

How blockchain will revolutionise far more than money. The impact of record-keeping on the course of history cannot be overstated. For example, the act of preserving Judaism and Christianity in written form enabled both to outlive the plethora of other contemporary religions, which were preserved only orally. William the Conqueror’s Domesday Book, compiled in 1086, was still being used to settle land disputes as late as the 1960s. Today there is a new system of digital record-keeping. Its impact could be equally large.
Mobile security. Psiphon.ca · delivering the net. Opt out of PRISM, the NSA’s global data surveillance program - PRISM BREAK. EXCLUSIVE: Owner of Snowden’s Email Service on Why He Closed Lavabit Rather Than Comply With Gov’t. This is a rush transcript.

Copy may not be in its final form. AARON MATÉ: We turn now to the news an encrypted email service believed to have been used by National Security Agency leaker Edward Snowden has abruptly shut down. The move came amidst a legal fight that appeared to involve U.S. government attempts to win access to customer information. 2 E-Mail Services Close and Destroy Data Rather Than Reveal Files. An image of Silent Circle’s Web page, ending its e-mail.
A spokesman said the company’s customers included heads of state, members of royalty and government agencies. The company will continue its encrypted phone and text messaging service. The shutdown of two small e-mail providers on Thursday illustrates why it is so hard for Internet companies to challenge secret government surveillance: to protect their customers’ data from federal authorities, the two companies essentially committed suicide. Lavabit, a Texas-based service that was reportedly used by Edward J. Snowden, the leaker who had worked as a National Security Agency contractor, announced the suspension of its service Thursday afternoon. ProtonMail - Secure Email, Made Simple. How to remain secure against NSA surveillance.
Now that we have enough details about how the NSA eavesdrops on the internet, including today's disclosures of the NSA's deliberate weakening of cryptographic systems, we can finally start to figure out how to protect ourselves.
For the past two weeks, I have been working with the Guardian on NSA stories, and have read hundreds of top-secret NSA documents provided by whistleblower Edward Snowden. I wasn't part of today's story – it was in process well before I showed up – but everything I read confirms what the Guardian is reporting. At this point, I feel I can provide some advice for keeping secure against such an adversary. The primary way the NSA eavesdrops on internet communications is in the network. That's where their capabilities best scale. Leveraging its secret agreements with telecommunications companies – all the US and UK ones, and many other "partners" around the world – the NSA gets access to the communications trunks that move internet traffic.
Revealed: 'Collect It All' NSA Targets Those Seeking Web Privacy. (Image: via Boing Boing)Internet users who use online privacy tools or read certain websites may themselves become targets of NSA surveillance, according to a new investigation by public broadcasting outlets in Germany published on Thursday.

Detekt tool aims to tell activists if their PCs are being spied on. A coalition of human rights groups has released a tool called Detekt, for finding known spyware packages.
It doesn’t promise a 100 percent hit rate, but it’s supposed to help journalists and activists see if their Windows PCs have been infected with the likes of FinFisher, which has been used everywhere from the U.K. and U.S. to Germany, India and Bahrain. The groups include Amnesty International, the Electronic Frontier Foundation (EFF), Privacy International and Germany’s Digitale Gesellschaft. Detekt was developed by security researcher Claudio Guarnieri, who noted that it is not yet supported on the 64-bit version of Windows 8.1. “Governments are increasingly using dangerous and sophisticated technology that allows them to read activists and journalists’ private emails and remotely turn on their computer’s camera or microphone to secretly record their activities,” Amnesty head of military, security and police Marek Marczynski said in a statement.
The Best Browser Extensions that Protect Your Privacy. How it works? Do Not Track Plus. Do-Not-Track Movement Is Drawing Advertisers’ Fire. Do Not Track mechanisms are features on browsers — like Mozilla’s Firefox — that give consumers the option of sending out digital signals asking companies to stop collecting information about their online activities for purposes of targeted advertising.

