

NSA Trying To Map Internet, Including Devices, In Real-Time. Tweet The National Security Agency, along with its British counterpart the Government Communications Headquarters, and several other nations are secretly trying to map the entire Internet in real-time, creating a worldwide surveillance tool on the scale of Google Earth.
Spiegel Online reports the ambitious program, codenamed “Treasure Map” (complete with its own glowing skull moniker) seeks to identify Internet routers and millions of individual devices in order to create an ”interactive map of the global Internet” in “near real-time,” which would allow intelligence analysts to “map the entire Internet — any device, anywhere, all the time,” according to documents leaked by ex-NSA contractor Edward Snowden. Core Secrets: NSA Saboteurs in China and Germany. The National Security Agency has had agents in China, Germany, and South Korea working on programs that use “physical subversion” to infiltrate and compromise networks and devices, according to documents obtained by The Intercept.

The documents, leaked by NSA whistleblower Edward Snowden, also indicate that the agency has used “under cover” operatives to gain access to sensitive data and systems in the global communications industry, and that these secret agents may have even dealt with American firms. The documents describe a range of clandestine field activities that are among the agency’s “core secrets” when it comes to computer network attacks, details of which are apparently shared with only a small number of officials outside the NSA. How the NSA Could Bug Your Powered-Off iPhone, and How to Stop Them.
Photo: Josh Valcarcel/WIRED Just because you turned off your phone doesn’t mean the NSA isn’t using it to spy on you.
Edward Snowden’s latest revelation about the NSA’s snooping inspired an extra dose of shock and disbelief when he said the agency’s hackers can use a mobile phone as a bug even after it’s been turned off. The whistleblower made that eye-opening claim when Brian Williams of NBC Nightly News, holding his iPhone aloft during last Wednesday’s interview, asked, “What can the NSA do with this device if they want to get into my life? La NSA cherche un détecteur de sarcasme 10.06.2014 - rts.ch - audio - la 1ère.
The ultimate goal of the NSA is total population control. In NSA-intercepted data, those not targeted far outnumber the foreigners who are. Ordinary Internet users, American and non-American alike, far outnumber legally targeted foreigners in the communications intercepted by the National Security Agency from U.S. digital networks, according to a four-month investigation by The Washington Post.
Nine of 10 account holders found in a large cache of intercepted conversations, which former NSA contractor Edward Snowden provided in full to The Post, were not the intended surveillance targets but were caught in a net the agency had cast for somebody else. Many of them were Americans. John Key says Edward Snowden ‘may well be right’ about NSA spying on NZ. The claim by Edward Snowden that New Zealanders’ internet traffic is accessible through a NSA intelligence database “may well be right”, the country’s prime minister, John Key, has acknowledged.
Key refused on Wednesday to rule out that New Zealanders’ metadata was being intercepted by American intelligence, telling local media: “I don’t run the NSA any more than I run any other foreign intelligence agency or any other country”. But he denied that agents from the country’s spy agency, the Government Communications Security Bureau (GCSB), were helping feed mass Kiwi metadata into the vast and controversial database known as XKeyscore. NSA Memo Says Agency Is 'Blurring The Lines' Between Terrorism And Drugs. The National Security Agency is "blurring the lines" between the war on drugs and the war on terror, according to a memo produced by the spy agency itself and published Monday by Glenn Greenwald's new website The Intercept.
The partially classified 2004 memo, written by an unnamed NSA employee who served as the Drug Enforcement Administration's "account manager," provides one of the most revealing glimpses yet at the ways counterterrorism and counternarcotics operations have melded since Sept. 11, 2001. Counternarcotics has been a major Defense Department mission since 1989, when President George H.W. Bush gave a speech announcing ramped up funding for a militarized approach to the drug war. Three months later, the U.S. invaded Panama, ostensibly to combat drug trafficking under strongman leader Manuel Noriega. Le monde orwellien, nous y sommes... mais ce qu’on perd en liberté vaut-il vraiment ce qu’on y gagne ? Atlantico : Selon de nouvelles révélations du New York Times, sur la bases des données d'Edward Snowden, la NSA aurait collecté des millions de photos pour améliorer leur technologie de reconnaissance faciale.
Y a-t-il des limites aux données collectées sur chacun de nous ?
NSA surveillance program reaches ‘into the past’ to retrieve, replay phone calls. The voice interception program, called MYSTIC, began in 2009.
