

Gauss, the Flame malware's 'cousin', targets banks in Lebanon. “Gauss is a nation state sponsored banking Trojan which carries a warhead of unknown designation.
Besides stealing various kinds of data from infected Windows machines, it also includes an unknown, encrypted payload which is activated on certain specific system configurations”, according to a Kaspersky Lab blog. The name of the malware comes from modules that have internal names paying tribute to famous mathematicians and philosophers, such as Johann Carl Friedrich Gauss, Kurt Godel, and Joseph-Louis Lagrange. Since late May 2012, more than 2,500 infections were recorded by Kaspersky Lab’s cloud-based security system, with the estimated total number of victims of Gauss probably being in tens of thousands. Of those infections, more than 1,600 of them were discovered in Lebanon and nearly 500 in Israel, the blog noted. Malware Intelligence Lab:More Flame/sKyWIper CNC Behavior Uncovered. Today, NSS Labs released a report detailing the performance of several vendors’ ability to detect advanced attacks.
We declined to participate in this test because we believe the NSS methodology is severely flawed. In fact, the FireEye product they used was not even fully functional, leveraged an old version of our software and didn’t have access to our threat intelligence (unlike our customers). We did participate in the BDS test in 2013 and at that time we also commented on the flaws of the testing methodology. In fact, we insisted that the only way to properly test was to run in a REAL environment. Iran says detected massive cyber attack: state TV. Flame authors order infected computers to remove all traces of the malware. The creators of the Flame cyber-espionage threat ordered infected computers still under their control to download and execute a component designed to remove all traces of the malware and prevent forensic analysis, security researchers from Symantec said on Wednesday.
Flame has a built-in feature called SUICIDE that can be used to uninstall the malware from infected computers. However, late last week, Flame's creators decided to distribute a different self-removal module to infected computers that connected to servers still under their control, Symantec's security response team said in a blog post . The module is called browse32.ocx and its most recent version was created on May 9, 2012. "It is unknown why the malware authors decided not to use the SUICIDE functionality, and instead make Flamer perform explicit actions based on a new module," the Symantec researchers said.
Deleting a file in Windows does not remove its actual data from the physical hard disk.
Flame malware hijacks Windows Update to spread from PC to PC. The Flame espionage malware targeting Iranian computers contains code that can completely hijack the Windows update mechanism that Microsoft uses to distribute security patches to hundreds of millions of its users, security researchers said Monday.
Flame components known as "Gadget" and "Munch" allow Flame operators to mount a man-in-the-middle attack against computers connected to a local network that hosts at least one machine already infected by the malware, Kaspersky Lab expert Alexander Gostev wrote in a blog post published Monday. By exploiting weaknesses in Microsoft's Terminal Server product—and poor key-management decisions made by Microsoft engineers—the Flame architects were able produce cryptographic seals falsely certifying that their malicious wares had been produced by Microsoft. United Nations views Flame as cybersecurity opportunity. The United Nations has seized on the appearance of the Flame worm, which targeted computers in the Middle East, to argue that it should have more authority to deal with cybersecurity threats on the Internet.
Last week, the United Nations' International Telecommunication Union circulated a statement about Flame saying the malware "reinforces the need for a coordinated response" that could come from "building a global coalition. " A Massive Web of Fake Identities and Websites Controlled Flame Malware. Map showing the number and geographical location of Flame infections on Kaspersky customer machines.
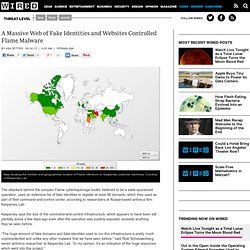
Courtesy of Kaspersky Lab The attackers behind the complex Flame cyberespionage toolkit, believed to be a state-sponsored operation, used an extensive list of fake identities to register at least 86 domains, which they used as part of their command-and-control center, according to researchers at Russia-based antivirus firm Kaspersky Lab. Kaspersky says the size of the command-and-control infrastructure, which appears to have been still partially active a few days ago even after the operation was publicly exposed, exceeds anything they’ve seen before. “The huge amount of fake domains and fake identities used to run this infrastructure is pretty much unprecedented and unlike any other malware that we have seen before,” said Roel Schouwenberg, senior antivirus researcher at Kaspersky Lab.
Flame malware's structure among most complex ever seen, says Kaspersky Lab. Network World - Kaspersky Lab Monday shared more details about the sophisticated cyber-espionage Flame malware widely believed to be the work of a nation-state, though the security firm isn't venturing yet to say what country that might be.
Kaspersky Lab is working with OpenDNS to investigate Flame malware tied most closely to cyber-espionage against Iran and Lebanon, and today both companies described what has been found in a week of investigation of Flame command and control (C&C) servers around the world. These servers are being "sinkholed" slowly to cut off ties between the C&C server and Windows-based computers infected with Flame malware, which spies on computer use and can upload content back to Flame's C&C operators.
Quick guide to Flame malware attack - IT Analysis from V3.co.uk. The security industry has been alight with the news of the Flame malware attack on Iranian IT systems, which represents a significant advancement on the Stuxnet and Duqu attacks from the last two years.
