

MAJES
It's-a me, Majes !
SYSADMIN. Chriskiehl/Gooey. Fix atikmpag.sys / atikmdag.sys blue screen errors (BSOD) I use a cheap AMD graphic card from Powercolor.
At times I would run into the atikmpag.sys blue screen error, but you can easily fix it by extracting the atikmdad.sys from the original drivers Expand.exe (File Expansion Utility): Correctly Extract Atikmdag.sys ! Microsoft has a built-in file expansion utility to expand certain files. You can expand the original drivers and replace it with your current, fixing any possible problems by restoring the original state. Sounds simple but a few steps are required: 0. 1. 2. 3.
Simply enter atikmdag.sy_ into the search bar 4. C:\AMD\Support\12-4_vista_win7_64_dd_ccc\Packages\Drivers\Display\W76A_INF\B136646 5. 6. 7. 8. Note, there is a space between the two filenames, else you will get an error No destination specified for: atikmdag.sy_ 9. 10. 11. 12. Alright, now why do you get the blue screen in the first place? Still Problems? If this does not fix your problem, please post the entire blue screen error code below so we can analyze this.
Web Application finger printing. Joomla URL pattern: Portal URL Pattern: /_layouts/*And similarly for majority of applications we can create regular expression rules to identify them.These regular expression’s combined together as a monolithic tool to identify all in one go or as a pluggable architecture for creating one pattern file for each type and work on it.

Example of tools using this technique includes browser plugin’s like Wapplyzer and web technology finder and similar tools.File and Folder Presence (HTTP response codes)This approach doesn’t download the page however it starts looking for obvious trails of an application by directly hitting the URL and in course identifying found and not found application list. In starting days of internet this was easy, just download headers and see if it’s 200 OK or 404 not found and you are done. However in current scenario, people have been putting up custom 404 Pages and are actually sending 200 OK in case the page is not found. Configure Hyper-V Host Network Adapters Like A Boss. Configure Hyper-V Host Network Adapters Like A Boss Posted in Hyper-V, IT, Microsoft, Powershell, Private Cloud, Server Core, Software, Virtualization, Web, Windows, Windows Server, Windows Server 2008 R2, Windows Server 2012, Windows Server 8, Work If you are working a lot with Hyper-V and Hyper-V Clustering you know that something that takes a lot of time is configure the Hyper-V Host Network Adapters.
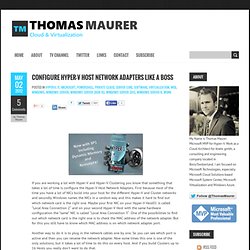
First because most of the time you have a lot of NICs build into your host for the different Hyper-V and Cluster networks and secondly Windows names the NICs in a random way and this makes it hard to find out which network card is the right one. Pearltrees. EyeWitness - A Rapid Web Application Triage Tool. StumbleUpon Diigo Delicious We, at ehacking used to share tools that can make the penetration testing process easy and effective.
You might have seen EH Tools shared before and you will witness the tools that we will share later, but today I have an interesting tool to discuss; it’s called EyeWitness. Chris Truncer is the man behind this tool; it has been designed to run on Kali Linux. EyeWitness is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible. What happens if you write a TCP stack in Python? - Julia Evans. During Hacker School, I wanted to understand networking better, and I decided to write a miniature TCP stack as part of that.
I was much more comfortable with Python than C and I’d recently discovered the scapy networking library which made sending packets really easy. So I started writing teeceepee! The basic idea was open a raw network socket that lets me send TCP packetssend a HTTP request to GET google.comget and parse a responsecelebrate! I didn’t care much about proper error handling or anything; I just wanted to get one webpage and declare victory :) Step 1: the TCP handshake.
How to read command line arguments in a bash script. To input arguments into a Bash script, like any normal command line program, there are special variables set aside for this The arguments are stored in variables with a number in the order of the argument starting at 1 First Argument: $1 Second Argument: $2 Third Argument: $3 Example command: .
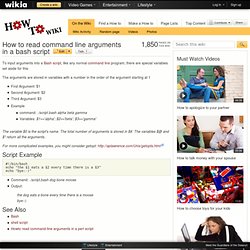
/script.bash alpha beta gammaVariables: $1=='alpha'; $2=='beta'; $3=='gamma' The variable $0 is the script's name.The total number of arguments is stored in $#. The variables $@ and $* return all the arguments. For more complicated examples, you might consider getopt: #! Writing nmap nse scripts for vulnerability scanning. Nmap Scripting Engine became a part of the mainline codebase with the release of Nmap 4.21ALPHA1 back in December, 2006.

Today, the NSE library has grown to more than 400 scripts covering an amazing array of different network technologies (from SMB vulnerability checks to Stuxnet detection and everything in between). The power of NSE lies in its versatile library collection which allows easy interaction with most major network services and protocols.
