

Choosing Secure Passwords. As insecure as passwords generally are, they're not going away anytime soon.
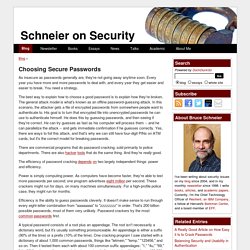
Every year you have more and more passwords to deal with, and every year they get easier and easier to break. You need a strategy. The best way to explain how to choose a good password is to explain how they're broken. The general attack model is what's known as an offline password-guessing attack. In this scenario, the attacker gets a file of encrypted passwords from somewhere people want to authenticate to. There are commercial programs that do password cracking, sold primarily to police departments. Ask Ars: Where should I store my passwords? Ask Ars was one of the first features of the newly born Ars Technica back in 1998.
And now, as then, it's all about your questions and our community's answers. Each week, we'll dig into our bag of questions, answer a few based on our own know-how, and then we'll turn to the community for your take. To submit your own question, see our helpful tips page. Question: What are the best practices when using a password-keeping service, and what are the merits and disadvantages of local vs. cloud-based password storage? With every website requiring users to register a password-protected account to see its content, password management systems have become very popular. Strong Passwords NEED Entropy. I just finished reading an article on Ars Technica titled "Ask Ars: Where should I store my passwords?

". There was a specific paragraph that I took issue with, which in turn prompted me to write this post. It is: "Still, it would take thousands of years to crack an 8-character password when checking both small and capital letters, spaces, and numbers. Password Strength. Password Reuse. How much entropy in that password? The disagreement boils down to Randall giving a lower bound on the entropy, and Steve giving an upper bound (and not realizing—or neglecting to mention—the difference).

Randall is right, and Steve is wrong. Let me explain: In both passwords featuring in the comic, Randall assumes a particular password template—in effect, an automatic procedure where you input some number of random bits and get a password. An example, similar to (but simpler than) the first of the comic’s password templates: Pick a six-letter dictionary word (in lowercase), capitalize one of the letters, and stick a number at the end. Supreme Court to Cops Who Want to Search Your Cellphone: Get a Warrant. On Wednesday, the Supreme Court unanimously ruled that police generally may not search the cellphones of Americans who have been arrested without a search warrant.
Password Protect Your Devices - In Photos: 10 Incredibly Simple Things You Can Do To Protect Your Privacy. Ten Million More Android Users' Text Messages Will Soon Be Encrypted By Default. FAQ: How Real ID will affect you. An update on our war against account hijackers. Have you ever gotten a plea to wire money to a friend stranded at an international airport?
An oddly written message from someone you haven’t heard from in ages? Compared to five years ago, more scams, illegal, fraudulent or spammy messages today come from someone you know. Although spam filters have become very powerful—in Gmail, less than 1 percent of spam emails make it into an inbox—these unwanted messages are much more likely to make it through if they come from someone you’ve been in contact with before. As a result, in 2010 spammers started changing their tactics—and we saw a large increase in fraudulent mail sent from Google Accounts.
In turn, our security team has developed new ways to keep you safe, and dramatically reduced the amount of these messages. Ligthbeam for Firefox. Tracking & privacy.
EFF Surveillance Self-Defense Project. Ten Steps You Can Take Right Now Against Internet Surveillance. One of the trends we've seen is how, as the word of the NSA's spying has spread, more and more ordinary people want to know how (or if) they can defend themselves from surveillance online.

But where to start? The bad news is: if you're being personally targeted by a powerful intelligence agency like the NSA, it's very, very difficult to defend yourself. The good news, if you can call it that, is that much of what the NSA is doing is mass surveillance on everybody. NSA surveillance: how to stay secure. Now that we have enough details about how the NSA eavesdrops on the internet, including today's disclosures of the NSA's deliberate weakening of cryptographic systems, we can finally start to figure out how to protect ourselves.
For the past two weeks, I have been working with the Guardian on NSA stories, and have read hundreds of top-secret NSA documents provided by whistleblower Edward Snowden. I wasn't part of today's story – it was in process well before I showed up – but everything I read confirms what the Guardian is reporting. At this point, I feel I can provide some advice for keeping secure against such an adversary. The primary way the NSA eavesdrops on internet communications is in the network. That's where their capabilities best scale. Leveraging its secret agreements with telecommunications companies – all the US and UK ones, and many other "partners" around the world – the NSA gets access to the communications trunks that move internet traffic. 1) Hide in the network. Encryption Works: How to Protect Your Privacy in the Age of NSA Surveillance. Download: [en] PDF, LibreOffice ODT • [pt] PDF, LibreOffice ODT Encryption works.

Properly implemented strong crypto systems are one of the few things that you can rely on. Unfortunately, endpoint security is so terrifically weak that NSA can frequently find ways around it.— Edward Snowden, answering questions live on the Guardian's website. Know Your Rights! Your computer, your phone, and your other digital devices hold vast amounts of personal information about you and your family. This is sensitive data that's worth protecting from prying eyes - including those of the government.
The Fourth Amendment to the Constitution protects you from unreasonable government searches and seizures, and this protection extends to your computer and portable devices. Michael Price: Digital Privacy at the Border. Until recently, U.S. Customs agents were free to copy every bit of data from your electronic devices. They could read all your documents, see all your pictures, review your browsing history, and even rummage through deleted files - for no reason whatsoever. To cross the border was to totally surrender your digital privacy. But thanks to a decision by the U.S. Court of Appeals for the Ninth Circuit, there is finally a limit on how far the government can go.
Protect Your Data During U.S. Border Searches. From Wired How-To Wiki The mandatory stop at the U.S. Customs counter when returning from an international trip usually just involves answering a few questions and getting a stamp on your passport. But recently, we've seen incidents of computer security experts with ties to WikiLeaks and white hat hackers being stopped by government agents and having their laptops and phones thoroughly inspected. Keep your data safe at the border. There is no right to privacy at international borders.
For those of us with laptops, this presents a pretty major problem: How do we get through U.S. Customs with our beloved portable devices, without having Uncle Sam peeking at every e-mail we've sent, every MP3 we've listened to, and every "home movie" we've made? Security guide to customs-proofing your laptop. If you travel across national borders, it's time to customs-proof your laptop. Customs officials have been stepping up electronic searches of laptops at the border, where travelers enjoy little privacy and have no legal grounds to object. Laptops and other electronic devices can be seized without reason, their contents copied, and the hardware returned hours or even weeks later. EFF's Guide to Protecting Electronic Devices and Data at the U.S. Border. Amid recent reports that security researchers have experienced difficulties at the United States border after traveling abroad, we realized that it's been awhile since we last discussed how to safeguard electronic devices and digital information during border searches.
So just in time for holiday travel and the 27th Chaos Communication Congress in Berlin, here's EFF's guide for protecting your devices and sensitive data at the United States border. The Government Has Broad Legal Authority to Search Laptops, Phones, Cameras, and Other Devices at the U.S. Defending Privacy at the U.S. Border: A Guide for Travelers Carrying Digital Devices.