

It’s Not Just Spying – How the NSA Has Turned Into a Giant Profit Center for Corrupt Insiders. So Americans aren’t entitled to any privacy because of a trumped up terrorist threat, yet top NSA employees can moonlight for private businesses involved in the same areas as the NSA with apparently no threat to national security.

America has gone completely insane. Unsurprisingly, this is just the tip of the crony-capitalist fraud that the NSA has become. In fact, Buzzfeed broke a related story recently. It reports how one of the most powerful individuals at the NSA, Teresa H. Shea., has several intelligence related businesses run from her home. Teresa Shea is the director of Signals Intelligence, or SIGINT, which refers to all electronic eavesdropping and interception, including the controversial domestic surveillance program that collects information about Americans’ phone use.
From Buzzfeed: On a quiet street in Ellicott City, Maryland, a blue-grey two-story clapboard house, set back from the road, is shaded by two sycamores and a towering maple. Go ahead and read that twice. NSA Whistleblower Speaks: “The Ultimate Goal is Total Population Control” At least 80% of fibre-optic cables globally go via the U.S.
This is no accident and allows the US to view all communication coming in. At least 80% of all audio calls, not just metadata, are recorded and stored in the US. NSA Spying. The NSA's next move: silencing university professors? This actually happened yesterday: A professor in the computer science department at Johns Hopkins, a leading American university, had written a post on his blog, hosted on the university's servers, focused on his area of expertise, which is cryptography.
FBI Can Turn On Your Webcam Without You Knowing It. The FBI apparently has the ability to take over your computer’s webcam and your smartphone’s camera and use them to spy on you, according to recent reports.

To make matters worse, you probably wouldn’t realize that you are under surveillance via your own devices, because the agency also can watch without your webcam light even turning on. The FBI has had the ability to take over webcams, microphones and camera phones for several years, The Washington Post discovered. The Rise of Global Digital Surveillance - Spying, Prying and Lying.
By Patrick Henningsen December 27, 2013 from NewDawnMagazine Website Books have been written about [US] President Eisenhower's famous farewell warning in 1961 about the "military-industrial complex," and what he described as its "unwarranted influence.

" But an even greater leviathan today, NSA Spying. The US government, with assistance from major telecommunications carriers including AT&T, has engaged in massive, illegal dragnet surveillance of the domestic communications and communications records of millions of ordinary Americans since at least 2001.
Since this was first reported on by the press and discovered by the public in late 2005, EFF has been at the forefront of the effort to stop it and bring government surveillance programs back within the law and the Constitution. History of NSA Spying Information since 2005 (See EFF’s full timeline of events here) News reports in December 2005 first revealed that the National Security Agency (NSA) has been intercepting Americans’ phone calls and Internet communications. Documents Reveal N.S.A. Campaign Against Encryption - Document. How The NSA Pulls Off Man-In-The-Middle Attacks: With Help From The Telcos.
We already covered the latest Guardian report on the NSA and GCHQ's attempts to compromise Tor.
While those have failed to directly break Tor, they were more successful effectively exploiting vulnerabilities in Firefox to target certain Tor users. Boundless Informant: the NSA's secret tool to track global surveillance data. The National Security Agency has developed a powerful tool for recording and analysing where its intelligence comes from, raising questions about its repeated assurances to Congress that it cannot keep track of all the surveillance it performs on American communications.
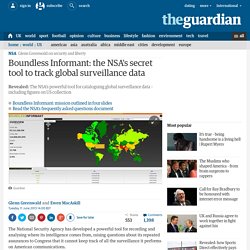
The Guardian has acquired top-secret documents about the NSA datamining tool, called Boundless Informant, that details and even maps by country the voluminous amount of information it collects from computer and telephone networks. The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message. The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013.
Iran was the country where the largest amount of intelligence was gathered, with more than 14bn reports in that period, followed by 13.5bn from Pakistan. 6 Anti-NSA Technological innovations that May Just Change the World. People used to assume that the United States government was held in check by the constitution, which prohibits unreasonable searches and seizures and which demands due process in criminal investigations, but such illusions have evaporated in recent years.