Some security experts have claimed the Flame malware "redefines the notion of cyberwar and cyber-espionage" given its complexity and capabilities. With so much information and conjecture circling around the development V3 aims to answer some of the key questions being asked about the newly discovered cyber weapon.
Flame-bait Questions. There are plenty of questions from customers, and also from members of the press.

Mikko spoke with Clark Boyd of PRI's The World yesterday about the breaking news. Symantec's Liam O Murchu spoke with Kai Ryssdal of Marketplace in a very "economical" conversation about Flame's functionality. Some good questions have been asked. And plenty of hyperbole has been generated. Here are some questions of our own. The Flame Virus: Your FAQs Answered. A frightening computer virus called Flame is on the loose in Iran and other parts of the Middle East, infecting PCs and stealing sensitive data.
Now, the United Nations' International Telecommunications Union warns that other nations face the risk of attack. But what is Flame, exactly, and is it cause for concern among ordinary PC users? Iran 'finds fix' for sophisticated Flame malware. 29 May 2012Last updated at 11:25 ET The sophistication of Flame helped it avoid detection by security software Iran says it has developed tools that can defend against the sophisticated cyber attack tool known as Flame.
The country is believed to have been hit hard by the malicious programme which infiltrates networks in order to steal sensitive data. Security companies said Flame, named after one of its attack modules, is one of the most complex threats ever seen. Iran says its home-grown defence could both spot when Flame is present and clean up infected PCs. Hard work. The Flame Virus: Spyware on an Unprecedented Scale. Security researchers recently discovered one of the most complex instances of computer malware on record. Flame, which also goes by the names SkyWiper and Viper, has infected hundreds of computers across the Middle East and Europe. What does it do? Where did it come from? Who unleashed it? What makes Flame so unusual is its size. “Flame is a sizable beast," said Graham Cluley of Sophos Security, a publisher of digital security software. What's the Meaning of This: Flame Malware. 'No country is safe from Flame super-virus attack' - Kaspersky Labs.
The number of locations of flame infections detected by Kaspersky Labs on their customers' machines. Picture: Kaspersky Labs Source: Supplied A POWERFUL new virus has been uncovered which has been sabotaging government systems for at least five years in the Middle East. The "Flame" program is claimed to be at least 20 times more powerful than any previously known cyber warfare programs. That includes the infamous Stuxnet which attacked Iran’s nuclear program in 2010, causing centrifuges in its new uranium enrichment facility at Bushehr to fail just weeks before it was due to start up.
Stuxnet and its successor, Duqu, have been fingered as viruses so powerful they could only have been created by a state. Flame was discovered by security company Kaspersky, which claims it has been mining Middle East government systems since at least 2010. Flame: Another Holiday, Another Super Virus. Another holiday here in upstate New York, another roll of the fire trucks while some were supposed to be kicking back and enjoying a barbeque. It's times like this when I'm glad I'm not in the antivirus business anymore and doubly relieved that none of our machines run Windows. No flames here. Computer security people however may have to reach for the extinguisher this morning as the latest conflagration in the news bounces across their desk, the discovery of yet another "super virus" called "FLAME" as reported by this BBC article.
Only problem is that according to Kaspersky, who made the discovery in coordination with the U.N.'s International Telecommunications Union (ITU), this one's been in the wild since at least December of 2010 and has only been detected now. Here we go... again. Flame virus: United Nations to issue warning against 'world's most powerful computer bug' 'Flame' bug has been used to hack into Iran computersTrojan superbug 100 times bigger than most forms of malicious software By David Gardner Created: 19:47 GMT, 29 May 2012. Flame virus: who is behind the world's most complicated espionage software?
Attacks on Iranian oil industry led to Flame malware find. Researchers identify Stuxnet-like malware called 'Flame' IDG News Service - A new, highly sophisticated malware threat that was predominantly used in cyberespionage attacks against targets in the Middle East has been identified and analyzed by researchers from several security companies and organizations. According to the Iranian Computer Emergency Response Team (MAHER), the new piece of malware is called Flamer and might be responsible for recent data loss incidents in Iran. There are also reasons to believe that the malware is related to the Stuxnet and Duqu cyberespionage threats, the organization said on Monday. Malware researchers from antivirus firm Kaspersky Lab have also analyzed the malware and found that while it is similar to Stuxnet and Duqu in terms of the geographic propagation and targeting, it has different features and it is, in many ways, more complex than both of those threats.
Flame, as the Kaspersky researchers call it, is a very large attack toolkit with many individual modules. Reprinted with permission from IDG.net. Virus Infects Computers Across Middle East. Researchers identify Stuxnet-like cyberespionage malware called 'Flame' IDG News Service - A new, highly sophisticated malware threat that was predominantly used in cyberespionage attacks against targets in the Middle East has been identified and analyzed by researchers from several security companies and organizations. According to the Iranian Computer Emergency Response Team (MAHER), the new piece of malware is called Flamer and might be responsible for recent data loss incidents in Iran. Flame: world's most complex computer virus exposed.
Meet 'Flame', The Massive Spy Malware Infiltrating Iranian Computers. Skywiper_v1.02.doc.