

Baltimore Sun - We are currently unavailable in your region. Anarchy and the Morality of Violence. California Bill Seeks Phone Crypto Backdoor. A week after a New York legislator introduced a bill that would require smartphone vendors to be able to decrypt users’ phones on demand from law enforcement, a California bill with the same intent has been introduced in that state’s assembly.
On Wednesday, California Assemblyman Jim Cooper submitted a bill that has remarkably similar language to the New York measure and would require that device manufacturers and operating system vendors such as Apple, Samsung, and Google be able to decrypt users’ devices. The law would apply to phones sold in California beginning Jan. 1, 2017. “This bill would require a smartphone that is manufactured on or after January 1, 2017, and sold in California, to be capable of being decrypted and unlocked by its manufacturer or operating system vendor,” the bill says. “You can get a warrant for pretty much anything and everything, but not for an iPhone or an iPad.” “Ninety-nine percent of the public will never have their phone searched with a court order. Blogs - Adam Curtis - NOW THEN.
THE EXILED – MANKIND'S ONLY ALTERNATIVE. Henry Kissinger on the Assembly of a New World Order - WSJ. The War Nerd: Today is the 200th anniversary of the wimpy so-called burning of Washington. By Gary Brecher On August 24, 2014 Editor’s note: This is a slightly edited version of an article first published by NSFWCORP (now part of Pando) as part of The War Nerd’s Guide to the War of 1812.
Today is the 200th anniversary of the burning of the White House in 1814. People talk about how the British troops “burned Washington” after the Battle of Bladensburg left D. C. wide open, but really, Americans have no idea how easy we got off. The British took it very, very easy on us, just like they did in the Revolutionary War. The occupation of D. There, that tells you right there how easy we had it. Searching for a hitman in the Deep Web. With the arrest of alleged Silk Road mastermind Ross Ulbricht in San Francisco last week, there's been a renewed spotlight on the shadowy network of the Deep Web, the sites accessible only through the encrypted Tor network.
Granted the cover of anonymity, users there engage in activities ranging from expressing political dissent to selling massive amounts of marijuana. While most of the attention has been paid to the trafficking of illegal narcotics, even a quick tour through the Deep Web shows the prevalence of another type of clandestine service: contract killers. These sites, with URLs consisting of random sequences of alphanumeric characters, can't be viewed with traditional Web browsers. A Tor browser, which routes users' information through a system of nodes around the world rendering people using the service effectively anonymous, is required to obtain access. "I do not know anything about you, you do not know anything about me.
Click to enlarge Photo by Lasse Havelund/Flickr. Not man enough? Buy a gun. Semi-automatic rifles like this one are being marketed as a pathway to manliness.
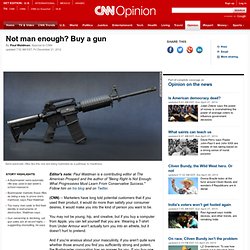
A Bushmaster semi-automatic rifle was used in last week's school massacreBushmaster markets those rifles as being a way to prove one's manhood, says Paul WaldmanToo many men seek to find their identity in instruments of destruction, Waldman saysGun ownership is declining, yet gun sales are at record highs -- suggesting stockpiling, he says Editor's note: Paul Waldman is a contributing editor at The American Prospect and the author of "Being Right Is Not Enough: What Progressives Must Learn From Conservative Success. " Follow him on his blog and on Twitter. (CNN) -- Marketers have long told potential customers that if you used their product, it would do more than satisfy your consumer desires, it would make you into the kind of person you want to be. You may not be young, hip, and creative, but if you buy a computer from Apple, you can tell yourself that you are. Paul Waldman Hernandez: More guns not the answer.
Nigerian scam. 419 scams are a type of fraud and one of the most common types of confidence trick.
There are many variations on this type of scam, including advance-fee fraud, Fifo's Fraud, Spanish Prisoner Scam, the black money scam and the Detroit-Buffalo scam. The number "419" refers to the article of the Nigerian Criminal Code dealing with fraud.[1] The scam has been used with fax and traditional mail, and is now used with the internet. Anders Breivik's Closing Statement, Final Day (June 22, 2012) Front page of a Danish newspaper 5,107 words Translated and annotated by Andrew Hamilton Translator’s Note: The terrorism trial of Norwegian revolutionary nationalist Anders Behring Breivik, 33, began in Oslo District Court in Norway on April 16, 2012, and concluded on June 22, 2012, a month earlier than planned.