

Martes 29 de septiembre @ Cereté, Montería. DEEP WEB: What is It? Amazing Documentary 2015. The Secret Web: Where Drugs, Porn and Murder Live Online. You are getting a free preview of a TIME Magazine article from our archive.
Many of our articles are reserved for subscribers only. Want access to more subscriber-only content, click here to subscribe. On the afternoon of Oct. 1, 2013, a tall, slender, shaggy-haired man left his house on 15th Avenue in San Francisco. He paid $1,000 a month cash to share it with two housemates who knew him only as a quiet currency trader named Josh Terrey. His real name was Ross Ulbricht. The FBI believes Ulbricht is a criminal known online as the Dread Pirate Roberts, a reference to the book and movie The Princess Bride. Technically the Deep Web refers to the collection of all the websites and databases that search engines like Google don’t or can’t index, which in terms of the sheer volume of information is many times larger than the Web as we know it. The Deep Web has plenty of valid reasons for existing.
Most people who use the Deep Web aren’t criminals. Video-About Deep Web. Une plongée au fin fond des abimes d'internet - Bienvenue dans le Deep-Web - Chronique d'une vie de bloggeur. Il est rare que je vous parle de la toile, mais il existe une face cachée de l'internet.
Cómo navegar en la internet profunda (Deep Web) Los motores de búsqueda como Google registran más de un billón de páginas en la Red informática mundial (World Wide Web), pero hay información a la que ellos no tienen acceso.
La mayoría de estas bases de datos deben buscarse directamente desde el sitio web específico. La internet profunda es famosa (o infame) por albergar una pequeña parte de las comunidades súper secretas que recurren a ella para evitar que las autoridades las identifiquen. Anuncio Pasos Método 1 de 2: Buscar bases de datos de la internet profunda <img alt="Search the Deep Web Step 1 Version 3.jpg" src=" width="670" height="512">1Ubica las bases de datos utilizando un motor de búsqueda convencional. <img alt="Search the Deep Web Step 4 Version 3.jpg" src=" width="670" height="512">4Navega por el sitio Internet Archive.El proyecto Internet Archive trata de recolectar la información digital para guardarla a largo plazo. The Ultimate Guide to the Invisible Web. Search engines are, in a sense, the heartbeat of the internet; “Googling” has become a part of everyday speech and is even recognized by Merriam-Webster as a grammatically correct verb.

It’s a common misconception, however, that Googling a search term will reveal every site out there that addresses your search. Typical search engines like Google, Yahoo, or Bing actually access only a tiny fraction — estimated at 0.03% — of the internet. The sites that traditional searches yield are part of what’s known as the Surface Web, which is comprised of indexed pages that a search engine’s web crawlers are programmed to retrieve.
Memo_WebInvisible.pdf. Timeline of events related to the Deep Web. Wp-deepweb-and-cybercrime.pdf. 'Tor Stinks' presentation – read the full document. Tor (red de anonimato) /chapter: Tor-The-Onion-Router / Circumvention Tools. Tor (The Onion Router) is a very sophisticated network of proxy servers.
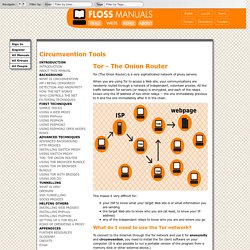
When you are using Tor to access a Web site, your communications are randomly routed through a network of independent, volunteer proxies. All the traffic between Tor servers (or relays) is encrypted, and each of the relays knows only the IP address of two other relays -- the one immediately previous to it and the one immediately after it in the chain. This makes it very difficult for: your ISP to know what your target Web site is or what information you are sending the target Web site to know who you are (at least, to know your IP address) any of the independent relays to know who you are and where you go What do I need to use the Tor network?
To connect to the Internet through the Tor network and use it for anonymity and circumvention, you need to install the Tor client software on your computer. Tor is compatible with most versions of Windows, Mac OS X and GNU/Linux. With what software is Tor compatible? 1. .onion. Initiation à I2P. Je n'ai encore jamais pris le temps de vous présenter i2p !
