

Tips, Tools and How-tos for Safer Online Communications. Catalog Reveals NSA Has Back Doors for Numerous Devices. Editor's note: This article accompanies our main feature story on the NSA's Tailored Access Operations unit.
You can read it here. When it comes to modern firewalls for corporate computer networks, the world's second largest network equipment manufacturer doesn't skimp on praising its own work. According to Juniper Networks' online PR copy, the company's products are "ideal" for protecting large companies and computing centers from unwanted access from outside. Canvas Fingerprinting: How to Stop the Web's Sneakiest Tracking Tool in Your Browser. I believe the government should be allowed to view my e-mails, tap my phone calls, and view my web history for national security concerns. CMV : changemyview.
Facebook, the CIA, and You. // Brainsturbator. NSA Haiku Generator. N.S.A. Devises Radio Pathway Into Computers. Photo WASHINGTON — The National Security Agency has implanted software in nearly 100,000 computers around the world that allows the United States to conduct surveillance on those machines and can also create a digital highway for launching cyberattacks.

While most of the software is inserted by gaining access to computer networks, the N.S.A. has increasingly made use of a secret technology that enables it to enter and alter data in computers even if they are not connected to the Internet, according to N.S.A. documents, computer experts and American officials. The technology, which the agency has used since at least 2008, relies on a covert channel of radio waves that can be transmitted from tiny circuit boards and USB cards inserted surreptitiously into the computers. In some cases, they are sent to a briefcase-size relay station that intelligence agencies can set up miles away from the target. Continue reading the main story. Police tapping iPhone for facial recognition. Some law-enforcement agencies are preparing to deploy a mobile facial-recognition tool, The Wall Street Journal reported today.
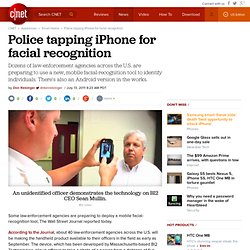
According to the Journal, about 40 law-enforcement agencies across the U.S. will be making the handheld product available to their officers in the field as early as September. The device, which has been developed by Massachusetts-based BI2 Technologies, allows officers to take a photo of a person from a distance of five feet or less. That photo is then compared with a database of images of people with criminal records to see if there is a match. The device is also capable of scanning a person's iris. Opt out of PRISM, the NSA’s global data surveillance program - PRISM BREAK. NSA surveillance: how to stay secure. Now that we have enough details about how the NSA eavesdrops on the internet, including today's disclosures of the NSA's deliberate weakening of cryptographic systems, we can finally start to figure out how to protect ourselves.
For the past two weeks, I have been working with the Guardian on NSA stories, and have read hundreds of top-secret NSA documents provided by whistleblower Edward Snowden. The NSA’s Latest Attempt to Hack Your Computer ... And What You Can Do To Stop It. Ted BaumannActivist Post Sometimes I wonder just how bad the news about government spying can get.
The answer was in my inbox this morning. I quickly ran out of superlatives: Awful. Terrible. Five Eyes. Richard Stallman explains iBads and Cell Phones. This is how we know Echelon exists. Is the Pentagon Spying on Americans? WASHINGTON - A year ago, at a Quaker Meeting House in Lake Worth, Fla., a small group of activists met to plan a protest of military recruiting at local high schools.

What they didn't know was that their meeting had come to the attention of the U.S. military. A secret 400-page Defense Department document obtained by NBC News lists the Lake Worth meeting as a threat and one of more than 1,500 suspicious incidents across the country over a recent 10-month period. Privacy as the New Free-Trade Zone of Corporate Exploitation. (Image via Shutterstock) Truthout doesn't take corporate money and we don't shy away from confronting the root causes of injustice.
NNDB: Tracking the entire world. The Technium. Cloud-Powered Facial Recognition Is Terrifying - Jared Keller - Technology. By harnessing the vast wealth of publicly available cloud-based data, researchers are taking facial recognition technology to unprecedented levels.
The Transparency Grenade by Julian Oliver (@julian0liver) – Design Fiction for Leaking Data. New DVRs will use cameras and microphones to monitor their owners. 14 Incredibly Creepy Surveillance Technologies That Big Brother Will Soon Be Using To Spy On You. The following are 14 incredibly creepy surveillance technologies that Big Brother will soon be using to watch you....
A company known as BRS Labs has developed "pre-crime" surveillance cameras that can supposedly determine if you are a terrorist or a criminal even before you commit a crime. Well, authorities are taking this technology quite seriously. In fact, dozens of these cameras are being installed at major transportation hubs in San Francisco.... The company says will put them in 12 stations with up to 22 cameras in each, bringing the total number to 288.The cameras will be able to track up to 150 people at a time in real time and will gradually build up a ‘memory’ of suspicious behaviour to work out what is suspicious. #2 Capturing Fingerprints From 20 Feet Away Can you imagine someone reading your fingerprints from 20 feet away without you ever knowing it?
This kind of technology is actually already here according to POPSCI.... #3 Mobile Backscatter Vans #4 Hijacking Your Mind. Contradicting a Federal Judge, FCC Clears Google in Wi-Fi Sniffing Debacle. The Federal Communications Commission is clearing Google of wrongdoing in connection to it secretly intercepting Americans’ data on unencrypted Wi-Fi routers.
The commission concluded Friday, in an order unveiled Monday, that no wiretapping laws were violated when the search giant’s Street View mapping cars eavesdropped on open Wi-Fi networks across America. The FCC said that, between 2008 and 2010, “Google’s Street View cars collected names, addresses, telephone numbers, URL’s, passwords, e-mail, text messages, medical records, video and audio files, and other information from internet users in the United States.” Last year, a federal judge ruled that the search-and-advertising giant could be held liable for violating federal wiretapping law, giving the greenlight to lawsuits seeking damages over Google’s objections.
Is the Government Spying On You Through Your Own Computer’s Webcam Or Microphone?