nvert between Latitude/Longitude & OS National Grid Reference points
Some people have asked me about converting between latitude/longitude & Ordnance Survey grid references. The maths is extraordinarily complex, but the Ordnance Survey explain the resulting formulae very clearly in Annex C of their Guide to coordinate systems in Great Britain. OS Grid References are based on 100km grid squares identified by letter-pairs, followed by digits which identify a sub-square within the grid square, as explained on the OS Interactive Guide to the National Grid. 6-digit references identify 100m grid squares; 8 digits identify 10m grid squares, and 10 digits identify 1m squares. TG51401317 represents a 10m box with its (south-west) origin 51.40km across, 13.17km up within the TG square. Before going further, I have to mention that, at a fine level of accuracy, there are different ways of measuring latitude & longitude. The Ordnance Survey uses ‘OSGB-36’, based on an elliptical model of the earth’s surface which is a good fit to the UK.
Блокнот
As of July 2012, Google Notebook has shut down and all Notebook data should now be in Google Docs. As previously announced, in most cases we were able to automatically export the Notebook data, so please visit Google Docs. Also please update any bookmarks or links to Notebook so that they point to Docs instead. Here are answers to some questions about this transition.
Education
Education Article II of the GeocacheAlaska! Inc. by-laws states the reasons for founding our organization are to: To meet the heavy commitment to train and educate, GeocacheAlaska! is in the process of creating training materials for use by all geocachers. The information will be first presented at GeoEducation Events hosted at several Alaskan locations and then posted here in portable document format (pdf) for all geocachers' use and reference.
GlobalLogic - Ukraine - G-Club Program
В конце октября харьковский офис GlobalLogic отпраздновал 10 лет сотрудничества с компанией Physio-Control. Это событие знаменательно не только потому, что Physio-Control — один из старейших и наиболее преданных клиентов GlobalLogic, но и потому, что работа с этой компанией открыла нам двери на рынок здравоохранения. Ведь для разработки и поддержки медицинских проектов недостаточно просто опыта в создании программного обеспечения. Надежность, стабильность и качество становятся определяющими факторами, когда идет речь о спасении человеческих жизней.
Range Finder Tool on a Map
Range Finder Use the ranger finder tool to find out the end point on a map when you specify a start point, a bearing and a distance. Range Finder Map Map Data Map Satellite
Сексология- ИЗБРАННЫЕ КНИГИ
Где купить книги? Читатели спрашивают, где можно купить мои книги. Книга "Подростковая сексуальность на пороге XXI века" (2001), по сведениям издательства Феникс+, в Москве продается: ТД Библиоглобус (М "Лубянка") Молодая Гвардия (М "Полянка") Московский дом книги , это на Новом Арбате Дом Деловой книги (ул. Марксистская) Дом книги на Соколе по остальным магазинам Москвы информация отсутствует ввиду того, что поставки осуществляет книготорговая фирма "Мастер-книга", а также в книготорговых фирмах (это оптовые структуры): ЦПЛ (Центр прикладной литературы) ул.
Smithy code
How the code works[edit] The letters in question are part of the actual text of the judgement, but italicised in contrast to the rest of the text. The following sequence of unusually italicised letters can be extracted from the judgement document: s m i t h y c o d e J a e i e x t o s t g p s a c g r e a m q w f k a d p m q z v The italicised letters only occur up to paragraph 43 (which is page 13 of a 71-page document). Meanwhile, paragraph 52 concludes with this sentence: "The key to solving the conundrum posed by this judgment is in reading HBHG and DVC."
Фокусы от Олега Степанова
Современная Энциклопедия фокусов Переводы зарубежных статей по фокусам c сайта All Magic. Полный Курс Фокусов Марка Вилсона Марк Вилсон. Современная Магия Профессор Хоффман.
The Black Chamber - Chamber Guide
As you enter each section of the Black Chamber, you typically encounter a new code. Each page will contain an explanation of how the code works, some history that puts the code in context, and an interactive tool that will allow you to encrypt and decrypt messages. The interactive tools allow you to type in a message and you can often encrypt it letter by letter or with a single mouse click. You can print the encrypted message or you can cut and paste it into an email and send it to a friend, who can decode the message by visiting the website.
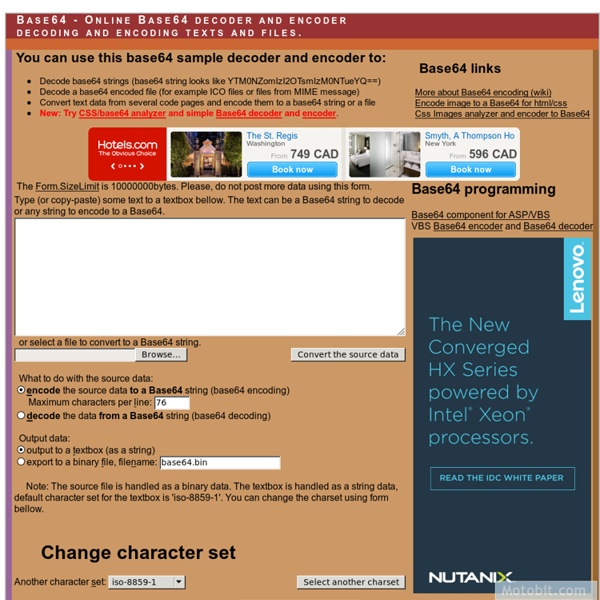
Useful websites for puzzle solving
This is just a collection of links to websites that I've found to be useful in solving various puzzle based geocaches. It's not intended to be a puzzle solving guide, but I have included some links to guides where appropriate. It's also a somewhat selective collection, as it concentrates on less common and more powerful tools. WARNING: I have no control over the pages that are linked to from this site. I have tried most of them myself without any problems, but over time, things change.