

Less Popular Google Search Tips. There’s not a day that passes by without searching for information on Google.
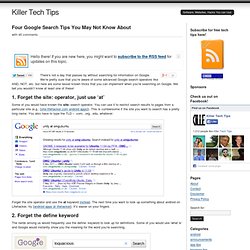
We’re pretty sure that you’re aware of some advanced Google search operators like AND, NOT, etc. but here are some lesser known tricks that you can implement when you’re searching on Google. We bet you wouldn’t know at least one of these! 1. Forget the site: operator, just use ‘at’ Some of you would have known the site: search operator. Forget the site operator and use the at keyword instead. 2. The nerds among us would frequently use the define: keyword to look up for definitions. You needn’t necessarily use the define keyword anymore to get definitions in search results. 3. AROUND(n) is an undocumented search operator and it will be of immense use when you’re looking for pages with two terms separated by n number of words. 4. You can use the tilde (~) operator to search for pages that not only contain the word that follows it, but also its synonyms. Top 15 Open Source/Free Security/Hacking Tools.
1.
Nmap Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. Nmap homepage. 2.
Wireshark is a network protocol analyzer. 3. Metasploit Community Edition simplifies network discovery and vulnerability verification for specific exploits, increasing the effectiveness of vulnerability scanners. 4. Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers. Hacking - Beginning txt. How to Pirate Software Without Getting Caught. The Best Hacking Tutorial Sites - Learn Legal Hacking. Top 50 Hacking Tools That You Must Have. Whether you are a Penetration tester, a hacker or an aspiring newbie trying to learn Cyber Security, you must have a nice catalogue of tools to make your life easier.
While these tools do make working simpler but cannot compensate for the vast amount of knowledge required in this field. In this post i’m going to mention 50 different tools under 9 categories that your ‘Hack Lab’ must have. Most of the tools mentioned in this post are pre-included in Kali Linux which you can install to have them at once.
Intrusion Detection Systems :- These are the tools you must have if you’re building a hack lab for penetration testing or for any security arrangement. SnortNetCop Encryption Tools :- While the above tools do identify any suspicious activity but they can’t protect your data, you need encryption tools for that. TrueCrypt (The project has been shut down and no longer supported)OpenSSHPuttyOpenSSLTorOpenVPNStunnelKeePass Port Scanners :- NmapSuperscanAngry IP Scanner Packet Sniffers :- Enjoy..!! Google Guide Cheatsheet. How to use Google for Hacking.
Google serves almost 80 percent of all the search queries on the Internet, proving itself as the most popular search engine.
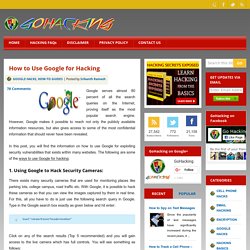
However, Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post, you will find the information on how to use Google for exploiting security vulnerabilities that exists within many websites. The following are some of the ways to use Google for hacking: 1. Using Google to Hack Security Cameras: There exists many security cameras that are used for monitoring places like parking lots, college campus, road traffic etc. Inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. As you can see in the above screenshot, you now have access to the Live cameras which work in real-time. Intitle:”Live View / – AXIS”