

In Baltimore and Beyond, a Stolen N.S.A. Tool Wreaks Havoc. Hacker Can Monitor Cars And Kill Their Engines After Breaking Into GPS Tracking Apps. A hacker broke into thousands of accounts belonging to users of two GPS tracker apps, giving him the ability to monitor the locations of tens of thousands of vehicles and even turn off the engines for some of them while they were in motion, Motherboard has learned.
The hacker, who goes by the name L&M, told Motherboard he hacked into more than 7,000 iTrack accounts and more than 20,000 ProTrack accounts, two apps that companies use to monitor and manage fleets of vehicles through GPS tracking devices. The hacker was able to track vehicles in a handful of countries around the world, including South Africa, Morocco, India, and the Philippines. On some cars, the software has the capability of remotely turning off the engines of vehicles that are stopped or are traveling 12 miles per hour or slower, according to the manufacturer of certain GPS tracking devices.
At that point, the hacker said he brute-forced “millions of usernames” via the apps’ API. Got a tip? / Triton is the world’s most murderous malware, and it’s spreading. As an experienced cyber first responder, Julian Gutmanis had been called plenty of times before to help companies deal with the fallout from cyberattacks.
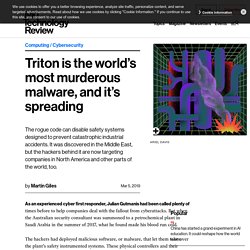
But when the Australian security consultant was summoned to a petrochemical plant in Saudi Arabia in the summer of 2017, what he found made his blood run cold. The hackers had deployed malicious software, or malware, that let them take over the plant’s safety instrumented systems. These physical controllers and their associated software are the last line of defense against life-threatening disasters. They are supposed to kick in if they detect dangerous conditions, returning processes to safe levels or shutting them down altogether by triggering things like shutoff valves and pressure-release mechanisms.
The malware made it possible to take over these systems remotely. Equifax mystery: Where is the data? How Hackers and Scammers Break into iCloud-Locked iPhones. In spring, 2017, a teenager walked up behind a woman leaving the Metro in Northeast Washington DC and put her in a chokehold: "Be quiet," he said.

And "delete your iCloud. " He grabbed her iPhone 6S and ran away. Last month, there were a string of similar muggings in Philadelphia. In each of these muggings, the perpetrator allegedly held the victim up at gunpoint, demanded that they pull out their iPhone, and gave them instructions: Disable “Find My iPhone,” and log out of iCloud. In 2013, Apple introduced a security feature designed to make iPhones less valuable targets to would-be thieves. The iCloud security feature has likely cut down on the number of iPhones that have been stolen, but enterprising criminals have found ways to remove iCloud in order to resell devices.
Making matters more complicated is the fact that not all iCloud-locked phones are stolen devices—some of them are phones that are returned to telecom companies as part of phone upgrade and insurance programs. Many popular iPhone apps secretly record your screen without asking. Many major companies, like Air Canada, Hollister and Expedia, are recording every tap and swipe you make on their iPhone apps.
In most cases you won’t even realize it. How Hackers Bypass Gmail 2FA at Scale. If you’re an at risk user, that extra two-factor security code sent to your phone may not be enough to protect your email account. Hackers can bypass these protections, as we’ve seen with leaked NSA documents on how Russian hackers targeted US voting infrastructure companies. But a new Amnesty International report gives more insight into how some hackers break into Gmail and Yahoo accounts at scale, even those with two-factor authentication (2FA) enabled. How to Delete Online Accounts You No Longer Need. Massive Collection #1 Breach Exposes 773 Million Emails. Hacks to clean and de-clutter your computer (inside and out) Get the Better newsletter.
Jan. 17, 2019, 8:35 PM GMT By Nicole Spector As Marie Kondo fever sweeps the nation, many of us are in an intense tidying up mode. We’re bidding adieu to clothes, books and miscellany that doesn’t “spark joy,” as organizational guru Kondo would say, and embracing a more minimalist mindset that emphasizes gratitude for our belongings and our homes. Want to be a Hacker? Go to Dallas. Set Up Your Financial Accounts Like You're Going to Be Hacked. Account takeover fraud: 7 tips to make you less vulnerable. Editor's note: Naples Daily News columnist and professional organizer Marla Ottenstein has been through a harrowing, expensive and life-changing experience since she was "hacked" last summer.
She's sharing some of her insights and the lessons she's learned. Shame on me, one of the most organized and security-conscious people you’ll ever meet, for logging onto the unsecured Wi-Fi at Miami International Airport last summer. I knew it was the wrong thing to do, but feeling impervious to hackers and somewhat cavalier, I figured: What could happen in 15 minutes. It turns out a lot can happen. The criminals hijacked my email and my mobile accounts and tried (unsuccessfully) to take over my Apple account, and that was just the beginning.
This type of cyber crime goes far beyond identity theft. Account takeover is a very real and very frightening issue and goes far beyond “transactional” theft (i.e., someone gets your credit card number and you have to get a replacement card).