Its RETRO tool, short for “retrospective retrieval,” and related projects reached full capacity against the first target nation in 2011. Planning documents two years later anticipated similar operations elsewhere. In the initial deployment, collection systems are recording “every single” conversation nationwide, storing billions of them in a 30-day rolling buffer that clears the oldest calls as new ones arrive, according to a classified summary. Edward Snowden Reveals NSA's MonsterMind Program.
In the high desert near Bluffdale, Utah, there lurks a creature made entirely of zeroes and ones. Called "MonsterMind", the project is an automated cyber weapon, perched atop the data flows into the National Security Agency's Mission Data Repository. According to recent revelations from former government contractor and NSA leaker Edward Snowden, Monstermind is both tremendously powerful and easily fooled. Here's the skinny on the biggest revelation from Wired's recent profile of Snowden. Author James Bamford writes: The massive surveillance effort was bad enough, but Snowden was even more disturbed to discover a new, Strangelovian cyberwarfare program in the works, codenamed MonsterMind.
Programs like this had existed for decades, but MonsterMind software would add a unique new capability: Instead of simply detecting and killing the malware at the point of entry, MonsterMind would automatically fire back, with no human involvement. La NSA prend 8 secondes pour détourner votre webcam. La NSA, ce mal qui nous veut du bien ?
L'agence américaine de renseignement a développé des logiciels malveillants utilisés à très grande échelle, qui lui permettent de pirater les données de millions d'ordinateurs, selon des documents transmis par Edward Snowden et révélés par le site du magazine en ligne The Intercept. D'après les informations dévoilées par l'ancien journaliste du Guardian Glenn Greenwald, l'agence a implanté dans des millions d'ordinateurs des logiciels malveillants qui lui permettent d'extraire des données de réseaux téléphoniques et internet à l'étranger. Collecte de données à une "échelle industrielle" Ces logiciels, destinés au départ à quelques centaines de cibles dont les communications ne pouvaient pas être surveillées par des moyens traditionnels, ont été étendus par la suite à une "échelle industrielle".
Leur but est de réduire l'utilisation que fait la NSA du renseignement humain. Installation du logiciel en moins de 10 secondes. Barack Obama's Secret Terrorist-Tracking System, by the Numbers - The InterceptThe Intercept. Nearly half of the people on the U.S. government’s widely shared database of terrorist suspects are not connected to any known terrorist group, according to classified government documents obtained by The Intercept.
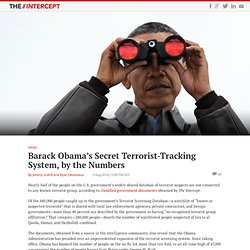
Of the 680,000 people caught up in the government’s Terrorist Screening Database—a watchlist of “known or suspected terrorists” that is shared with local law enforcement agencies, private contractors, and foreign governments—more than 40 percent are described by the government as having “no recognized terrorist group affiliation.” That category—280,000 people—dwarfs the number of watchlisted people suspected of ties to al Qaeda, Hamas, and Hezbollah combined. How the NSA Plans to Infect 'Millions' of Computers with Malware. One presentation outlines how the NSA performs “industrial-scale exploitation” of computer networks across the world. Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process.
The classified files – provided previously by NSA whistleblower Edward Snowden – contain new details about groundbreaking surveillance technology the agency has developed to infect potentially millions of computers worldwide with malware “implants.” The clandestine initiative enables the NSA to break into targeted computers and to siphon out data from foreign Internet and phone networks. The covert infrastructure that supports the hacking efforts operates from the agency’s headquarters in Fort Meade, Maryland, and from eavesdropping bases in the United Kingdom and Japan. “That would definitely not be proportionate,” Hypponen says. NSA Built Back Door In All Windows Software by 1999.
OK COMPUTER – Des images très compromettantes pour la NSA. NSA seeks to build quantum computer that could crack most types of encryption. [Read an annotated description of the Penetrating Hard Targets project] The development of a quantum computer has long been a goal of many in the scientific community, with revolutionary implications for fields such as medicine as well as for the NSA’s code-breaking mission. With such technology, all current forms of public key encryption would be broken, including those used on many secure Web sites as well as the type used to protect state secrets. Classifying NSA quantum computing efforts. A description of the Penetrating Hard Targets project.
