running concurrently. It’s great for getting big performance gains on dedicated boxes.Containers make it easy to rapidly change infrastructure from dedicated hosting or on-premise machines to public cloud and back as necessary.
Start working with Docker today and you’ll quickly find yourself doing some of the same things over and over again. We scanned the Internet for port 22. Yesterday (Sept. 12) we scanned the entire Internet for port 22 -- the port reserved for "SSH", the protocol used by sysadmins to remotely log into machines.
Unlike our normal scans of port 80 or 443, this generated a lot more "abuse" complaints, so I thought I'd explain the scan. Firstly, we'll happily add you to our "blacklist", so that we won't scan you ever again (barring accidents on our part). Our current blacklist is hundreds of entries long. However, please consider adding our scanner (71.6.151.167) to your "whitelist".
Masscan: the entire Internet in 3 minutes. I thought I'd write up some notes about my "masscan" port mapper.
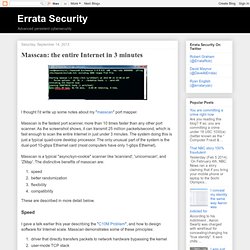
Masscan is the fastest port scanner, more than 10 times faster than any other port scanner. As the screenshot shows, it can transmit 25 million packets/second, which is fast enough to scan the entire Internet in just under 3 minutes. The system doing this is just a typical quad-core desktop processor. Getting Started - Docker, The linux container engine.
We try to make using Docker easy.
The C10K problem. [Help save the best Linux news source on the web -- subscribe to Linux Weekly News!] It's time for web servers to handle ten thousand clients simultaneously, don't you think? After all, the web is a big place now. And computers are big, too. Shell scripts. I am big fan of shell scripts and so love to learn interesting stuff from other's shell scripts.
Recently i came across the authy-ssh scripts which eases two-factor authentication for ssh servers. When i walk through scripts, i learned lot of cool things that i am going to share it with you. Ports Database. SG TCP/IP Ports contains a comprehensive, searchable database of official and unofficial tcp/udp port[1] assignments, known vulnerabilities, trojans, applications use and more. The ports, services and protocols database contains combined information derived from IANA, numerous port lists, as well as our own research and user submissions. You can search by application/service name, or simply click on port numbers below for detailed information.
Please simply use the "Add comment" buttons on individual port pages to add information about ports not already in the database. Security Tools.