

David Cameron to close gap in oversight of mass surveillance. David Cameron has moved to close a hole in the oversight of Britain’s intelligence agencies after it was revealed for the first time that they were creating “bulk personal datasets” containing millions of items of personal information, some of it gathered covertly without any statutory accountability.
The Great SIM Heist: How Spies Stole the Keys to the Encryption Castle. AMERICAN AND BRITISH spies hacked into the internal computer network of the largest manufacturer of SIM cards in the world, stealing encryption keys used to protect the privacy of cellphone communications across the globe, according to top-secret documents provided to The Intercept by National Security Agency whistleblower Edward Snowden.

The hack was perpetrated by a joint unit consisting of operatives from the NSA and its British counterpart Government Communications Headquarters, or GCHQ. The breach, detailed in a secret 2010 GCHQ document, gave the surveillance agencies the potential to secretly monitor a large portion of the world’s cellular communications, including both voice and data. The company targeted by the intelligence agencies, Gemalto, is a multinational firm incorporated in the Netherlands that makes the chips used in mobile phones and next-generation credit cards. In all, Gemalto produces some 2 billion SIM cards a year. Its motto is “Security to be Free.” Requests for user information – Google Transparency Report. Like other technology and communications companies, Google regularly receives requests from governments and courts around the world to hand over user data.
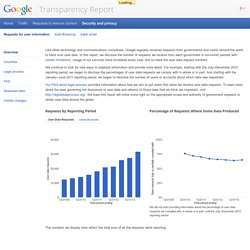
In this report, we disclose the number of requests we receive from each government in six-month periods with certain limitations. Usage of our services have increased every year, and so have the user data request numbers. We continue to look for new ways to organize information and provide more detail. For example, starting with the July–December 2010 reporting period, we began to disclose the percentages of user data requests we comply with in whole or in part. And starting with the January–June 2011 reporting period, we began to disclose the number of users or accounts about which data was requested. Our FAQ about legal process provides information about how we aim to put users first when we receive user data requests. Requests by Reporting Period. Report-ponemon-2014-exposing-cybersecurity-cracks-en. The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013. 2014 Verizon Data Breach Investigations Report (DBIR) NSA broke privacy rules thousands of times per year, audit finds.
The National Security Agency has broken privacy rules or overstepped its legal authority thousands of times each year since Congress granted the agency broad new powers in 2008, according to an internal audit and other top-secret documents.
Most of the infractions involve unauthorized surveillance of Americans or foreign intelligence targets in the United States, both of which are restricted by statute and executive order. They range from significant violations of law to typographical errors that resulted in unintended interception of U.S. e-mails and telephone calls. The documents, provided earlier this summer to The Washington Post by former NSA contractor Edward Snowden, include a level of detail and analysis that is not routinely shared with Congress or the special court that oversees surveillance. In one instance, the NSA decided that it need not report the unintended surveillance of Americans. Read the documents FISA court finds illegal surveillance What's a 'violation'? A Possible Explanation For How U.S. Diplomat's Call Was Tapped. U.S.
Assistant Secretary of State Victoria Nuland leaves a news conference at the U.S. Embassy in Kiev on Friday. A phone call of hers about Ukraine was leaked on the Internet. Gleb Garanich/Reuters/Landov hide caption itoggle caption Gleb Garanich/Reuters/Landov U.S. Gleb Garanich/Reuters/Landov An American diplomat got in trouble for saying something, well, undiplomatic.
Victoria Nuland, a top State Department official, thought she was having a private phone conversation. It turned out their conversation was being recorded. Nuland is traveling in Kiev, and at a press conference earlier today, she refused to comment on what she called a "private diplomatic conversation. " U.S. Whoever is responsible, how might they have done it? "Somehow this phone was tapped," says Richard Bejtlich, a chief security strategist at cybersecurity company FireEye and a fellow at the Brookings Institution. A Secure Line? MSRT March: Superfish cleanup - Microsoft Malware Protection Center. This month we added two new families to the Microsoft Malicious Software Removal Tool: Win32/CompromisedCert and Win32/Alinaos.

The Alinaos trojan family targets point-of-sale terminals to steal credit card information. This blog will discuss the security risk presented by Superfish, an ad-injecting application that we detect as CompromisedCert. Some new Lenovo consumer notebooks sold between September 2014 and February 2015 had Superfish pre-installed. In February, it was discovered that this application exposes a machine to man-in-the-middle (MiTM) attacks because of a security vulnerability involving a self-signed root certificate used by Superfish.
Lenovo customers concerned about pre-installed versions of Superfish should refer to Lenovo’s security advisory. Microsoft worked with Lenovo and Superfish to add detection with a root trust repair solution for Superfish to our real time protection products on February 19. Viewcontent.