How The NSA Hacks Your iPhone (Presenting DROPOUT JEEP) Following up on the latest stunning revelations released yesterday by German Spiegel which exposed the spy agency's 50 page catalog of "backdoor penetration techniques", today during a speech given by Jacob Applebaum (@ioerror) at the 30th Chaos Communication Congress, a new bombshell emerged: specifically the complete and detailed description of how the NSA bugs, remotely, your iPhone. The way the NSA accomplishes this is using software known as Dropout Jeep, which it describes as follows: "DROPOUT JEEP is a software implant for the Apple iPhone that utilizes modular mission applications to provide specific SIGINT functionality.
This functionality includes the ability to remotely push/pull files from the device. SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic, camera capture, cell tower location, etc. Command, control and data exfiltration can occur over SMS messaging or a GPRS data connection. Vodafone reveals existence of secret wires that allow state surveillance. Vodafone, one of the world's largest mobile phone groups, has revealed the existence of secret wires that allow government agencies to listen to all conversations on its networks, saying they are widely used in some of the 29 countries in which it operates in Europe and beyond. The company has broken its silence on government surveillance in order to push back against the increasingly widespread use of phone and broadband networks to spy on citizens, and will publish its first Law Enforcement Disclosure Report on Friday.
At 40,000 words, it is the most comprehensive survey yet of how governments monitor the conversations and whereabouts of their people. The company said wires had been connected directly to its network and those of other telecoms groups, allowing agencies to listen to or record live conversations and, in certain cases, track the whereabouts of a customer. "I never thought the telcos [telecommunications companies] would be so complicit. Catalog Reveals NSA Has Back Doors for Numerous Devices. Editor's note: This article accompanies our main feature story on the NSA's Tailored Access Operations unit. You can read it here. When it comes to modern firewalls for corporate computer networks, the world's second largest network equipment manufacturer doesn't skimp on praising its own work. According to Juniper Networks' online PR copy, the company's products are "ideal" for protecting large companies and computing centers from unwanted access from outside.
NSA monitored calls of 35 world leaders after US official handed over contacts. The National Security Agency monitored the phone conversations of 35 world leaders after being given the numbers by an official in another US government department, according to a classified document provided by whistleblower Edward Snowden. The confidential memo reveals that the NSA encourages senior officials in its "customer" departments, such as the White House, State and the Pentagon, to share their "Rolodexes" so the agency can add the phone numbers of leading foreign politicians to their surveillance systems. The document notes that one unnamed US official handed over 200 numbers, including those of the 35 world leaders, none of whom is named. How NSA access was built into Windows. A CARELESS mistake by Microsoft programmers has revealed that special access codes prepared by the US National Security Agency have been secretly built into Windows.
NSA surveillance: don't underestimate the extraordinary power of metadata. 'To be remembered after we are dead," wrote Hazlitt, "is but poor recompense for being treated with contempt while we are living. " The NSA/GCHQ metadata reassurances are breathtakingly cynical. Me and my metadata – thoughts on online surveillance. Posted by Ethan on Jul 3rd, 2013 in CFCM, Human Rights, ideas | 6 comments. Attacking Tor: how the NSA targets users' online anonymity. NSA and GCHQ target Tor network that protects anonymity of web users. Peeling the onion: Almost everyone involved in developing Tor was (or is) funded by the US government. “The United States government can’t simply run an anonymity system for everybody and then use it themselves only.
Because then every time a connection came from it people would say, “Oh, it’s another CIA agent.” Unlocking Private Communications - Graphic. Agreements with private companies protect U.S. access to cables’ data for surveillance. In months of private talks, the team of lawyers from the FBI and the departments of Defense, Justice and Homeland Security demanded that the company maintain what amounted to an internal corporate cell of American citizens with government clearances. Among their jobs, documents show, was ensuring that surveillance requests got fulfilled quickly and confidentially. This “Network Security Agreement,” signed in September 2003 by Global Crossing, became a model for other deals over the past decade as foreign investors increasingly acquired pieces of the world’s telecommunications infrastructure.
The publicly available agreements offer a window into efforts by U.S. officials to safeguard their ability to conduct surveillance through the fiber-optic networks that carry a huge majority of the world’s voice and Internet traffic. Linux creator admits NSA demanded backdoor. Sous-marin: L'USS Jimmy Carter, les oreilles de la NSA au fond des mers - News Monde: Amériques. Court gave NSA broad leeway in surveillance, documents show.