

How to Crack a Wi-Fi Network. 1.Back Track Today we’re going to run down, step-by-step, how to crack a Wi-Fi network with WEP security turned on. Dozens of tutorials on how to crack WEP are already all over the internet using this method. Seriously—Google it. This ain’t what you’d call “news.” But what is surprising is that someone like me, with minimal networking experience, can get this done with free software and a cheap Wi-Fi adapter. Unless you’re a computer security and networking ninja, chances are you don’t have all the tools on hand to get this job done. . * A compatible wireless adapter—This is the biggest requirement. . * A BackTrack 3 Live CD.
. * A nearby WEP-enabled Wi-Fi network. . * Patience with the command line. To crack WEP, you’ll need to launch Konsole, BackTrack’s built-in command line. First run the following to get a list of your network interfaces: The only one I’ve got there is labeled ra0. Now, run the following four commands. An Incredible Way to Reveal Passwords Behind Asterisks. Google Hacking Database, GHDB, Google Dorks - StumbleUpon. The Best Hacking Tutorial Sites - Learn Legal Hacking - StumbleUpon. Tips and downloads for getting things done - StumbleUpon. How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine.
However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. The following are some of the hacks that can be accomplished using Google. 1. Hacking Security Cameras There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time. Inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. you now have access to the Live cameras which work in real-time.
Intitle:”Live View / – AXIS” Dorks & hacks Big list. Google hacking master list. This master list of Google Hacking command sets has show up on a forum in Russia, as well as on Scribd.
While we often forget about Google hacking, and rarely use it against our own sites, a list like this is going to keep the kids happy as they merrily pound their way through Google to your systems. This makes the data much more accessible than at Johnny I hack stuff. There are some drawbacks in how Johnny I hack stuff works, you have to do a lot of clicking to get to the right hacks. This master list also includes things I have not seen or tried yet meaning that the body of knowledge for Google hacks is still being expanded upon. Miu-miu-sparrow-pumps> Shoeperwoman. These shoes sold out almost instantly at Net-a-Porter (sorry if the sight of them just got your hope up, there), which surprises me slightly, because in addition to the fact that they cost £365, they’re not the kind of shoes I would expect to have widespread appeal.
With that said, these are one of Miu Miu’s most talked-about styles of the season, which possibly explains the high demand. With navy blue uppers and a white sparrow print, they have a breezy, Spring style to them, which will fit in seamlessly with all of the nautical style clothes around right now (and not just in my closet, either!). Application server. ColdFusion EnterpriseRapidly build highly scalable websites and mobile applications.
Loading... Buy now Try › ColdFusion StandardCode and deploy robust single-server websites and applications. Loading... Buy now Try › ColdFusion BuilderProfessional tools for serious developers. Learn more › Carina's Craftblog: Tutorial: crochet granny triangle. So!
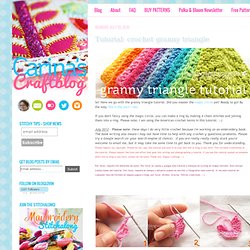
Here we go with the granny triangle tutorial. Did you master the magic circle yet? Ready to go? By the way, this is the yarn I use. Design*Sponge » Blog Archive » trendspotting: brutalism. Hi, folks!
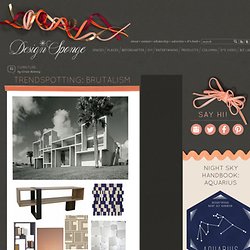
Nick Olsen here, interior decorator, style blogger and newest addition to the design*sponge family. Grace has asked me to scour the market for trends in design and decorating and I’m super thrilled. So let’s get to it: I was tempted to title this post “Hard Times” because my first theme, Brutalism, extends far beyond credenzas and tchotchkes. Things are still a little rough all over in 2010! But as an architectural movement, Brutalism (from the French term for “raw concrete”) busted out in the 1950s and 60s with blocky, imposing structures by Le Corbusier, Paul Rudolph, and later I.M. Perhaps the most famous Brutalist furniture designer is the late Paul Evans, who successfully married artisanal craftsmanship and mass appeal by teaming up with Directional for his famed Cityscape Collection.
VMware Virtualization Software for Desktops, Servers & Virtual Machines for Public and Private Cloud Solutions. Global Provider of Innovative Graphics, Processors and Media Solutions. Laptop, Notebook, Desktop, Server and Embedded Processor Technology - Intel. Office 2010: Office 2010 Tools for School. Hardware and Software, Engineered to Work Together. Apple. PHP: Hypertext Preprocessor.
SaaS Application Packaging Standard. SaaS Application Packaging Standard.