Google tracks you. We don't. An illustrated guide. DuckDuckGo. A Browser To Keep The NSA From Snooping On You. Concern over personal privacy in the era of NSA spying revelations has reached something of a Code Orange.
Out in the Open: Inside the Operating System Edward Snowden Used to Evade the NSA. Photo: Josh Valcarcel/WIRED When NSA whistle-blower Edward Snowden first emailed Glenn Greenwald, he insisted on using email encryption software called PGP for all communications.

But this month, we learned that Snowden used another technology to keep his communications out of the NSA’s prying eyes. Anonymity Online. Tor traffic disguised as Skype video calls to fool repressive governments. Computer scientists have released a tool that disguises communications sent through the Tor anonymity service as Skype video calls, a cloak that's intended to prevent repressive governments from blocking the anonymous traffic.
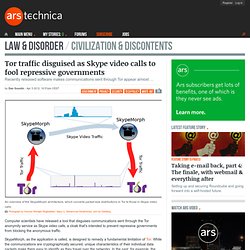
SkypeMorph, as the application is called, is designed to remedy a fundamental limitation of Tor: While the communications are cryptographically secured, unique characteristics of their individual data packets make them easy to identify as they travel over the networks. In the past, for example, the cryptographic key exchange was different in Tor transactions and the certificates used were typically valid for only a matter of hours, compared with as long as a year or two for certificates used by most Web servers. These fingerprints made it possible for government censors in Iran, China, and elsewhere to block data traveling over Tor while leaving the rest of the country's communications intact.
A censorship arms race. FreedomBox Foundation. Presentation of the FreedomBox from James Vasile. PirateBox Takes File-Sharing Off The Radar and Offline, For Next To Nothing. ‘Tribler’ software makes Internet piracy impossible to stop. By Stephen C.
WebsterWednesday, February 8, 2012 11:38 EDT Internet piracy has been a hot topic in recent weeks, but it’s about to heat up even more. With lawmakers all over the world struggling to agree upon copyright regimes that would disconnect people from the Internet, shut down websites simply for linking to infringing content and cut off whole advertising networks that support pirate domains, one might think the world was on the verge of plugging up the copied media loophole for good. But then, one would be wrong. A piece of software getting a fresh look this week seems to have the answer that media pirates are looking for: invincibility, with zero liability for website operators. Protects Your Privacy!
The only search engine that does not record your IP address. Every time you use a regular search engine, your search data is recorded. Major search engines capture your IP address and use tracking cookies to make a record of your search terms, the time of your visit, and the links you choose - then they store that information in a giant database. Home. Distributed wifi occupation. Silent Circle's latest app democratizes encryption. Governments won't be happy. Courtesy of Silent Circle For the past few months, some of the world’s leading cryptographers have been keeping a closely guarded secret about a pioneering new invention. Today, they’ve decided it’s time to tell all. Ryan Gallagher is a journalist who reports on surveillance, security, and civil liberties. Follow Back in October, the startup tech firm Silent Circle ruffled governments’ feathers with a “surveillance-proof” smartphone app to allow people to make secure phone calls and send texts easily.
This Cute Chat Site Could Save Your Life and Help Overthrow Your Government. Nadim Kobeissi, creator of Cryptocat, spoke in mid-July at the HOPE conference, held at New York’s Hotel Pennsylvania every two years. Hide Secret Messages in Facebook Photos With This Chrome Extension. It's no secret that Facebook isn't the best place for keeping secrets. Owen Campbell-Moore, a computer science student at Oxford University, designed a method to encrypt secret messages inside photos on the social networking site. Heml.is - The Beautiful & Secure Messenger. Jitsi (SIP Communicator) In Antipiracy Debate, Media Worlds (and Generations) Clash. Internet Pirates Will Always Win.
Hit one, countless others appear. Quickly. SOPA Boycotts and the False Ideals of the Web. Google’s Spymasters Are Now Worried About Your Secrets. A recent article in The Wall Street Journal by Google Executive Chairman Eric Schmidt, “The Dark Side of the Digital Revolution,” makes for very scary reading. Why Nico Sell, CEO of Wickr, Demands Privacy and Resists Social-Media Business.
In Cryptography, Advances in Program Obfuscation. Doxxing defense: Remove your personal info from data brokers.