C'est mal. I2P. I2P (sigla para Invisible Internet Project, que significa Proyecto de Internet invisible) es un software que ofrece una capa de abstracción para comunicaciones entre ordenadores, permitiendo así la creación de herramientas y aplicaciones de red con un fuerte anonimato.
Sus usos incluyen páginas webs anónimas (eepsitees), servidores y clientes de chat, blogging, transferencia de archivos, además es una red que se adapta muy bien a las redes p2p. I2P es software libre y utiliza varias licencias libres. Funcionamiento[editar] Online Survival Kit. Reporters sans frontières et Tor serveurs, partenaires contre la surveillance et la censure en ligne. Reporters sans frontières et Torservers.net s’associent pour créer et maintenir 250 serveurs supplémentaires au sein du réseau Tor.
“C’est un véritable pied de nez que ces deux organisations font aux censeurs du monde entier. Quels que soient les moyens techniques déployés pour contrôler l’information, il existera toujours des solutions de contournement que de nombreuses organisations y compris la nôtre n’hésiteront pas à déployer” a déclaré Grégoire Pouget, responsable du bureau Nouveaux médias. “L’anonymat est essentiel dans la pleine expression et la réalisation des libertés civiles. Fight for the Future, defending our basic rights and freedoms. The Internet Defense League - Protecting the Free Internet since 2012. Torservers.net - Tor Exit Node & Bridge hosting. La totalité de nos communications espionnées par un supercalculateur.
Enquête.
La DGSE collecte et stocke l'ensemble des mails, SMS, relevés d'appels téléphoniques, accès à Facebook, Twitter..., en dehors de tout contrôle. Si les révélations sur le programme d'espionnage américain Prism ont provoqué un concert d'indignation en Europe, la France, elle, n'a que faiblement protesté. Pour deux excellentes raisons : Paris était déjà au courant. Et fait la même chose. TorHiddenWiki.com. Massive Deep Web Links 2015 [UPDATED June 2015]
Tor .onion urls directories. Programa Monedas de Redes Caracol tv. Colombia Security Threats – Data and Information. In Febraury 2014, Interpol and Europol reported on global raids conducted against producers and sellers of counterfeit foods.
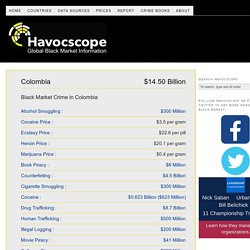
In total, over 1,200 tonnes of counterfeit and substandard food and nearly 430,000 liters of counterfeit beverages were seized across 33 countries. 96 people were arrested by various criminal justice programs during the investigation. Highlights of the campaign against counterfeit foods: Across Europe, over 131,000 liters of fake oil and vinegar , 80,000 counterfeit biscuits and chocolate bars, 20 tonnes of fake spices and condiments, and 45 tonnes of substandard dairy products were seized by Europol.In Italy, 60,000 bottles and labels of fake champagne was seized.Police in Thailand found over 270 bottles of fake whiskey.$17.2 Million worth of counterfeit foods and drinks were seized in Colombia. Source: “Global police swoop seizes millions in fake food, drink,” Channel NewsAsia, February 14, 2014. (Additional examples of money laundering cases worldwide.) Qwant. Lilo, le moteur de recherche qui finance des projets sociaux.
Diplomeo : Orientation après bac - Trouver la bonne formation. Memex Helps Find Human Trafficking Cases Online. Share this: By Seth Daire, Associate In February 2015 the Defense Advanced Research Projects Agency (DARPA), an agency of the U.S. Department of Defense, announced the Memex program, which aims to create new internet search engine technologies that better discover, organize, and present information relating to specific subjects. Their initially stated goal is to apply Memex to fight human trafficking, which is a “key Defense Department mission.” According to DARPA, human trafficking is facilitated over the Internet through the use of forums, chat services, ads, and job postings. Google is part of the surface web. The Tor network is also a part of the deep web, though some mistakenly say it is on the dark web, which is a part of the web no longer accessible with an Internet connection. Tor has gained notoriety as a connecting point for illicit purposes, such as the Silk Road marketplace that the FBI shut down in 2013.
Indexing is only part of the goal. Photo credit: Seth Daire. i03.pdf.