

Docs · master · matrix-org / Olm · GitLab. Introduction of the privacy centric matrix bot. — one. January 8, 2021 Parses the whole post / article (text), acting as a proxy, providing a preview (some posts might not load because bot handles all the requests over Tor).

Converts YouTube, Reddit, Twitter, Instagram links to respective privacy focused front-ends. Converts (several) clearnet site links to respective onion links (includes news media / publication / online services sites). The bot will place custom m.reaction (DM preview / DM alternative) on link containing message which will trigger (if clicked) the bot to send converted alternative links and requested articles (will include media elements soon) in a separate room. Commento: Home. ChatonsOrg : "@ademalsasa @praveen…" Berty/berty: Berty is a secure peer-to-peer messaging app that works with or without internet access, cellular data or trust in the network. Jitsi Meet. Remote Communication - LibrePlanet. This list is work in progress.
We have not audited the software listed on this page for security or privacy concerns beyond what developers of the software, and potentially other sites tell us about it. We have done some initial research into software licenses. Entries with Free Software Directory links have been thoroughly reviewed from a licensing perspective. This page is a shared resource, and we encourage others to add to it, so some of the entries here may be added by members of the community. We check this resource periodically, and know that others check it too, but it's a wiki, so errors may be added before they're fixed. As more people are going remote, there is an outbreak of proprietary software happening around the Internet.
Keybase. MotionBox Video Browser. I created a reddit-like site that bridges I2P, Tor and Yggdrasil to allow users to interact with one another without leaving their network of choice. (Also available on the clearnet) : i2p. I hope that it's okay that I post this here.
So, I wanted a reddit-like site that was: Lightweight / fastPrivacy focusedNot heavy on censorshipAnd integrated with "alternative internets" (Tor, I2P, Yggdrasil for now) This website is accessible as a service on each of the individual large anonymity networks allowing users of those networks to not leave their network of choice. Whereas normally, members on a Tor Onion Service web forum would only be able to communicate with other members using that same Tor Onion Service, on here, they can interact with members using the website via the I2P eepsite service, or the regular internet, even. The New Oil. You’re probably already aware that cell phones don’t communicate directly with other cell phones, they communicate with cell towers who make a mesh network with other cell towers to bounce your call, text, or other data from tower to tower until it reaches its destination.
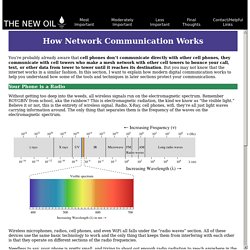
But you may not know that the internet works in a similar fashion. In this section, I want to explain how modern digital communication works to help you understand how some of the tools and techniques in later sections protect your communications. Your Phone is a Radio Without getting too deep into the weeds, all wireless signals run on the electromagnetic spectrum. Remember ROYGBIV from school, aka the rainbow? Wireless microphones, radios, cell phones, and even WiFi all falls under the “radio waves” section. The Internet Works the Same Way. The Hitchhiker’s Guide to Online Anonymity. Version 0.1.1 (draft), December 2020 (work in progress, some parts are incomplete) by AnonymousPlanet This guide is open-source, licensed under Creative Commons Attribution 4.0 International (cc-by-4.0).
Feel free to submit issues/recommendations/ideas using Github Issues at: PDF version of this guide at: Send Messages, Not Metadata. Spantaleev/matrix-docker-ansible-deploy: Matrix (An open network for secure, decentralized communication) server setup using Ansible and Docker. Installing the new Dendrite Matrix Homeserver on Debian Buster. This post contains my personal notes on how to set up Dendrite, Matrix.org’s second-generation homeserver written in Go.
These notes are not yet complete, but do contain the basics to get things going. Please note that Dendrite is in early beta and not yet recommended for use in production environments. For more information, refer to the README.md on Github and this blogpost on Matrix.org. GPG Quick Start. SimonBrazell/privacy-redirect: A simple web extension that redirects Twitter, YouTube, Instagram & Google Maps requests to privacy friendly alternatives. #23 - Échanger des secrets entre serveurs (peering) - infra - tildegit.
Piloting SecureDrop Workstation for Qubes OS - SecureDrop. In March, Freedom of the Press Foundation will begin to pilot SecureDrop Workstation for Qubes OS with select news organizations.
The goal of the project is to make the SecureDrop experience more intuitive, and to decrease the time-on-task for journalists, without compromising security. With SecureDrop Workstation, journalists can use a single integrated computer to review messages and documents submitted by sources via SecureDrop, and to reply to them. We’re deeply grateful to Freedom of the Press Foundation’s friends and supporters for making this project possible, including the Mozilla Open Source Support Awards and our individual donors. WireGuard: fast, modern, secure VPN tunnel. Trailofbits/algo: Set up a personal VPN in the cloud. Terms of Service; Didn't Read. NixNet. Standing on Our Own Two Feet. Uncensored Internet access for Windows and Mobile. From Kushal's mind. DriveDroid. Notifications for image hosting.
Setup guide for first time use and device compatibility testing. Blacklist/whitelist in setup guide that checks whether device is found to be compatible or not. Ability to choose different USB systems for better device compatibility. Automatic USB mode switching upon hosting images. Nicer host dialog with descriptions for each button and a help button. Manually changing USB mode and persistent USB mode individually (was always combined in 0.7.7). Ability to turn off automatic USB mode switching for people who want to switch manually. Liberated Computers – (from Mostly Harmless) Friendica – A Decentralized Social Network. Friendica/friendica: Friendica Communications Platform. De-google-ify Internet.
- Change the worldone byte at a time. How I do my Computing. My computer I use a Thinkpad T400s computer, which has a free initialization program (libreboot) and a free operating system (Trisquel GNU/Linux).

It was not sold that way by Lenovo, however; small businesses buy them used, recondition them, and install the free software. This is one of the computers endorsed by the FSF. Before using such Thinkpads, I used the Lemote Yeeloong for several years. Owncast. Antitree/private-tor-network: Run an isolated instance of a tor network in Docker containers. Steganography at DuckDuckGo. Live: trustable live streaming for all. Live streaming simplified Hechno Live is a Web-based live streaming service that works on any device with a modern Web browser installed on it.
You can livecast your screen, webcam, mic and system audio without installing any additional plugins or apps, thanks to the latest Web standards. The actual use of Hechno Live is up to you. Learn Learnin' Crabgrass Dev Network - networks - Crabgrass. October 2014 to March 2015 – Finalizing Core Rework¶ Matomo Analytics - The Google Analytics alternative that protects your data. State-of-the-art crypto goes post-quantum. Secrecy is one of the most important functions of computer science. Should electronic secrecy suddenly collapse into total transparency, we could not engage in electronic commerce, we would be unable to communicate privately, our past communications would be globally visible, and we would be critically impacted in myriad ways that would fundamentally change our ability to work and live.
Consider the time we spend every day maintaining our secrecy with passwords, lock patterns, wireless fobs, and biometrics that restrict access to protect us and the ramifications of their failure. Public-key cryptosystems form a critical aspect of our secrecy. The ability to establish private communications over a public medium is exercised billions of times per day. LineageOS 17.1 ROM for Samsung Galaxy M30s Android 10 Q. The Case for Pseudonymity. Abstract Pseudo-anonymity enables an open society. Privacy is a basic human right and a requirement for true self-expression, free flow of information, and autonomy.
Total anonymity is not always a realistic goal for a functioning society as proof of ownership and right to access requires some proof of identity and or reputation. Opt out of global data surveillance programs like PRISM, XKeyscore, and Tempora - PRISM Break.