

Gallery: How networks help us understand the world. As designer Manuel Lima points out in his TED Talk, A visual history of human knowledge, the network has become a powerful way to visualize much of what is going on in the world around us.
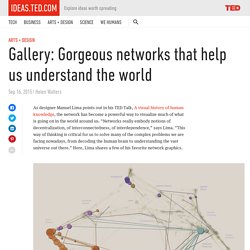
“Networks really embody notions of decentralization, of interconnectedness, of interdependence,” says Lima. “This way of thinking is critical for us to solve many of the complex problems we are facing nowadays, from decoding the human brain to understanding the vast universe out there.” Turnitin and SafeAssign plagiarism detection programs: Why are they all ineffective? Photo illustration by Juliana Jiménez.

Photo by Chris Boswell/Thinkstock Plagiarism detection software from vendors such as Turnitin is often criticized for labeling clumsy student writing as plagiarism. Long Live the Web: A Call for Continued Open Standards and Neutrality. Digital Copyright. Published by Baltimore, Maryland Internet and Media Attorneys. » A Speculative Post on the Idea of Algorithmic Authority Clay Shirky. Jack Balkin invited me to be on a panel yesterday at Yale’s Information Society Project conference, Journalism & The New Media Ecology, and I used my remarks to observe that one of the things up for grabs in the current news environment is the nature of authority.

In particular, I noted that people trust new classes of aggregators and filters, whether Google or Twitter or Wikipedia (in its ‘breaking news’ mode.) I called this tendency algorithmic authority. I hadn’t used that phrase before yesterday, so it’s not well worked out (and I didn’t coin it — as Jeff Jarvis noted at the time, Google lists a hundred or so previous occurrences.) The Baloney Detection Kit: Carl Sagan’s Rules for Bullshit-Busting and Critical Thinking.
Carl Sagan (November 9, 1934–December 20, 1996) was many things — a cosmic sage, voracious reader, hopeless romantic, and brilliant philosopher.

But above all, he endures as our era’s greatest patron saint of reason and critical thinking, a master of the vital balance between skepticism and openness. In The Demon-Haunted World: Science as a Candle in the Dark (public library) — the same indispensable volume that gave us Sagan’s timeless meditation on science and spirituality, published mere months before his death in 1996 — Sagan shares his secret to upholding the rites of reason, even in the face of society’s most shameless untruths and outrageous propaganda. Through their training, scientists are equipped with what Sagan calls a “baloney detection kit” — a set of cognitive tools and techniques that fortify the mind against penetration by falsehoods: Web Literacy - Information Literacy Quiz. Critical-thinking - Taxonomy. Jamie Bartlett: How the mysterious dark net is going mainstream.
LiveLinks - Research Strategies. Turnitin, "The Sources in Student Writing – Higher Education (White Paper)": 1.5 Information today – The state of the art 1.5.1 Books Google books,

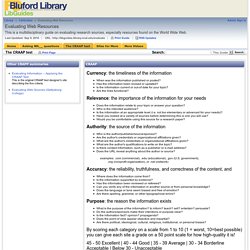
First-Year Seminar Program. About the Module The CRAAP Test module helps students learn the difference between appropriate and inappropriate sources for papers and bibliographies by prompting them to evaluate five basic elements of the sources: Currency, Relevance, Authority, Accuracy, and Purpose.
Morningside Center for Teaching Social Responsibility. By Alan Shapiro "Warning: Several shipments of bananas from Costa Rica have been infected with necrotizing fasciitis, otherwise known as flesh-eating bacteria.
Recently this disease has decimated the monkey population in Costa Rica...and has been able to graft itself to the skin of fruits in the region, most notably the banana....It is advised not to purchase bananas for the next three weeks.... "The skin infection from necrotizing fasciitis is very painful and eats two to three centimeters of flesh per hour. Amputation is likely, death is possible....The FDA has been reluctant to issue a countrywide warning because of fear of nationwide panic. They have secretly admitted that they feel upwards of 15,000 this will affect Americans but that these are acceptable numbers. My grandson Eli forwarded this email to my wife Sue a couple of years ago with a preface that read, "Received this from a good source.
" Crap Detection 101 - City Brights: Howard Rheingold. “Every man should have a built-in automatic crap detector operating inside him.”
Ernest Hemingway, 1954 The answer to almost any question is available within seconds, courtesy of the invention that has altered how we discover knowledge – the search engine. Materializing answers from the air turns out to be the easy part – the part a machine can do. The real difficulty kicks in when you click down into your search results. At that point, it’s up to you to sort the accurate bits from the misinfo, disinfo, spam, scams, urban legends, and hoaxes. Unless a great many people learn the basics of online crap detection and begin applying their critical faculties en masse and very soon, I fear for the future of the Internet as a useful source of credible news, medical advice, financial information, educational resources, scholarly and scientific research.
EmeraldInsight. Craap_worksheet.pdf. Eval_websites.pdf. The CRAP test for evaluating sources. I frequently blog about evaluating sources— it was the subject of my very first post–so it should come as no surprise that I liked “Crap Detection, A 21st Century Literacy” from the Libraries and Transliteracy blog, which I found through the Librarian in Black.