It turns out that the NSA considers itself above the law in every respect and feels entitled to spy on anyone anywhere in the world without warrants, and without any real oversight. Understandably these revelations shocked the average citizen who had been conditioned to take the government's word at face value, and the backlash has been considerable. The recent "Today We Fight Back" campaign to protest the NSA's surveillance practices shows that public sentiment is in the right place. Whether these kinds of petitions and protests will have any real impact on how the U.S. government operates is questionable (to say the least), however some very smart people have decided not to wait around and find out.
NSA Glossary. 28 January 2014Last updated at 14:06 ET By Leo Kelion Technology reporter The documents leaked by Edward Snowden have led the White House to call for reforms.
The NSA Is Breaking Most Encryption on the Internet. The new Snowden revelations are explosive. Basically, the NSA is able to decrypt most of the Internet. They're doing it primarily by cheating, not by mathematics. NSA & Big Brothers, suite. Controlling the web (2012) In January 2012, two controversial pieces of legislation were making their way through the US Congress. SOPA, the Stop Online Piracy Act, and PIPA, the Protect Intellectual Property Act, were meant to crack down on the illegal sharing of digital media. The bills were drafted on request of the content industry, Hollywood studios and major record labels. The online community rose up against the US government to speak out against SOPA, and the anti-online piracy bill was effectively killed off after the largest online protest in US history.
But it was only one win in a long battle between US authorities and online users over internet regulation. SOPA and PIPA were just the latest in a long line of anti-piracy legislation US politicians have passed since the 1990s. The US government says it must be able to fight against piracy and cyber attacks. Sympa de mettre un visage sur une voix. La NSA espionnait aussi les Nations unies. Les géants du Web minimisent leur implication dans le scandale de la NSA. Facebook, Microsoft, Yahoo ! Et Google ont publié lundi le nombre de demandes de renseignements sur des utilisateurs qu’ils ont reçues dans le cadre du programme Prism au cours des six premiers mois de 2013. La NSA peut obtenir toute information qu’elle recherche sur un internaute. La question est de savoir si Facebook, Google, Microsoft et Yahoo facilitent cet espionnage. Les grandes entreprises du Web ont révélé lundi, dans un rapport, le nombre de requêtes judiciaires qu’elles ont reçues secrètement de la part de la NSA, selon Reuters.
Les géants du Web souhaitent minimiser leur rôle dans le scandale de la NSA révélée par Edward Snowden en 2013. Comment la NSA ignore les lois sur la vie privée et édulcore des rapports. Comment la NSA infiltre secrètement les serveurs de Google et Yahoo! Prism : la NSA a dédommagé les géants du Web. Espionnage: Kerry admet que les Etats-Unis sont parfois allés «trop loin» Les Etats-Unis sont parfois allés «trop loin» en matière d'espionnage, a reconnu le secrétaire d'Etat John Kerry, dans ce premier aveu de Washington en pleine polémique avec l'Europe sur la collecte massive de données par l'Agence nationale de sécurité (NSA).
Après dix jours de scandale, de révélations et de démentis entre les Etats-Unis et leurs alliés européens, c'est la première fois qu'un responsable gouvernemental américain admet explicitement des pratiques controversées dans l'interception par la NSA de communications et de données en Europe. «Dans certains cas, je vous le concède, comme l'a fait le président (américain Barack Obama), certaines de ces actions sont allées trop loin et nous allons nous assurer que cela n'arrive plus à l'avenir», a déclaré John Kerry lors d'une conférence à Londres à laquelle il participait depuis Washington jeudi soir par liaison vidéo. Obama résolu à clarifier la situation Une polémique internationale Avec AFP. How Nsa Uses Radio Frequencies. La NSA espionne aussi les ordinateurs non-connectés à internet.
Why Care About the N.S.A.? - Video. NSA: the story of the summer. The NSA's Secret Role in the U.S. Assassination Program. Credit: Kirsty Wigglesworth/Associated Press. The National Security Agency is using complex analysis of electronic surveillance, rather than human intelligence, as the primary method to locate targets for lethal drone strikes – an unreliable tactic that results in the deaths of innocent or unidentified people.
