

Untitled. Linux has a mechanism to avoid a DoS attack – with regard to logging – called rate limit.

Every message logged by the kernel (including its modules), with printk(), is checked if it’s allowed to be actually printed through this mechanism. The limits can be configured by tuning the files /proc/sys/kernel/printk_ratelimit and /proc/sys/kernel/printk_ratelimit_burst. In my machine, the values for these files are 5 and 10, respectively, meaning: It’s allowed 10 messages every 5 seconds. Exceeding this will make the kernel discard the message and print something like “ratelimit N: callbacks suppressed”. However, the networking code in the kernel has its own limit configuration. The message_cost file contains the interval and message_burst contains the maximum number of messages allowed in that interval. To disable this mechanism and allow every message to be logged, simply set the interval to 0: # sysctl -w net.core.message_cost=0. dSniff. Dsniff is a set of password sniffing and network traffic analysis tools written by security researcher and startup founder Dug Song to parse different application protocols and extract relevant information. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, etc.). arpspoof, dnsspoof, and macof facilitate the interception of network traffic normally unavailable to an attacker (e.g., due to layer-2 switching). sshmitm and webmitm implement active man-in-the-middle attacks against redirected SSH and HTTPS sessions by exploiting weak bindings in ad-hoc PKI.[2] [3] Overview[edit] The applications sniff usernames and passwords, web pages being visited, contents of email etc.
The name "dsniff" refers both to the package as well as an included tool. This Is the Most Detailed Picture of the Internet Ever (and Making it Was Very Illegal) Why would you need a map of the Internet?
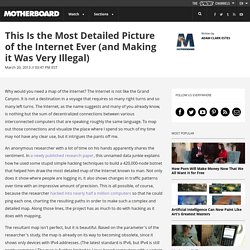
The Internet is not like the Grand Canyon. It is not a destination in a voyage that requires so many right turns and so many left turns. The Internet, as the name suggests and many of you already know, is nothing but the sum of decentralized connections between various interconnected computers that are speaking roughly the same language. To map out those connections and visualize the place where I spend so much of my time may not have any clear use, but it intrigues the pants off me. An anonymous researcher with a lot of time on his hands apparently shares the sentiment.
The resultant map isn't perfect, but it is beautiful. But on a general, half-a-million-computer level, this is what the Internet looks like in all of its gorgeous motion: This map shows the average Internet usage of the observed nodes over a 24-hour period. Hacking into 420,000 computers is highly illegal. However, these were not sophisticated attacks. RFC 4186 - Extensible Authentication Protocol Method for Global System for Mobile Communications (GSM) Subscriber Identity Modules (EAP-SIM)
What is SPDY? Deployment Recommendations. Originally written by Sehoon Park In the middle of this year a news report announced that Facebook is planning to support Google's SPDY protocol in large scale, and that they are already implementing SPDY/v2.
Here is the official response from Facebook that I have found on this topic. Among various efforts devised and suggested by Google to make the Web faster, I think SPDY will be the one to become a new industry standard, and it will be included in HTTP/2.0. As an acronym of SPeeDy, SPDY is a new protocol Google has suggested as a part of its efforts to "make the Web faster. " It was suggested as a protocol to use the present and future Internet environment more efficiently by addressing the disadvantages of HTTP devised in the early Internet environment.
In this article, I will provide a brief introduction to the features and merits of SPDY. When was the latest version of HTTP released? Table 1: Comparison of Mean Webpage Size in 2010 and 2012. OpenOnload. Current IP Check.
Geographic Implications of DNS Infrastructure Distribution - The Internet Protocol Journal - Volume 10, No. 1. The past several years have seen significant efforts to keep local Internet communications local in places far from the well-connected core of the Internet.
Although considerable work remains to be done, Internet traffic now stays local in many places where it once would have traveled to other continents, lowering costs while improving performance and reliability. Data sent directly between users in those areas no longer leaves the region. Applications and services have become more localized as well, not only lowering costs but keeping those services available at times when the region's connectivity to the outside world has been disrupted. I discussed the need for localization in a previous paper, "Internet Mini-Cores: Local connectivity in the Internet's spur regions.
" [1] What follows here is a more specific look at a particular application, the Domain Name System (DNS). It should be noted that information about DNS deployment is changing rapidly. DNS Hierarchy Root Servers Methodology.
Test your IPv6.