

Anonymity Online. Base64 Online - base64 decode and encode. This online sample demonstrates functionality of a base64 property, ByteArray class and Huge asp file upload.
You can convert texts using several code pages (using CharSet property) from Unicode string to byte array and then convert the binary data to a Base64 string. The sample uses a special Base64 algorithm written for the ByteArray class. The Base64 conversion algorithm is written in C++ and works with binary (VT_ARRAY | VT_UI1) and String (BSTR) OLE data. It contains hi-speed and low-memory consumption BSTR->BSTR, BSTR->BINARY, BINARY->BSTR and BSTR->BSTR algorithms. Source code of the coding algorithm is available within distribution license of a ScriptUtilities library. Another online samples (utilities, converting, upload) On-line base64 decoder and encoder - let's you convert text data and files from/to a Base64 string.
SQL Injection. Welcome to another edition of Security Corner.
This month's topic is SQL injection, an attack vector that frequents the minds of PHP developers, but for which there is a shortage of good documentation. Most web applications interact with a database, and the data stored therein frequently originates from remote sources. Thus, when creating an SQL statement, you often use input in its construction. A typical SQL injection attack exploits this scenario by attempting to send fragments of valid SQL queries as unexpected values of GET and POST data. This is why an SQL injection vulnerability is often the fault of poor filtering and escaping, and this fact cannot be stressed enough. This article explains SQL injection by looking at a few example attacks and then introducing some simple and effective safeguards. SQL Injection For a moment, place yourself in the role of an attacker.
Figure 1: In order to get more information about this form, you view the source: Toggle Code View chris' /* chris' /* Sqlninja - a SQL Server injection & takeover tool. While sqlninja can be extremely effective in your penetration tests, is not a trivial tool to setup and use. While this is a good thing to keep script kiddies at bay, it can be also a problem for security professionals that have to deal with short deadlines. Therefore, here are a couple of flash movies that should make things a little clearer for people that have never used this tool before.
Sqlninja basic demo A demo of all basic features: How to configure the tool How to fingerprint the remote server How to bruteforce the 'sa' password How to upload executables and obtain a shell GUI access demo A demo of the integration of sqlninja and metasploit, showing how to start from a simple SQL Injection to finally obtain a full GUI access on the remote DB server.
Both demos will open a new window. Injection SQL tuto sur les failles de type injection sql. Home > tutoriel-injection-sql Voici un tutoriel sur l'injection SQL sous MySQL et MS SQL server.
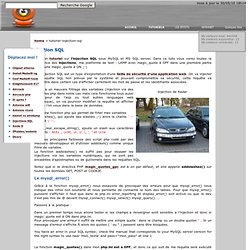
Dans ce tuto vous verez toutes la puissance des injections; ma platforme de test : LAMP avec magic_quote à OFF dans une première partie et ensuite magic_quote à ON ;-) Une injection SQL est un type d'exploitation d'une faille de sécurité d'une application web. On va injecter une requête SQL non prévue par le système et pouvant compromettre sa sécurité, cette requête va permettre dans certain cas d'afficher carrement les mot de passe et les identifiants associées. Injection de Radar Grâce a un mauvais filtrage des variables (injection via des variables php dans notre cas mais cela fonctionne tous aussi bien pour de l'asp ou tout autres languages web dynamique), on va pourvoir modifier la requête et afficher ce que l'on veux dans la base de données.
Voici une fonction php qui permet de filter mes variables addslashes(), qui ajoute des slashes ;-) alors la chaîne ' -- devient \' --. Le mysql_error()