

Firewall vendors revisit core technologies to win market. Firewalls should still be an integral part of any enterprise's cyber security strategy, and vendors of the hardware variety are redoubling their R&D to win more market share.

Firewall hardware is now evolving in line with two trends: one towards greater distribution of security across the enterprise with incorporation of intrusion protection, and the other tied to the growth of server virtualisation. This is blurring the traditional line between firewall hardware and software; and yet at the same time preserving some distinct niches for each. Firewalls are the network security systems that control incoming and outgoing data traffic by analysing the packets and determining whether they should be let 'through' or blocked, based on rules set by IT security policies, for instance. The growing sophistication of its functions, whether in hardware or software, also means that the firewall itself is overlapping more with intrusion detection systems (IDS) and even higher level attack analysis. Quantum cryptography: using photons to create secure keys.
It is essential that cryptography remains well ahead of the hackers, and that's precisely the motivation for a project that uses the quantum mechanical properties of photons to create tamper-proof keys.

The future for the protection of sensitive data could be bright. Researchers have uncovered evidence that the quantum mechanical properties of photons (light particles) may be used to generate tamper-proof keys, and this represents a big leap forward in the fight against computer hackers and other cyber-security threats. Four and a half years ago, the EU-funded Secure Communication based on Quantum Cryptography (SECOQC) consortium successfully demonstrated long-distance, practical quantum-key distribution (QKD) in a fibre-optic network around the Austrian capital Vienna. Battelle says that it is already in talks with organisations interested in using the technology.
One particular concern is diversion of Internet traffic. Privacy amplification QKD has two stages. Trusted nodes QKD in space? Mailvelope. GPGTools - It's worth protecting what you love. Gpg4win - Secure email and file encryption with GnuPG for Windows. Hacking the Internet - bringing down infrastructure. Why should hackers try to disable computers when they might be able to set their sights higher?
Routers can be just as vulnerable as servers, so why not bring down the entire Internet? The US Department for Homeland Security (DHS) was set up in November 2002 with the primary responsibility of protecting the USA and its territories from terrorist attacks, accidents, and natural disasters. However, its remit has slowly spread in recent years to cover the nation's Critical National Infrastructure, which includes the structure of the Internet itself.
VoIP: voicing security concerns. Channelling voice calls over IP networks has brought many advantages to enterprise communications, but it also creates some security risks.

Though Voice over Internet Protocol (VoIP) services are available for both consumer and business markets, it is from the latter that most enthusiasm for it has come; for this reason, it is also where most of VoIP's security issues occur. While the commercial sector has, of course, invested heavily in protecting their data networks from other cyber threats, IP-based voice has been somewhat overlooked. VoIP describes a set of services used to manage the delivery of voice transmissions over a broadband Internet connection instead of using time-division multiplexing (TDM) over a traditional public switched telephone network (PSTN). It works by transmitting analogue voice signals as digitised packets over the Internet allowing it to share the same connections as other digital technologies. Free calls for all? Preparation is key. Online Visual Traceroute. Map Data Map data ©2017 Google, INEGI Map Satellite Visual traceroute may have misplaced routers.
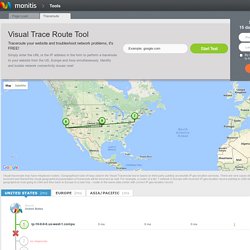
Geographical route of hops used in the Visual Traceroute tool is based on third-party publicly accessible IP geo-location services. Infrastructure cyber attack threat grows. Despite high-profile attacks, there is still a lack of IT security in key public infrastructure.

We ask if it will take a major meltdown to prompt governments to take action. It is almost a year now since the attack on the control system of an Iranian nuclear reactor by the Stuxnet virus. However, despite this ominous development and recent reports that the threat of attacks has increased, a worrying amount of vital public infrastructure is still vulnerable. National Cyber Security Alliance. ID access management's cloud challenge. With users accessing systems from ever more obscure points of entry, how do you keep control of access privileges?
We look at the software that may have the answer. The problem of offsetting data security against accessibility has proved a ubiquitous problem of the last decade. As the range of software that users have to work with has broadened and security's remit has become enlarged, IT administrators have struggled to keep control of system and application access without complicating the login process. Identity access management (IAM) software has emerged as an important tool for administrators trying to regain control. Research firm Gartner has estimated that companies are spending roughly 8 per cent of their data security budget on IAM tools. Introduction to Cyber Security: More free resources from The Open University. Copyrighted image Copyright: © Oksipix 4 | Dreamstime.com 5 - Cyber Security Photo About the course Do you want to better understand online security and protect your digital life, whether at home or work?
Perhaps you would like to be able to recognise the threats that could harm you online and the steps you can take to reduce the chances that they will happen to you? We've collated a range of free content for you to take your learning further with more in-depth free courses and features on this fascinating subject. Google 2-Step Verification. Security Notice. Update: July 10, 2015 @ 8:00 PM EST Thank you for taking the time to read our posts and follow our recommended actions after the recent events.
Behind-the-scenes, our response has been ongoing. As we mentioned before, we’ve engaged security experts and firms to help us, and we’re working with the authorities to take the appropriate actions. These events have put our systems to the test, and we’re more secure as a result. Password Safe. 1Password. Password Manager, Auto Form Filler, Random Password Generator & Secure Digital Wallet App.
Untitled Document. Week 2 Good Password Practices. 2014 Information security breaches survey. Cyber governance health check: 2013. Cyber security - small firms now in the firing line. Small businesses need to upgrade their awareness of - and abilities in - cyber security if they are to avoid becoming the 'soft underbelly' of the UK's fights against hackers and cyber threats.
Media Reports about IT security breaches resulting in data loss and other compromises to corporate data integrity usually only make headline news when big name brands are hit. Resultant concerns about reputational damage have spurred many medium-to-large enterprises (MLEs) into reviewing their cyber-security strategies and redoubling their efforts to ensure that their ICT is properly protected - or at least as protected as possible within the context of their risk assessments and IT budgets. Because of their size a lot of the damage can over time be 'managed'. Disproportionate riches The 'Black Hat' intelligentsia are wise to the fact that start-up SMEs often have data assets of a value disproportionate to their company size on their systems. Introduction to Cyber Security: More free resources from The Open University. Troy Hunt.
Schneier on Security. Latest computer security news, opinion and advice. Krebs on Security. Product Security. Microsoft Internet Safety and Security Center. Naked Security – Computer Security News, Advice and Research. The Hacker News — Cyber Security, Hacking, Technology News. Infosecurity Magazine - Information Security & IT Security News and Resources. IT security resources and information - ComputerWeekly. Threat Level.
Cybersecurity stories. Internet security: Online safety & security news. Information security. Technology. Protect your home or business from cyber crime. Product Security. Security Response Center.