

Top 10 C Language resources that will turn you into a better programmer. Custom Search People consider computer programming a little tiresome but some find it more enjoyable.

Every programmer has to keep up with the latest trends coming in the programming languages. Most of the programmers start programming in C as it is the most commonly used programming language for writing operating systems and applications. If you are reading this article, most probably you are already a programmer or want to become a programmer. SQL Injection Attacks by Example. A customer asked that we check out his intranet site, which was used by the company's employees and customers.
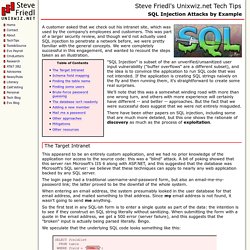
This was part of a larger security review, and though we'd not actually used SQL injection to penetrate a network before, we were pretty familiar with the general concepts. We were completely successful in this engagement, and wanted to recount the steps taken as an illustration. "SQL Injection" is subset of the an unverified/unsanitized user input vulnerability ("buffer overflows" are a different subset), and the idea is to convince the application to run SQL code that was not intended. If the application is creating SQL strings naively on the fly and then running them, it's straightforward to create some real surprises. We'll note that this was a somewhat winding road with more than one wrong turn, and others with more experience will certainly have different -- and better -- approaches.
The Linux System Administrator's Guide. How Browsers Work: Behind the Scenes of Modern Web Browsers. Web browsers are the most widely used software.

In this primer, I will explain how they work behind the scenes. We will see what happens when you type google.com in the address bar until you see the Google page on the browser screen. The browsers we will talk about There are five major browsers used on desktop today: Chrome, Internet Explorer, Firefox, Safari and Opera. On mobile, the main browsers are Android Browser, iPhone, Opera Mini and Opera Mobile, UC Browser, the Nokia S40/S60 browsers and Chrome–all of which, except for the Opera browsers, are based on WebKit. The browser's main functionality The main function of a browser is to present the web resource you choose, by requesting it from the server and displaying it in the browser window. The way the browser interprets and displays HTML files is specified in the HTML and CSS specifications. Browser user interfaces have a lot in common with each other.
The browser's high level structure The browser's main components are (1.1): Advanced Bash-Scripting Guide. How Google Works - Culture Lifestyle. The First Few Milliseconds of an HTTPS Connection. Convinced from spending hours reading rave reviews, Bob eagerly clicked “Proceed to Checkout” for his gallon of Tuscan Whole Milk and… Whoa!

What just happened? In the 220 milliseconds that flew by, a lot of interesting stuff happened to make Firefox change the address bar color and put a lock in the lower right corner. With the help of Wireshark, my favorite network tool, and a slightly modified debug build of Firefox, we can see exactly what’s going on. By agreement of RFC 2818, Firefox knew that “https” meant it should connect to port 443 at Amazon.com: Most people associate HTTPS with SSL (Secure Sockets Layer) which was created by Netscape in the mid 90’s.
Client Hello TLS wraps all traffic in “records” of different types. The next two bytes are 0x0301 which indicate that this is a version 3.1 record which shows that TLS 1.0 is essentially SSL 3.1. The handshake record is broken out into several messages. Server Hello Checking out the Certificate. Algorithm Design. The Basics of C Programming" The C programming language is a popular and widely used programming language for creating computer programs.
Programming, Motherfucker - Do you speak it? Top 10 Ways to be Screwed by "C" To get on this list, a bug has to be able to cause at least half a day of futile head scratching, and has to be aggravated by the poor design of the "C" language.

In the interests of equal time, and to see how the world has progressed in the 20-odd years since "C" escaped from its spawning ground, see my Top 10 Ways to be Screwed by the Java programming language, and for more general ways to waste a lot of time due to bad software, try my Adventures in Hell page. A better language would allow fallible programmers to be more productive.
What is an Operating System?& Not all computers have operating systems.

The computer that controls the microwave oven in your kitchen, for example, doesn't need an operating system. It has one set of tasks to perform, very straightforward input to expect (a numbered keypad and a few pre-set buttons) and simple, never-changing hardware to control. For a computer like this, an operating system would be unnecessary baggage, driving up the development and manufacturing costs significantly and adding complexity where none is required.
Instead, the computer in a microwave oven simply runs a single hard-wired program all the time. For other devices, an operating system creates the ability to: Cheat sheets and programming resources - QuicklyCode. Linux Directory Structure (File System Structure) Explained with Examples. By Ramesh Natarajan on September 8, 2010 Have you wondered why certain programs are located under /bin, or /sbin, or /usr/bin, or /usr/sbin?
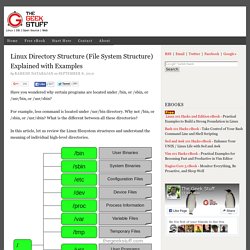
For example, less command is located under /usr/bin directory. Why not /bin, or /sbin, or /usr/sbin?