

David
Domain/IP/Blacklist. Capture the Flag/Wargames. CTF. The Top 100 Alternative Search Engines. Written by Charles S.
Knight, SEO, and edited by Richard MacManus. The Top 100 is listed at the end of the analysis. Ask anyone which search engine they use to find information on the Internet and they will almost certainly reply: "Google. " Look a little further, and market research shows that people actually use four main search engines for 99.99% of their searches: Google, Yahoo! , MSN, and Ask.com (in that order). But it's not just the sheer number of them that makes them worthy of attention; each one of these search engines has that standard "About Us" link at the bottom of the homepage. The Search Homepage In order to address their claims systematically, it helps to group them into categories and then compare them to their Google counterparts.
Google has successfully made their site the front door through which everyone passes in order to access the Internet. A second example comes from Simply Google. Artificial Intelligence Clustering Engines Recommendation Search Engines The Top 100. Internet Archive: Wayback Machine. Live Hangout Schedule - EducationOnAir. IdiomSite.com - Find out the meanings of common sayings. 100 Little Ways You Can Dramatically Improve Your Writing.
WiFi Info Gathering. D0CS_Forensic_Computing. Security. Web site Tutorials. Informatique. Lessons learned writing digital forensics tools. Hack a Day — Fresh hacks every day. InterN0T - Underground Security Training. How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine.
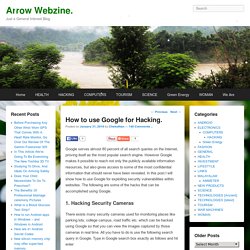
However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. The following are some of the hacks that can be accomplished using Google. 1. Hacking Security Cameras There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time. Inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. you now have access to the Live cameras which work in real-time. Intitle:”Live View / – AXIS” 2. 3. . “? The Best Hacking Tutorial Sites - Learn Legal Hacking.
How to Break Into a Windows PC (and Prevent It from Happening to You) How to use Google for Hacking. Google serves almost 80 percent of all the search queries on the Internet, proving itself as the most popular search engine.
However, Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post, you will find the information on how to use Google for exploiting security vulnerabilities that exists within many websites. The following are some of the ways to use Google for hacking: 1. Cozy, a personal cloud you can hack, host and delete. Hacker Attack Tools. Distributed Denial of Service (DDoS) Attacks/tools. - Knowledge Should be Shareable Software Tricks, Tips and Hacking.
- Knowledge Should be Shareable Software Tricks, Tips and Hacking. How Hackers Protect Themselves From Getting Hacked. When Adrian Lamo goes online, he leaves nothing to chance.
To log in to personal accounts, he uses a digital password generator -- a plastic key chain-like device that displays a new string of digits every 60 seconds. He adds an extra layer of security to some accounts by entering a special code that he receives via text message. And he uses browser extensions to avoid downloading malware by accidentally visiting dangerous Web sites. Some techniques “may seem like a ‘Mission Impossible’ level of security to the average user," Lamo said. But the average user could learn a thing or two from hackers like Lamo, who are not only skilled at breaking into others' PCs, but have devised sophisticated -- in some cases, extreme -- methods for protecting their own. Is not available. Hack a Day — Fresh hacks every day. Cool Websites, Software and Internet Tips. The Best Hacking Tutorial Sites - Learn Legal Hacking. About Hacking. Hacking tutorials sites & tools.
Cyber Situational Awareness. Course Catalog for Online Classes. Free Online College Courses from Top Universities. Free Online College Courses from Top Universities. Big Data University. Learn. Digital Analytics Fundamentals - - Unit 2 - Getting started with digital analytics. Analytics Academy Login Unit 2 - Getting started with digital analytics The importance of digital analytics Text Version Lesson objectives Understand what "digital measurement" meansRecognize why digital analytics tools like Google Analytics are important to implement for your business Additional resources Activity 2.1 - The importance of digital analytics Complete the definition of "digital analytics" by choosing the best option to fill in the blanks for the statement below.
Previous Page Next Page. Digital Analytics Fundamentals - Analytics Academy Courses. Web site Tutorials. Websites for Learning Programming. Websites for Learning Programming. Go Hacking - StumbleUpon. Need to hack someone’s Facebook password?

Well, you’re at the right place! In this post I’ll show you some of the possible ways to hack Facebook password. Also, at the end of this post, I will be discussing. IT Security Cookbook - Firewalls: Securing external Network connections. Summary: A quick guide to firewalls If you just want to connect to the Internet to browse the Web and exchange email for a few users, forget a firewall.

Just setup a non-networked PC with simple dialup access to a service provider. Install a simple personal firewall like BlackICE. Unplug the modem when the PC is not in use. Solaris/SunOS: Use the instructions in sp/Solaris_hardening.html or sp/Solaris_hardening3.html to strip unnecessary services from the system. Introduction Firewalls are a vast and complex subject, of which a limited overview is presented here.
This section concentrates heavily on Internet Firewalls, although a Firewall can (and should) be used between any two networks of different security levels / domains. What is a Firewall? A packet filter stops or allows packets to flow between two networks according to predefined rules. Introducing 35 Pentesting Tools Used for Web Vulnerability Assessment. The Best Hacking Tutorial Sites - Learn Legal Hacking. Meet boxopus. Codecademy Online Tutorials. Open Source Intelligence. Windows Tools For Penetration Testing. Most penetration testers are using either a Mac or a Linux-based platform in order to perform their penetration testing activities.However it is always a good practice to have and a Windows virtual machine with some tools ready to be used for the engagement.The reason for this is that although Windows cannot be used as a main platform for penetration testing some of the utilities and tools can still help us to extract information from our windows targets.So in this post we will see some of the tools that we can use in our windows system.
HashCheck Shell Extension The HashCheck Shell Extension makes it easy for anyone to calculate and verify checksums and hashes from Windows Explorer. In addition to integrating file checksumming functionality into Windows, HashCheck can also create and verify SFV files (and other forms of checksum files, such as .md5 files). Everything is Vulnerable. SecurityXploit: Pentest. Web-sorrow - Linux Am Saturday, 19.
May 2012 im Topic 'Pentest' A perl based tool used for checking a Web server for misconfiguration, version detection, enumeration, and server information. I will build more Functionality in the future. what is's NOT: Vulnerably scanner, inspection proxy, DDoS tool, exploitation framework. It's entirely focused on Enumeration and collecting Info on the target server basic: perl Wsorrow.pl -host scanme.nmap.org -S look for login pages: perl Wsorrow.pl -host 192.168.1.1 -auth CMS intense scan: perl Wsorrow.pl -host 192.168.1.1 -Ws -Cp all -I most intense scan possible: perl Wsorrow.pl -host 192.168.1.1 -e -ua "I come in peace" Cyber Security and Information Systems Information Analysis Center. Update Your Browser. Update Your Browser. Cheat Sheet : All Cheat Sheets in one page.
Excess XSS: A comprehensive tutorial on cross-site scripting - Vimperator. Resources. Hacking Tools / Downloads / Scripts & Codes. Hacking Tools / Downloads / Scripts & Codes. Ethical Hacking. Ethical Hacking. Programming. Programming. Network Science. H@cking. Web Tools. Programming. Cyber Counter Culture. Cyber-Communities. Cyber lyfe. Cyber Dic. US defense and cyber information. Cyber Tech. Cyber war/security. Cyber Crime Foresics. Cyber Security Threats. Cyber Situational Awareness. Cyber Security. Tutorials, training & CTF. Hackables/CTF/Games/Etc | IT Security.