Zoom
Trash

Remmina. Sandboxing. Xserver stuff. Containers (linux) Jack. Ftp (to sort) To sort. Mknod. Web based IDEs. Woof-next petget sync. ISO linux. Glibc. Library managment (to sort) Ddog. Anbox (Android) Samba. Python. Mirroing Android Screen. Doing Stuff withotu SystemD. Raspup. Pastebin. Fake-SystemD.
Docker. Socat. Fix Windows. Learn Guitar. Puppylinux (New Forum) Slavoj Žižek. Economics (to sort) Tex. Coding A Meme App In React. Orlando Sentinel. If We All Get COVID Anyway, Should We Just Get It Over With? Face Masks May Be The Key Determinant Of The Covid-19 Curve, Study Suggests. As states reopen amid the ongoing Covid-19 pandemic, many are documenting still-rising levels of new cases.
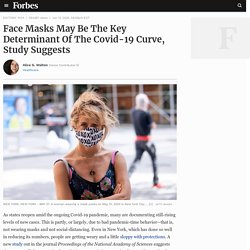
This is partly, or largely, due to bad pandemic-time behavior—that is, not wearing masks and not social-distancing. Even in New York, which has done so well in reducing its numbers, people are getting weary and a little sloppy with protections. A new study out in the journal Proceedings of the National Academy of Sciences suggests that among all the strategies for reducing transmission, wearing face masks may be the central variable that determines the spread of the virus.
“Our analysis reveals that the difference with and without mandated face covering represents the determinant in shaping the trends of the pandemic,” the team, from Texas A&M University, the University of Texas at Austin, California Institute of Technology, and the University of California San Diego, write in their new paper. Coronavirus long-term effects: Some Covid-19 survivors face lung scarring, heart damage, and anxiety.
At first, Lauren Nichols tried to explain away her symptoms.

In early March, the healthy 32-year-old felt an intense burning sensation, like acid reflux, when she breathed. Embarrassed, she didn’t initially seek medical care. Coronavirus: Dexamethasone proves first life-saving drug. Image copyright Getty Images A cheap and widely available drug can help save the lives of patients seriously ill with coronavirus.

