

Webdesign. BOOTSTRAP. Method Draw. A Product Hacker Toolbox - by Aymeric Rabot. How to get started shipping software into awesome products effectively.

There is a nebula of tools out there. Below is a compilation of some helpful ones that I’ve used over time. Awesome products help make awesome products. Some might require further study but they are all solid tools that you will love using at any level.These resources are trusted by millions of people. You can use them as part of your everyday workflow or just try them once just to know what the world is made of.
Curiosity is one path to progress. The Ultimate Privacy Guide - Best VPN.comBest VPN.com. Find the Best VPNs - Best VPN.comBest VPN.com.
Keepass. Virtualization Administration Guide. Red Hat Enterprise Linux 6 Virtualization Documentation Edition 0.1 Red Hat Engineering Content Services Copyright © 2011 Red Hat, Inc.

The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). Check hardware information on Linux with hwinfo command. Hwinfo The hwinfo command is a very handy command line tool that can be used to probe for details about hardware components.
It reports information about most hardware units like cpu, hdd controllers, usb controllers, network card, graphics cards, multimedia, printers etc. Global DNS Propagation Checker - What's My DNS? CEH Self Study Course Package - Information Security IT Training Course. Forum. Hacking. Metasploit Securite et hacking - Le guide du pentesteur.
How to use proxychains. ProxyChains - TCP and DNS through proxy server. HTTP and SOCKS. Interactive Vim tutorial. SHODAN - Computer Search Engine.
Free & Public DNS Server List (Updated March 2014) By Tim Fisher Updated October 01, 2016.
Your ISP automatically assigns DNS servers when your router or computer connects to the Internet via DHCP... but you don't have to use those. Chapter 12. Storage pools. Suppose a storage administrator responsible for an NFS server creates a share to store guest virtual machines' data.
The system administrator defines a pool on the host physical machine with the details of the share (nfs.example.com:/path/to/share should be mounted on /vm_data). When the pool is started, libvirt mounts the share on the specified directory, just as if the system administrator logged in and executed mount nfs.example.com:/path/to/share /vmdata. If the pool is configured to autostart, libvirt ensures that the NFS share is mounted on the directory specified when libvirt is started. Mémo autohébergement - Phyks.me. Dernière mise à jour : 20 avril 2014, reprise de la partie sur le partitionnement et Owncloud / Firefox Sync / SNI.

