

ESP32’s Wi-Fi Range Extended to 10 km with a Directional Antenna. The relevant test (for readers within China, please click here) took place in the area around the historical site of Hohenneuffen Castle, which was chosen as an easy-to-target landmark with optimal line of sight between the transmitter and the receiver.

Approximately 10 km away from Hohenneuffen Castle, then, ESP32 was connected to an OV2640 module.To decide on the kind of antennas that should be used for this setup, the Friis Equation proved to be particularly helpful: Pr = Pt Gt Gr (λ/4πR)² In general, this equation can be used to estimate the strength of received signs, where lambda (λ) is the wavelength, Pt is the signal power at the transmitter’s end, and Pr is the signal power at the receiver’s end. Gt and Gr are their respective antenna gains. Jeija/esp32free80211: Send arbitrary IEEE 802.11 frames with Espressif's ESP32. Problem loading page. Networking - How to put Mac OS X wireless adapter in monitor mode. Show me your SSID's, I'll Tell Who You Are! - /dev/random. The idea of this article came from a colleague of mine.
He wrote a first version of the script described below. I found it very useful and asked his permission to re-use it and to write this blog article. Thanks to him! In the mean time, during my researches, I also found that a friend, Didier Stevens, published on his blog the same kind of script but for an AirCap adapter. Mine uses any adapter capable to be switched to “monitor” mode. All devices have Wi-Fi interfaces (laptops, tablets, mobile phones, consoles, etc) and their operating systems have features to easily manage the wireless networks you connect them to. This database may contains a lot of interesting data. (Click to enlarge) By default, when a new wireless network is configured, the flag “auto-connect” is enabled.
Beacon,Probe Requests,Probe Responses,Association Requests,Reassociation Requests “Probe Requests” are very interesting to be captured to detect the SSID’s already configured and used by people. Usage: . !! Networking - How to put Mac OS X wireless adapter in monitor mode. Wireless - Phones broadcast the SSIDs of all networks they have ever connected to. How can these be obtained by an attacker? My approach to this was to use an OpenWRT (could be done with DDwrt or other similar projects) device (a TPlink 3600) and to use only tcpdump and monitor mode (not airodump).
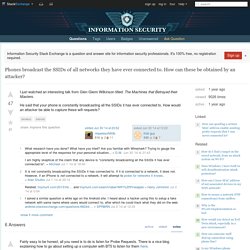
Using TCPdump lets you see all traffic (to profile area activity as well as watching for beacons/probes) The advantage to using a dedicated device is they are inexpensive, use little electricity, and have two radios that work independently. I used a flash drive mounted on /media/drive1 to hold the files. The below commands will watch channel 11 on the b/g/n bands and channel 149 on the a/n bands, obviously this can be changed to suit local needs. With this running at startup you can move the device to the desired area, plug it in, wait, and then unplug it and review the files from the flash drive on your PC. The possible wireless security audit scenarios with this platform are many. How I cracked my neighbor’s WiFi password without breaking a sweat. Last week's feature explaining why passwords are under assault like never before touched a nerve with many Ars readers, and with good reason.

After all, passwords are the keys that secure Web-based bank accounts, sensitive e-mail services, and virtually every other facet of our online life. Lose control of the wrong password and it may only be a matter of time until the rest of our digital assets fall, too. Take, for example, the hundreds of millions of WiFi networks in use all over the world. If they're like the ones within range of my office, most of them are protected by the WiFi Protected Access or WiFi Protected Access 2 security protocols. In theory, these protections prevent hackers and other unauthorized people from accessing wireless networks or even viewing traffic sent over them, but only when end users choose strong passwords. First, the good news. That's not to say wireless password cracks can't be accomplished with ease, as I learned firsthand.