Often times it is necessary to scan a large number of hosts for a new vulnerability which does not yet have signatures in existing scanning engines. The challenge is to quickly develop a signature and scan your enterprise to enumerate hosts running the application and check them for the vulnerability. Manage and Limit Download/Upload Bandwidth with Trickle in Linux. Have you ever encountered situations where one application dominated you all network bandwidth?

If you have ever been in a situation where one application ate all your traffic, then you will value the role of the trickle bandwidth shaper application. Either you are a system admin or just a Linux user, you need to learn how to control the upload and download speeds for applications to make sure that your network bandwidth is not burned by a single application. What is Trickle? Trickle is a bandwidth shaper tool which can be used to limit the bandwidth usage of programs such as Firefox, FTP , SSH and many other applications that make use of the network bandwidth. Achieving Anonymity with Tor Part 2: Proxies and DNS servers. 1.
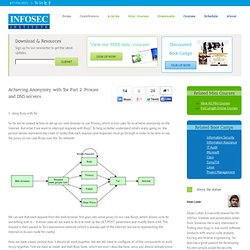
Using Burp with Tor So far we’ve looked at how to set up our web browser to use Privoxy, which in turn uses Tor to achieve anonymity on the Internet. But what if we want to intercept requests with Burp? To help us better understand what’s really going on, the picture below represents the chain of nodes that each request (and response) must go through in order to be able to use the proxy (in our case Burp) over the Tor network: Cutorrent.1.0.beta1.tar.gz - cutorrent - Initial release (Beta) - A command-line tool for uTorrent. Garder une fenêtre dos ouverte - Win NT/2K/XP. Failles de sécurité dans les Gadgets, Microsoft recommande leur désactivation dans Windows Vista et 7. MAJESTIK FORTRESS › Connexion. Uploading .webm videos. @Seacoast Web Design I could be sorely deficient in my understanding of mime types here, but I'm thinking you might be able to increase the allowed file upload size all day long, and it still wouldn't matter.
I'm getting the impression that size is the secondary consideration in this case. But wait.. "Why? " You ask? How to set a video's duration in FFMPEG? Ffmpeg - How to create a webm video file? List of available directshow screen capture filters. VLC itself has a “capture desktop” mode though apparently it doesn’t work with sound. It feels a tidge slower than (if you’re on Windows) using a directshow input source that also captures the desktop. Here’s a list of the ones I’ve found that are free to download. (my own, a shameless plug–it’s free and open source!) Download it from here: uscreencapture, works ok.
Other options: seems quick, though I haven’t looked at them too closely (note: it expires after a time trial, so after that point you can no longer use it after that time without purchasing it). pretty fast, adds a water mark to your output though unless you pay. $500. Capture/Desktop. Linux ¶ Use the x11grab device: ffmpeg -video_size 1024x768 -framerate 25 -f x11grab -i :0.0+100,200 output.flv This will grab the image from desktop, starting with the upper-left corner at (x=100, y=200) with the width and height of 1024x768. Creating Screencasts in Linux « Dennis Nienhüser. Recording screencasts and post-processing them for publishing on sites like YouTube or as HTML5 videos was a tedious and error-prone task for me up until some months ago: Recording software like recordMyDesktop, istanbul or xvidcap didn’t produce good results, if working at all. Video editors like avidemux, cinelerra, kdenlive or kino were lacking important features, had a cumbersome user interface or crashed in the twinkling of an eye.
Fortunately things changed when I discovered that ffmpeg works great for taking raw screencasts and when kdenlive 0.8.2 was released. Kdenlive had always been a promising application: A solid set of features, more than I probably ever need, arranged in a convenient user interface. Yet I was never able to accomplish even the simplest task with it in earlier versions — it almost certainly crashed somewhere in between. This behavior has changed significantly in recent versions – I’ve produced a bunch of videos with it now without a single crash.
Mod rewrite - How to enable mod_rewrite for Apache 2.2. Locate. Un article de Wikipédia, l'encyclopédie libre. Cowlibob/rubyscript2exe. Rubyscript2exe.rb and 623 Can't modify frozen string (Type Error) A tiny bug Today I bumped into this error in rubyscript2exe.rb: rubyscript2exe.rb:623:in `replace': can't modify frozen string (TypeError) I'm using ruby 1.8.6 (2008-08-08 patchlevel 286) [i686-linux] and rubyscript2exe.rb version 0.5.3 (29.05.2007) which is the latest to this date. However the forementioned error occurs when trying to run rubyscript2exe.rb. Ungoogled. RubyScript2Exe - A Ruby Compiler. A Ruby Compiler Tue May 29 20:09:00 UTC 2007Erik Veenstra <rubyscript2exe@erikveen.dds.nl> PDF version (A4) 1. Successfully using OCRA with Watir. Mar 16. Packaging a ruby script as an Windows exe using OCRA.