Monter son propre serveur n'est pas très compliqué et est même largement accessible pour quiconque a un peu de temps à y consacrer et quelques connaissances sur Linux. Ce guide a été écrit dans l'optique de me servir d'aide-mémoire le jour où je devrai tout réinstaller.
Blog » An installation and everyday usage guide for libvirt and KVM. Why all this ?
Today, nearly every modern computing-related company uses directly or indirectly a virtualization software. As seen with the recent Cloud computing trend, it is a sector that recently exploded in popularity and it is now accessible to everyone. There are now a LOT of alternatives to virtualize an OS : Isolation : OpenVZ, VServer, LXC, UML, BSD jails, Solaris zones…Paravirtualization : XenFull virtualization : VMWare Player/Workstation/ESX/ESXi, KVM/Qemu, Virtualbox, Bochs… When having to deal with a large pack of machines for building packages, testing software on multiple OSes or optimally use a powerful server with lots of RAM, you rapidly should, if not have to, realize that Virtual Machines can make your life significantly easier.
Adding iSCSI storage to KVM. I’m really surprised that I’m the one writing this as there we no flat out simple guides available, maybe it’s just because I’m new to the whole iSCSI thing.
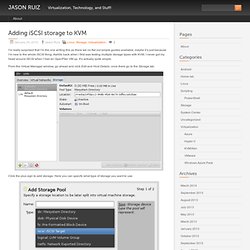
Awhile back when I first was testing multiple storage types with KVM, I never got my head around iSCSI when I had an OpenFiler VM up. It’s actually quite simple. From the Virtual Manager window, go ahead and click Edit and Host Details, once there go to the Storage tab. Index of /debian-cd.
Hadoop. Tricks. Glances gives a quick overview of system usage on Linux. Monitor your Linux system As a Linux sysadmin it feels great power when monitoring system resources like cpu, memory on the commandline.
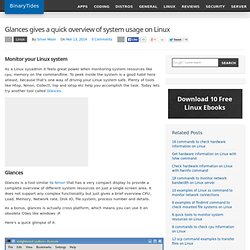
To peek inside the system is a good habit here atleast, because that's one way of driving your Linux system safe. Plenty of tools like Htop, Nmon, Collectl, top and iotop etc help you accomplish the task. Today lets try another tool called Glances. Encrypt DNS Traffic In Linux With DNSCrypt (Via OpenDNS) DNSCrypt, as its name suggests, encrypts DNS traffic between your computer and OpenDNS, in the same way SSL turns HTTP traffic into HTTPS encrypted traffic.
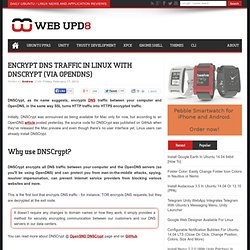
Initially, DNSCrypt was announced as being available for Mac only for now, but according to an OpenDNS article posted yesterday, the source code for DNSCrypt was published on GitHub when they've released the Mac preview and even though there's no user interface yet, Linux users can already install DNSCrypt. Why use DNSCrypt? Welcome to OpenDNS! DNSCrypt home page. How to Boost Your Internet Security with DNSCrypt. Top 20 Nginx WebServer Best Security Practices. Nginx is a lightweight, high performance web server/reverse proxy and e-mail (IMAP/POP3) proxy.
It runs on UNIX, GNU/Linux, BSD variants, Mac OS X, Solaris, and Microsoft Windows. According to Netcraft, 6% of all domains on the Internet use nginx webserver. Nginx is one of a handful of servers written to address the C10K problem. Unlike traditional servers, Nginx doesn't rely on threads to handle requests. 20 Linux System Monitoring Tools Every SysAdmin Should Know.
Need to monitor Linux server performance? Try these built-in commands and a few add-on tools. Most Linux distributions are equipped with tons of monitoring. These tools provide metrics which can be used to get information about system activities. You can use these tools to find the possible causes of a performance problem. The commands discussed below are some of the most basic commands when it comes to system analysis and debugging server issues such as: Information for the World from Outer Space. Learn how to code. FreeNAS 9.1 Setup Guide.
Bitmessage. Pdf. Address Directory. Wiki. Bitmessage. From the Bitmessage wiki: "Bitmessage is a P2P communications protocol used to send encrypted messages to another person or to many subscribers. It is decentralized and trustless, meaning that you need-not inherently trust any entities like root certificate authorities. It uses strong authentication which means that the sender of a message cannot be spoofed, and it aims to hide "non-content" data, like the sender and receiver of messages, from passive eavesdroppers like those running warrantless wiretapping programs.
" MegaHAL. MegaHAL is a computer conversation simulator, or "chatterbot", created by Jason Hutchens. Background[edit] MegaHAL was and made its debut in the 1998 Loebner Prize Contest. Like many chatterbots, the intent is for MegaHAL to appear as a human fluent in a natural language. As a user types sentences into MegaHAL, MegaHAL will respond with sentences that are sometimes coherent and at other times complete gibberish. MegaHAL learns as the conversation progresses, remembering new words and sentence structures.
Backup your files with ubuntu one and Déjà Dup. From their site, What Is Ubuntu one? My Blog: Backing up Ubuntu Using Deja Dup and Amazon Web Services S3. Ubuntu includes a nice backup tool called Déjà Dup based on Duplicity that gives us just the options we need to handle our home backups. Guide Open Source : le référentiel des solutions open source professionnelles. Pack for Firefox 2013: Our List of the Best Extensions. CyanogenMod Downloads. Freedom Through Security » Blog Archive » Edward’s Snowden revelations and implications to VPN Use. There has been many shocking revelations by Edward Snowden including Friday’s disclosure on some of the details on how the NSA (US) and GCHQ (UK) allegedly eavesdrop on the internet.
Ethical Hacking. Linux_hebergement. Preparation · Rackster/ispconfig3-nginx-reverse-proxy Wiki. Beginner's guide on using IRC. The standard IRC client is the original ircII. Howto setup the Ultimate IRC Server — Codeography. Setting Up an Basic IRC Server on Ubuntu « The Tech Tutorial. Comparison of Internet Relay Chat daemons. How to set up ircd-hybrid and hybserv on ubuntu 12.04 : Leonard Austin.
[Tuto] Tor : héberger son "hidden service" ← Open-Freax.