

7 configurações que todo mundo deveria mudar no roteador de casa. Na hora de pensar na segurança dos dispositivos domésticos, muita gente acaba esquecendo do roteador.
E trata-se de um esquecimento perigoso, já que um roteador sem segurança pode ser invadido com muita facilidade. Essa falta de atenção à segurança dos roteadores já permitiu até mesmo que um grupo de hackers criasse uma botnet com roteadores brasileiros para fazer ataques DDoS. As configurações de fábrica do seu roteador, portanto, não são seguras, e é importante que você altere ao menos algumas opções delas.
Para acessá-las, basta abrir um navegador e digitar o endereço do seu roteador na barra de endereços. Em geral, esse endereço é um número que vem escrito na documentação do roteador: 192.168.1.1, 192.168.2.1 e 192.168.1.10 são alguns dos endereços mais comuns, mas esse número varia bastante. After iOS, Opera's Free VPN App is Available for Android Devices. Tutorial: transforme seu computador com Windows 8 em um hotspot WiFi - Vídeos Canaltech. How to Supercharge Your Router with DD-WRT. Routing and Switching. The basics of using a proxy server for privacy and security.
Patrick Lambert goes over the basics of how proxy servers work and why they are used to add security and privacy.
If you work remotely, or have to handle corporate files on the road, then chances are you've used a specific type of proxy and may not even be aware of it. In fact, proxies are used by workers all over the world in the form of a VPN. A virtual private network is one specific type of proxy which provides you with the ability to work remotely and securely. But what is a proxy exactly, how does it work, and what are some of the advantages it can give not only a remote worker, but anyone who wants an extra layer of privacy? Here's a look at the various types of proxies and a review of one particular service which provides you with proxies on steroids. Five free network analyzers worth any IT admin's time. If you work on a network, you then know the value of information.
Solid information leads to a strong and worry-free network (or at least as worry-free as you can manage). In order to gather that information, you need the right tools. The tools I speak of are network analyzers. Once you start looking, you can find analyzers of every shape, size, and price. See what process is using a TCP port in Windows Server 2008. Windows administrators sometimes have to track down network traffic or errant processes and then match that to network traffic.
Here are scripts that will aid in the connectivity forensics at the port and process level. You may find yourself frequently going to network tools to determine traffic patterns from one server to another; Windows Server 2008 (and earlier versions of Windows Server) can allow you to get that information locally on its connections. You can combine the netstat and tasklist commands to determine what process is using a port on the Windows Server. The following command will show what network traffic is in use at the port level: IP subnetting made easy. George Ou explains IP subnetting using his own graphical approach.
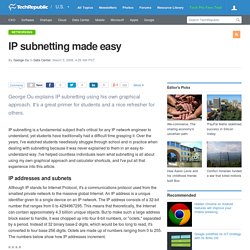
It's a great primer for students and a nice refresher for others. IP subnetting is a fundamental subject that's critical for any IP network engineer to understand, yet students have traditionally had a difficult time grasping it. Quick Tips: Flush the ARP cache in Windows 7. Jack Wallen shows you how to clear the Address Resolution Protocol cache and how to manage that cache with a few command switches.
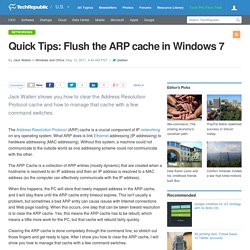
The Address Resolution Protocol (ARP) cache is a crucial component of IP networking on any operating system. What ARP does is link Ethernet addressing (IP addressing) to hardware addressing (MAC addressing). Without this system, a machine could not communicate to the outside world as one addressing scheme could not communicate with the other. The ARP Cache is a collection of ARP entries (mostly dynamic) that are created when a hostname is resolved to an IP address and then an IP address is resolved to a MAC address (so the computer can effectively communicate with the IP address). 10 things you shouldn't do when running network cable. Improperly installed cabling can cripple network performance, create maintenance headaches, and lead to hidden costs.
Here's where things can go wrong. Network cabling can be a finicky thing. Network diagrams highly-rated by IT pros. There is a site called RateMyNetworkDiagram, which allows users to upload their own network diagrams to be rated and critiqued by fellow networking professionals.
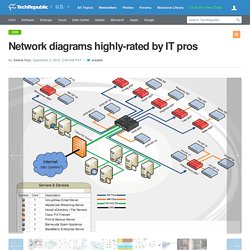
By their permission, I chose these 12 examples of some of the higher-rated diagrams in categories of Large, Small, Home, Network Racks (photos), and Funny. Maybe these will inspire you to get creative with your own network diagram creation. Submitted by user hodgesbo Selena has been at TechRepublic since 2002. She is currently a Senior Editor with a background in technical writing, editing, and research. 10 tips for troubleshooting DNS problems. Figuring out what's wrong with DNS will go faster if you have a set of troubleshooting steps to follow.
Brien Posey shares his approach to isolating the cause of DNS problems. DNS is one of the most essential services on any Windows network. Active Directory can't function without DNS, and it's is also used by any number of other network functions. Harald Haas: Forget Wi-Fi. Meet the new Li-Fi Internet. 10 Ways to Troubleshoot DNS Resolution Issues. Introduction We all need proper DNS resolution for our network applications.
10 Ways to Troubleshoot DNS Resolution Issues. Netcat (UDP Tools -- Unix & Linux) Top 10 Tech Concepts You Always Wanted To Learn About (But Never Did) Store your data on someone else's computer, hope they don't do anything bad with it or decide to shut down. Stallman calls it "Careless Computing". If you put personal data in-the-cloud like future plans., trips, your current GPS location, then you should expect that data to be shared all over the world with nice people, nice companies and criminals (looking for when to rob you).
Facebook connections and twitter followers provide information about you and your friends. If they assume you are similar to your friends, then the personal information those other people enter helps them build a profile of your likes/dislikes too. Photos tagged with your real name provide all sorts of other information that you may not want known to anyone in the world with a computer and internet connection. Open Wireless Movement. NAT. 5 Ways to Secure Your Wireless Router. Sometimes the best thing to say about a wireless router in your house is that once it's set it, you forget it exists. As long as the devices that need the Wi-Fi connection can get on and function, that's all that matters, right? Maybe, but we also live in the age of leaks, wiki and otherwise. If you're worried about the security of your home So what do you do? Follow these tips and you'll be well ahead of most home Wi-Fi users.
Melhore o sinal de sua rede sem fio com essas 10 dicas - Redes. IPv4 Subnetting. IPv6. Networking - How can I find out where an email really came from? Understanding IP Classes - CompTIA Network+ N10-005: 1.3. Substituta do Wi-Fi, rede Li-Fi permite baixar até 30 filmes por segundo - Li-Fi - Economia. Pesquisadores da Universidade de Oxford atingiram um novo patamar de transmissão de dados via Li-Fi, uma espécie de evolução do Wi-Fi que transfere dados por luzes LED.
As informações são do UOL Tecnologia. De acordo com o estudo, a velocidade máxima atingida foi de 224 Gbps (Gigabits por segundo). Com essa capacidade, dá para baixar 30 filmes (de 1,5 gigabyte cada) por segundo. Ethermanage.com.