

Certificate Expiry Monitor. Download the Free Nmap Security Scanner for Linux/MAC/UNIX or Windows. Nmap and Zenmap (the graphical front end) are available in several versions and formats.
Recent source releases and binary packages are described below. Older version (and sometimes newer test releases) are available from the dist directory (and really old ones are in dist-old). For the more security-paranoid (smart) users, GPG detached signatures and SHA-1 hashes for each release are available in the sigs directory (verification instructions). Before downloading, be sure to read the relevant sections for your platform from the Nmap Install Guide. PSEXEC. S Golden Ratio Typography Calculator.
Events and Errors. Events and Errors documentation is organized by server roles and server fundamentals.
Within each role and fundamental, the information is organized in a hierarchical structure, based on the logical parts of an application or service that an administrator configures or uses to perform an administrative task. This hierarchy presents an overview of the system as a whole from the management perspective. A good example is the Printing Infrastructure hierarchy. In the Printing Infrastructure hierarchy, there are two major logical components: the Print Server and the Print Migration Tool.
The rest of the logical components in the hierarchy—the queue, the spooler, the cluster, the driver, and the ports—are aligned under the Print Server itself. Managed Entities have specific functional areas called Aspects that are of interest to an administrator. At the lowest level of the hierarchy are events. Organize your resources in an online binder - LiveBinders. 40 of the Best To-Do Apps for Personal Task Management.
To-do lists don't need to be complicated—plenty of people use a pen and paper for the job without any problem.
And yet a new to-do list app seems to come out every day. OpenOffice and LibreOffice templates, tutorials, tips and FAQ. Tutorials/articles Calculating in text documents Cross references: How to use Cross references: working with Desktop Publishing with OOo.
My Life Organized. Troubleshoot Windows Event Logs. WLAN Book. WizShark - Wi-Fi Troubleshooting Made Easy. Top 47 Log Management Tools. Operating systems, such as Windows and Unix, as well as networks such as Cisco, typically offer some native log management functionality.
But these log and event management mechanisms fall short of consolidating the data in any meaningful way, leaving bits and pieces of event logs scattered across a network. Not to mention, many of those events are lost as a result of overwrites, creating a security and compliance problem. Third-party, comprehensive log management tools, however, offer built-in consolidation, archiving, alerting and reporting — the functionality needed to actually turn log data into useful insights. Whether you need log management solutions for Windows, Linux or any other platform, and regardless of the number of log sources you need to monitor, there’s a log management solution that will meet your specific requirements.
NOTE: The following 47 log management tools are listed in random order, not in order of performance or capabilities. 1. Key Features: Change Local Admin Password on remote Computers. Create a hidden admin account. Password is expiring notification. Check services run on domain by specific user. Social Media Monitoring, Analytics and Alerts Dashboard. Operational Intelligence, Log Management, Application Management, Enterprise Security and Compliance. Dhcp Explorer - Discover DHCP servers on your LAN. Dynamic Host Configuration Protocol (DHCP) is a client-server networking protocol and uses the same two IANA assigned ports for BOOTP: 67/udp for the server side, and 68/udp for the client side.
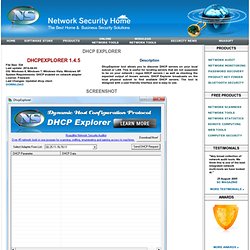
A DHCP server provides configuration parameters specific to the DHCP client host requesting, generally, information required by the client host to participate on an IP network. DHCP also provides a mechanism for allocation of IP addresses to client hosts. DHCP server is a useful tool that automates the assignment of IP addresses to hundreds of workstations in your network. The server maintains a pool of IP addresses that you use to create scopes.
Speedtest.net - The Global Broadband Speed Test. Alpha: Examples by Topic. OUI Lookup Tool. SimpleMind Desktop. 6 free network vulnerability scanners. Though you may know and follow basic security measures on your own when installing and managing your network and websites, you'll never be able to keep up with and catch all the vulnerabilities by yourself.
Vulnerability scanners can help you automate security auditing and can play a crucial part in your IT security. They can scan your network and websites for up to thousands of different security risks, producing a prioritized list of those you should patch, describe the vulnerabilities, and give steps on how to remediate them. Some can even automate the patching process. Five free network analyzers worth any IT admin's time. If you work on a network, you then know the value of information.
Solid information leads to a strong and worry-free network (or at least as worry-free as you can manage). In order to gather that information, you need the right tools. Resources and Tools for IT Professionals. Syswow64 blog: Bitlocker. What is Bitlocker?
