

Introduction to Networking. How Promoting an Online Business Works" How-to stop getting tracked in your Browser. Use Ubuntu Live CD to Backup Files from Your Dead Windows Computer. If you’ve ever asked for help with your Windows computer that won’t boot anymore, you’ve probably been told to “Backup all your data and then reinstall”… but if you can’t boot, how can you get to your data?
That’s the question we’ll be answering today. One of the easiest methods to access your data is to simply boot off an Ubuntu Live CD… and it’s completely free (except for the cost of a blank cd). Burn an Ubuntu Live CD If you have another computer, you can download and burn the Ubuntu Live CD using a very simple application called ImgBurn.
Otherwise, you can bug one of your friends to help you burn a copy. Just open up ImgBurn, and click the icon to “Write image file to disc” Then click on the icon next to “Source”, pick the downloaded ISO file, stick a recordable CD into the drive, and click burn. EPIC Online Guide to Practical Privacy Tools. PET - CyberWiki. Thanks for visiting the CIS PET wiki.
This is meant to be a list of free technologies aimed at empowering Internet users to gain better control over their data. It's very simple to add an entry---just click the "edit" tab, copy and paste the previous entry, and substitute the name, description, and address. Abine - A Firefox / Internet Explorer plugin that blocks third party advertising networks, manages HTTP, DOM, and Flash cookies, and securely manages site logins.
Currently in private beta, but invites aren't hard to get. Abine Privacy SuiteAd Blockers for Browsers - Firefox: Adblock Plus Chrome: AdBlock Safari: AdBlock Anon email services - Send anonymous email awxcnx.de Email drop drop.ioAnonymouse - A Web search portal hosted on an island off the coast of Somalia. How to Surf the Web Anonymously& The Internet has a way of lulling you into a false sense of anonymity.
After all, how can anyone know your true identity in a virtual world? The truth is that simply by connecting to the Internet, you share information about your computer, your geographical location and even about the Web sites you visit. The goal of anonymous Web surfing is to circumvent the technologies that track your online activity and may potentially expose your personal information to others. Password Chart. Aerogel: See-Through, Strong as Steel & Ligher than Air. Despite its incredibly low density, aerogel is one of the most powerful materials on the planet.
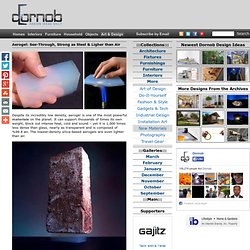
It can support thousands of times its own weight, block out intense heat, cold and sound – yet it is 1,000 times less dense than glass, nearly as transparent and is composed of %99.8 air. Guide To (Mostly) Harmless Hacking. How to Hack a Vending Machine. Hack Website using Dot Net Nuke. Watch the World Get Attacked By Cyber Criminals in Real Time. HakShop — USB Rubber Ducky. Since 2010 the USB Rubber Ducky has been a favorite amongst hackers, penetration testers and IT professionals.
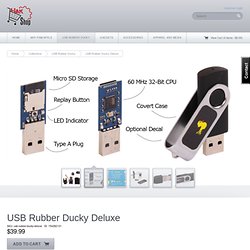
With origins as a humble IT automation proof-of-concept using an embedded dev-board, it has grown into a full fledged commercial Keystroke Injection Attack Platform. The USB Rubber Ducky captured the imagination of hackers with its simple scripting language, formidable hardware, and covert design. Quack like a Keyboard! Nearly every computer including desktops, laptops, tablets and smartphones take input from Humans via Keyboards. It's why there's a specification with the ubiquitous USB standard known as HID - or Human Interface Device. By taking advantage of this inherent trust with scripted keystrokes at speeds beyond 1000 words per minute traditional countermeasures can be bypassed by this tireless trooper - the USB Rubber Ducky. Ducky Script. The USB Rubber Ducky's scripting language is focused on ease-of use. Unmatched Performance, Simplicity and Value.
Cross Platform. Google Hacking Database, GHDB, Google Dorks. Hacking wireless networks with Man in the Middle attacks. - StumbleUpon. Google Chrome: Coffee. Cloud Evolution: From Internal Efficiencies to Better Customer Experiences. It's been fascinating to observe the evolution of cloud computing.
Although I've only been focused on it for about three years, in those three years I've seen drastic changes in the way cloud is perceived -- and employed. Already we've moved from more narrow, opportunistic usages to broad platform-level thinking that benefits companies seeking to innovate their business models. In some cases it's entire industries that are impacted. In fact, a recent IBM study of business and IT leaders found that the number of organizations which will be using cloud for business model innovation will double within the next three years. In addition, even though cloud is often perceived as being an IT concern, respondents perceive cloud's value in its ability to help them with business capabilities such as increased collaboration (62%), new delivery channels/markets (56%), new/enhanced revenue streams (54%), competitive differentiation through specialization (51%), and so on.
Ralph Langner: Cracking Stuxnet, a 21st-century cyber weapon. Top 10 Ways to Turn Your Retired Gadgetry into the Technology of the Future.