I wanted to point out two great items featured in the post: Howard Rheingold’s “Crap Detection 101,” and the librarian-created CRAP test for evaluating sources based on “Currency, Reliability, Authority and Purpose/Point of View”: CurrencyHow recent is the information? How recently has the website been updated? Is it current enough for your topic? The CRAAP test - Evaluating Web Resources - LibGuides at North Carolina Agricultural & Technical State University. Currency: the timeliness of the information When was the information published or posted?
Chucking the Checklist: A Contextual Approach to Teaching Undergraduates Web-Site Evaluation. Find using OpenURL Buy This Issue. PIP_Privacy_management_on_social_media_sites_022412.pdf. The Privacy Jungle: On the Market for Data Protection in Social Networks. Perspectives%20on%20Psychological%20Science-2012-Wilson-203-20.pdf. Internet and Surveillance: The Challenges of Web 2.0 and Social Media - Christian Fuchs, Kees Boersma, Anders Albrechtslund, Marisol Sandoval.
p763-wang.pdf?ip=168.28.2. 16. Self-protection is behavior that seeks to prevent or reduce the likelihood of embarrassment, difficult questions, and feelings of vulnerability. Self-protection results in teenage patients avoiding mention of their diagnosis and treatment in their activities on Facebook. Self-protection has also a temporal dimension, as the need for protection changes over time (box 5).v Box 5 Self-protection Finding 14. “Well, I don't really think it is anyone's business on Facebook. Finding 15. Teens, Social Media, and Privacy. Teens, Social Media, and Privacy Teens share a wide range of information about themselves on social media sites; indeed the sites themselves are designed to encourage the sharing of information and the expansion of networks. However, few teens embrace a fully public approach to social media. Instead, they take an array of steps to restrict and prune their profiles, and their patterns of reputation management on social media vary greatly according to their gender and network size.
These are among the key findings from a new report based on a survey of 802 teens that examines teens’ privacy management on social media sites: JuncoClassStandingFBJADP. Facebook gets real with the kids over that privacy thing. Facebook is partnering with the National Association of Attorneys General in the US to launch a privacy awareness campaign for teenagers. This could well be a disaster in the making so Privacy Surgeon decided to create this helpful template and translation so out-of-touch executives and lawmakers can reach the right demographic. Bless-up dudes! (Translation: Dear Facebook user) We wanna do some real talk about the privacy thing.
The yute don’t want some wanksta jackin’ their info, so here’s some advice. The Privacy Blog - Privacy, Security, Cryptography, and Anonymity The Privacy Blog. Helping Your Kids Understand Social Media Privacy Settings - Sue Scheff BlogSue Scheff Blog. Our kids are growing up in an age when sharing is ubiquitous and encouraged. But kids aren’t born understanding how to manage social media privacy settings or why it’s important to do so. It’s up to us as parents to guide them, just the same as teaching them how to cross the street or to stay away from strangers.
Messer-Polis-jt-suppt-ltr-07062015.pdf. Privacy. Consumer Watchdog. Facebook Is Now Selling Your Web-Browsing Data To Advertisers. Access to Social Media Usernames and Passwords. Increasing numbers of Americans use social media both on and off the job. Reports of employers asking employees to turn over their usernames or passwords for their personal accounts prompted concerns among some lawmakers. Some employers argue that access to personal accounts is needed to protect proprietary information or trade secrets, to comply with federal financial regulations, or to prevent the employer from being exposed to legal liabilities. But others consider requiring access to personal accounts an invasion of employee privacy. State lawmakers introduced legislation beginning in 2012 to prevent employers from requesting passwords to personal Internet accounts to get or keep a job. Privacy and Social Media: It’s Complicated. Social Networking Advice for Teenagers: Protect your Privacy.
Facebook, Instagram, and Social Parent Concern. No thanks. Teaching Kids to Be Smart About Social Media. Social Networking Privacy. Latest News/Events With New Policy Changes, Facebook Tracks Users Across the Web: Over the objections of consumer privacy organizations, Facebook has implemented policy changes that allow the company to track users across the web without consent. Privacy and Social Media: It’s Complicated. Facebook Privacy Tips. Welcome to Forbes. Data Science: What the Facebook Controversy is Really About - Sara M. Watson. Technology The Facebook contagion study raises a lot of questions. But what does it mean for this thing we call data science? This Is Who Facebook Thinks You Are. How to Think about Privacy: An Interview with Jaron Lanier. Should Parents Post Pictures of Their Kids on Facebook? 11 ways to protect your privacy on Facebook. Use of Facebook and Twitter in social science research distorts studies -
Technology - DIGITAL COMMERCE - As privacy grows scarcer on the Internet, people finally start to take notice. Privacy issues of social networking sites. Social media research raises privacy and ethics issues. Kids' online privacy: Debate over sharing photos. Data Use Policy. Privacy Policy – Privacy & Terms – Google.