According to a former drone operator for the military’s Joint Special Operations Command (JSOC) who also worked with the NSA, the agency often identifies targets based on controversial metadata analysis and cell-phone tracking technologies. Rather than confirming a target’s identity with operatives or informants on the ground, the CIA or the U.S. military then orders a strike based on the activity and location of the mobile phone a person is believed to be using. His account is bolstered by top-secret NSA documents previously provided by whistleblower Edward Snowden. It is also supported by a former drone sensor operator with the U.S. “They might have been terrorists,” he says. #PRISM #Snowden #Lustre : ceci n’est pas un sabre-laser.
Les révélations d’Edward Snowden doivent amener une réflexion d’ensemble sur le monde interconnecté et hypertechnologique dans lequel nous sommes entrés. Opt out of PRISM, the NSA's global data surveillance program - PRISM BREAK. Prism ? Une surprise ? Pas vraiment non … NSA Prism program taps in to user data of Apple, Google and others. The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian.
The NSA access is part of a previously undisclosed program called Prism, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says. The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation – classified as top secret with no distribution to foreign allies – which was apparently used to train intelligence operatives on the capabilities of the program. The document claims "collection directly from the servers" of major US service providers. Although the presentation claims the program is run with the assistance of the companies, all those who responded to a Guardian request for comment on Thursday denied knowledge of any such program.
An Apple spokesman said it had "never heard" of Prism. NSA slides explain the PRISM data-collection program. NSA seeks to build quantum computer that could crack most types of encryption. [Read an annotated description of the Penetrating Hard Targets project] The development of a quantum computer has long been a goal of many in the scientific community, with revolutionary implications for fields such as medicine as well as for the NSA’s code-breaking mission.
With such technology, all current forms of public key encryption would be broken, including those used on many secure Web sites as well as the type used to protect state secrets. Newly Leaked NSA Slides On PRISM Add To Confusion, Rather Than Clear It Up. NSA paid millions to cover Prism compliance costs for tech companies. Why the NSA Surveillance Program Isn't Like "The Wire" David Simon, creator of The Wire, got a lot of attention over the weekend for his defense of the NSA program that collects records of every phone call made in the United States. It's really nothing new, he says: Allow for a comparable example, dating to the early 1980s in a place called Baltimore, Maryland. There, city detectives once began to suspect that major traffickers were using a combination of public pay phones and digital pagers to communicate their business.
And they took their suspicions to a judge and obtained court orders — not to monitor any particular suspect, but to instead cull the dialed numbers from the thousands and thousands of calls made to and from certain city pay phones. Catalog Reveals NSA Has Back Doors for Numerous Devices. NSA surveillance: anger mounts in Congress at 'spying on Americans' Anger was mounting in Congress on Tuesday night as politicians, briefed for the first time after revelations about the government's surveillance dragnet, vowed to rein in a system that one said amounted to "spying on Americans". New NSA leaks show how US is bugging its European allies.
FLYING PIG: The NSA Is Running Man In The Middle Attacks Imitating Google's Servers. Glyn mentioned this in his post yesterday about the NSA leaks showing direct economic espionage, but with so many other important points in that story, it got a little buried. The NSA's next move: silencing university professors? ‘NSA-Proof’ Email Service ‘ProtonMail’ by Harvard and MIT Students becomes massive success. NSA's 'TURBINE' Cookies used by NSA to spy.
How the NSA Plans to Infect 'Millions' of Computers with Malware. The NSA Is Breaking Most Encryption on the Internet. The ultimate goal of the NSA is total population control. NSA shares raw intelligence with Israel. NSA & Israel Developed STUXNET Together.
U.S. gives big, secret push to Internet surveillance. A Guardian guide to metadata. US surveillance guidelines not updated for 30 years, privacy board finds. Smartphone location, what the Government could do... The state should be exposing the cyber-snoops, not joining them. The US government has betrayed the internet. We need to take it back. Comment se rendre invisible du réseau PRISM?