Windows - Ruby 2 Exe tool. Unicode - How to get rid of non-ascii characters in ruby. Wpa. !! Installation. For up to date installation instructions download Homebrewer’s Guide to Watir book. How To Write Your First Ruby Web Bot In Watir. Time for the fun stuff now. NOVA the Network Obfuscation and Virtualized Anti-Reconnaissance v12.6 available. Rooted Warfare 2014 Spain Wrap-up Part 1. ToolsWatch was present at Rooted CON, the most important security conference in Spain to organize the Rooted Warfare, similar to the Black Hat Arsenal edition, allowing auditors, penetration testers and security experts present and show their tools to the community and interact with attendees.
This time Rooted CON was held the 6, 7 and 8 March, being 7 and 8 with Rooted Warfare. To me (maxisoler) was amazing stay with the Spanish community, colleagues and friends, while others only knew through Twitter or blogs as Security By Default. During these days were presented 12 amazing tools! We will starting to publish videos and more pictures about it. Schedule. Passing the Hash with Remote Desktop. GARD Pro Not Registered Kali Linux contains a large number of very useful tools that are beneficial to information security professionals.
11.04 - Possible missing firmware /lib/firmware/rtl_nic/rtl8105e-1.fw for module r8169 with 2.6.39 kernel. Linuxtricks : [KDE] Autoriser root à se connecter en graphique - Documentation. Disable PC Speaker Beep. Introduction. Installation rapide de LAMP (Apache+MySql+php) sous Linux. Shellter v1.4. BTB Security - How to make custom exes for deployment via psexec in Metasploit. Offensive Security Blog V2.0. Anti-virus evasion – 2. Using custom shellcode. Malware, comment éviter la détection par les antivirusBlog sur la Sécurité Informatique. Reverse Shell - 0x0ff.info. Antivirus : technique d'évasion des logiciels espions - 0x0ff.info. Device Drivers Vulnerability Research, Avast a real case. How to Setup a VPN (PPTP) Server on Debian Linux. HTML5 Video Player.
Add extra driver. Interpreted Languages: JavaScript, PHP, Python, Ruby (Sheet One) Distributing Ruby Applications - Theory and Practice of Building, Packing and Distributing Ruby Applications. Null. YGN Ethical Hacker Group (YEHG) Better, Faster, Stronger: DLLHijack... Exploiting DLL Hijacking Flaws.
Créer une page de téléchargements pour votre blog WordPress. IT From All Angles » Hyper-V Guests: Mouse Integration on Linux VMs. Debian v7.0 on Hyper-V. How to install Hyper-V Integration Services (ICs) in Ubuntu 12.04 LTS. Configuring Hyper-V for multiple subnets with only one NIC (Server 2012 R2 Edition) - LetsDoThis. Ruby en vingt minutes. Modèle de courrier de recours contre une radiation pour absence suite à une convocation non reçue. Good tools that fit on a thumb drive. Wallpaper Art. Cortana Tutorial - cortana_tutorial.pdf. Armitage Tutorial - Cyber Attack Management for Metasploit. r57.txt - c99.txt - r57 shell - c99 shell - r57shell - c99shell - r57 - c99 - shell archive - php shells - php exploits - bypass shell - safe mode bypass - sosyete safe mode bypass shell - Evil Shells - exploit - root - localshell.net.
.: Mirror-Zone :. Kernel panic not syncing vfs unable to mount root fs on unknown block oo swapper not tainted. Mounting a raw partition file made with dd or dd_rescue in Linux. ImageX - Create an ISO from a VHD. [UPDATED] DNS Scraping for Corporate AV Detection - "Admins, stop sharing your cache with everyone!" Jeanne d'Hack. Podcast 6 - Jeanne d'Hack le podcast.
MAJESTIK FORTRESS. Transistor Radio Hack! CSAW 2012 CTF - Exploit 300 Writeup - codezen.fr. Utilman.exe : changer son mot de passe oublié au démarrage de Windows. Light Linux Distributions - Hardware Testing (RAM) Open source boot firmware [docs] Installation. ART DU WEB - DEPLOIEMENT - boot PXE avec DRBL-TFTP-DHCP. Variable d'environnement.
HTTPS et HSTS : Duo gagnant. Ettercap - multipurpose sniffer/content filter for man in the middle. Ettercap/share/etter.filter.examples at master · Ettercap/ettercap. Ettercap Tutorial: DNS Spoofing & ARP Poisoning Examples. INFO : Run, RunOnce, RunServices, RunServicesOnce et Startup. Lancer un script au premier lancement uniquement ? - Win NT/2K/XP. Find & Remove Duplicate Bookmarks With Ease In Firefox. Deploying Metasploit's Meterpreter with MITM and an Ettercap filter. Shell is coming ...: Metasploit: Man in the Middle through PPTP tunnel. Nullsecurity.