The low-dose steroid treatment dexamethasone is a major breakthrough in the fight against the deadly virus, UK experts say. The drug is part of the world's biggest trial testing existing treatments to see if they also work for coronavirus. It cut the risk of death by a third for patients on ventilators. Neoliberal Capitalism Depends on White Supremacy. Billionaires like Mark Zuckerberg, Jeff Bezos, and Jamie Dimon may personally associate with individual African Americans, Latinos and other minorities.
They might even employ them. They might even attend dinner parties with them, and, one-on-one, display few outward manifestations of overt racism. But make no mistake about it: Their vast fortunes and the economic and political power they wield are based on the active and passive promotion of racism and white supremacy. As economist Paul Krugman writes in The New York Times, A Portal Special Presentation- Geometric Unity: A First Look.
Texlive. Tek. Medical Researchers. Billionaire Elon Musk: How I Became The Real 'Iron Man' Code Conference 2016. “Bias Expert” Unwittingly Reveals Own Bias Towards Republicans. Suicide data. Planet of the Humans. Joe Rogan Experience #1470 - Elon Musk. Our Revolution Failed to Live Up to Its Potential. But the Bernie Movement Needs a Mass Organization Now. Despite our best hopes and struggle, Bernie Sanders’s presidential campaign once again ended in second place.
But while we came up short, it’s more than clear now that 2016 wasn’t a fluke — we do indeed have a mass constituency. And those Bernie supporters deserve a vehicle to advance their political project in the years to come — that means a formal organization capable of representing and galvanizing a mass movement. What form that organization should take, however, is up for debate. // ACEP-AAEM Joint Statement on Physician Misinformation.
Joint Statement issued on April 27, 2020: The American College of Emergency Physicians (ACEP) and the American Academy of Emergency Medicine (AAEM) jointly and emphatically condemn the recent opinions released by Dr.
Daniel Erickson and Dr. 2005-2016Joe Rogan From Bush To Donald Trump US Election. Take Back MIT (Eric Weinstein) Bernie Sanders goes out with a whimper - An obituary on an aborted 'revolution' (Part 1) SSL Certificates HOWTO. A Conversation with Ed Steinfeld and Mark Blyth. Puppy Linux Discussion Forum. Glenn Greenwald announces show ft Kyle Kulinski, how to balance authoritarian instinct in crisis. Precise-light - 17March2019 - for older hardware. Thankyou, I'm glad it's working for you.
I was surprised that you were able to get such new certificates to work I'm not sure, whether firefox-16 can use this version of glibc or not. I created an adrv yesterday, by using my remaster sandbox script. Bill Gates: "This is the nightmare scenario"
Coronavirus in China. NicOS-Utility-Suite. Awesome cli Apps. Firefox & certs. YouTube. Woof-CE/verifypkg.sh at testing · puppylinux-woof-CE/woof-CE. Woof-CE/pkg_chooser.sh at testing · puppylinux-woof-CE/woof-CE. Woof-CE/downloadpkgs.sh at testing · puppylinux-woof-CE/woof-CE. Woof-CE/verifypkg.sh at testing · puppylinux-woof-CE/woof-CE. Woof-CE/installpreview.sh at testing · puppylinux-woof-CE/woof-CE. Git tips. Pkgs_to_install - ppm - puppylinux. Intercepted Special: Nina Turner and Briahna Joy Gray on Attacks Against Bernie Sanders. As the presidential campaign of Sen.
Bernie Sanders gains momentum, the attacks against him are intensifying. The billionaire former mayor of New York City, Michael Bloomberg, has announced that he is going to unleash a spate of attack ads against Sanders, while Pete Buttigieg and Joe Biden are harping about comments Sanders made on “60 Minutes” in the 1980s, where he praised Cuba’s literacy efforts. Ron Paul: I Feel a Kinship With Bernie Sanders. EasyPup version 2.2.11, released February 22, 2020. G'day BK, Posting from Easy227 via OperaPortable.
HP smallform desktop, vintage mid 2000's. FiloSottile/age: A simple, modern and secure encryption tool with small explicit keys, no config options, and UNIX-style composability. Mike Bloomberg Ran Stasi-Style Police and Surveillance Operations Against Muslim Americans. As Mayor of New York, Mike Bloomberg ran a sweeping surveillance operation against Muslim Americans.
This week on Intercepted: As Bloomberg nears a half a billion dollars in paid ads for his presidential campaign, he is intensifying his attacks on Bernie Sanders. Meanwhile, the red-baiting smears against Sanders are resurfacing as he surges in national polls. NYU Professor Nikhil Pal Singh, author of “Race and America’s Long War,” dissects the record of Bloomberg, what his candidacy says about the state of electoral politics in the U.S. and discusses Bloomberg’s “racial terror” tactics in New York. Hacking is not a hobby but a way of life. VIPKID base pay and incentives: How much do teachers earn per hour? VIPKID pays pretty well for an at-home teaching job, with the VIPKID pay averaging about $20 USD per hour taught. Your pay does depend on how many bookings you get, as parents decide whether to book with you or not. You also need to pay your own taxes in the US or Canada.
VIPKID hours - What time of day can you teach for VIPKID? VIPKid teachers based in North America usually work in the early morning and on weekend evenings. These hours are peak times in China. Teachers create their own schedule by opening slots which students can book. Each class lasts 25-28 minutes and teachers are paid for 30 minutes. You can open as many or as few slots as you want and take a vacation when you want. Tyler Cowen on "The Portal", Ep. #016 (w/ Eric Weinstein) - The Revolution Will Not Be Marginalized.
The idea that the internet is the establishment and the council on foreign relations are the outsiders is a way of obscuring where power lies. Sure the internet is influential but let's not pretend that the council on foreign relations has now power over the internet. For instance I'm sure that the counsel on foreign relations is quite influential in the blue checkmark twitterverse! – s243a
Trying to blame the deviation between the median wage and the the GDP in the 1970s on lost productivity due to feminization is a very sloppy slight of hand. I get it it that the IDW audience likes this kind of thing but the GDP (per person per hour worked) measures productivity rather than the median wage. The deviation between the median wage and GDP has nothing to do with a loss of productivity! This slight of hand works by telling the audience something that they believe so that they will nod along while overlooking the blatant error in logic. It also provides a scapegoat to explain away growing inequality. – s243a
The whole idea that if real inflation is mismeasured then one should be able to make some trade on it shows both a blind faith in the markets and also makes it blatantly clear who *Institutional* economics is for. The idea of utility and preferences also obscures that for the people at the bottom utility is a measure of their basic needs whereas for people at the top it is more a matter of taste. People at the bottom use their income for the basic necessities of living and such necessaries (e.g. housing) aren't available as an "Online-Good". The real rate of inflation for people at the bottom will depend heavily on their needs whereas the real rate of inflation for the people at the top will be based on their tastes. There is not one rate of inflation for all people and aggregate inflation values are averaged over dollars spent rather than on a per person basis. Since wealthy people have more money these tradable aggregates won't reflect the rates of inflation scene by the people at the bottom. – s243a
I'm watching Ep. #016 of Eric Weinsteins Portal. What is interesting is Eric is the token leftest of the IDW. It was perhaps Michael Brooks that compared Erik's show to Dave Rubin's. Unlike Rubin Erik is smart enough to push back but he only does so enough to set his guests up for their points...at least that is what I observe in this episode. Rubin seems to be focused on culture issues whereas Eric seems to be more focused on intellectual issues. However, both of these topics are pillars of an ideology which justifies the status quo. – s243a
How to Redirect Links on Android to Open in the App You Really Wanted. One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always. " If you choose "Just Once," you'll continue to be prompted to select an app every time you tap one of these types of links, which gets annoying fast.
Ssl stuff. Ppa in precise light.