Bitlocker Drive Encryption allows you to encrypt all data stored on the Windows operating system volume and configured data volumes, and by using a Trusted Platform Module (TPM), it can also help ensure the integrity of early startup components. Bitlocker was updated with the release of Windows 7 and Windows Server 2008 R2. Backing Up Bitlocker and TPM Recovery Information to AD DS Backing up recovery passwords for a Bitlocker-protected drive allows administrators to recover the drive if it is locked.
This ensures that encrypted data belonging to the enterprise can always be accessed by authorized users. Gravit – unlock your design potential. Paint.NET - Free Software for Digital Photo Editing. Emulators. Mohawk - Mohawk: A tool for verifying access-control policies. Mohawk is tool for verifying correctness of access-control policies.
Mohawk accepts an ARBAC policy and a safety query as inputs, and reports an error if it finds one. Otherwise, Mohawk terminates and reports that it could not find any errors. Mohawk uses an abstraction-refinement based technique and bounded model checking for quickly identifying errors. The basic idea behind the approach is that it is efficient to verify an abstract policy than the full policy. Mohawk operation comprises multiple steps. New The latest version of Mohawk uses novel methods for calculating the diameter of an ARBAC policy and uses that as the bound when using the bounded model checker.
Tasklist. Windows Compatibility Center: Find Updates, Drivers, & Downloads for Windows 8, Windows RT and Windows 7. Network Calculators. Auditing. The Windows Filtering Platform (WFP) provides auditing of firewall and IPsec related events. These events are stored in the system security log. The audited events are as follows. By default, auditing for WFP is disabled. Auditing can be enabled on a per-category basis through either the Group Policy Object Editor MMC snap-in, the Local Security Policy MMC snap-in, or the auditpol.exe command.
Security Risk Management Guide. Published: October 15, 2004 | Updated: March 15, 2006 Click here to get the Security Risk Management Guide from the Microsoft Download Center. The Security Risk Management Guide is a technology-agnostic solution that provides a four-phased approach to risk management. The guide references many industry accepted standards for managing security risk, and incorporates real-world experiences from Microsoft IT and also includes input from Microsoft customers and partners. NetworkMiner - The NSM and Network Forensics Analysis Tool. NetworkMiner is a Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, hostnames, open ports etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
NetworkMiner makes it easy to perform advanced Network Traffic Analysis (NTA) by providing extracted artifacts in an intuitive user interface. The way data is presented not only makes the analysis simpler, it also saves valuable time for the analyst or forensic investigator. NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. Splunk For Application Development, DevOps and APM.
Splunk® software allows you to quickly identify and pinpoint code-level issues at any stage of the development and release process. Iplog. Iplog is a TCP/IP traffic logger. Currently, it is capable of logging TCP, UDP, and ICMP traffic. iplog is able to detect TCP port scans, TCP null scans, FIN scans, UDP and ICMP "smurf" attacks, bogus TCP flags, TCP SYN scans, TCP "Xmas" scans, ICMP ping floods, UDP scans, and IP fragment attacks. iplog is able to run in promiscuous mode and monitor traffic to all hosts on a network. iplog uses libpcap to read data from the network and can be ported to any system that supports pthreads and on which libpcap will function. BackTrack Linux - Penetration Testing Distribution. Top 100 Network Security Tools. Automating security configuration tasks: Security Configuration Editor; Security Services.
Updated: January 21, 2005. Measuring Disk Latency with Windows Performance Monitor (Perfmon) - Ask the Core Team. Wevtutil. Updated: April 17, 2012 Applies To: Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows 8. Music Text Composition Generator ( A free online music utility) The P22 Music Text Composition Generator allows any text to be converted into a musical composition. Select license. Traceroute - VisualRoute - Download Page. Qnext Secure File Sharing and Access App. Wire Shark. Online TraceRoute - SubnetOnline.com. Nessus Vulnerability Scanner. From the beginning, we've worked hand-in-hand with the security community.
PsExec. Introduction Utilities like Telnet and remote control programs like Symantec's PC Anywhere let you execute programs on remote systems, but they can be a pain to set up and require that you install client software on the remote systems that you wish to access. PsExec is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software. Wireshark Display Filter Examples (Filter by Port, IP, Protocol) While debugging a particular problem, sometimes you may have to analyze the protocol traffic going out and coming into your machine.
Wireshark is one of the best tool used for this purpose. In this article we will learn how to use Wireshark network protocol analyzer display filter. 1. How to Use Wireshark to Capture, Filter and Inspect Packets.