

France 2018. More Windows. Latest News, Projects & Technical Articles. Teaching Methods. Windows Offline Files Survival Guide. Windows Offline Files have a bad reputation.
Many an administrator can tell a story where Offline Files caused issues that sometimes even required a reinstallation of the affected PC. But Microsoft has gradually improved the functionality and ironed out many of the bugs. Today – in Windows 7 SP1 with all post-SP1 fixes – Offline Files is a technology that still has its problems, but can be used in production – if you are adventurous. This article lists the gotchas I am aware of. Please note: Although this article originally targeted Windows 7, most if not all of its content applies to Windows 8, too.
Documentation If you want to know what is really going on under the hood, you are mostly on your own. Configuration In enterprise environments, Offline Files are configured via Group Policy, the relevant node is Administrative Templates -> Network -> Offline Files. Caution: Most settings do not apply to Windows 7, but to older operating systems. Logging Architecture Permissions.
Amazon.co. In summary, these SDRs are superb device for Radio beginners, discrete projects and for experimentation.
They are very easy to set up and get immediate gratification but complex enough to become a life long obsession too. I have been a licensed Radio Ham since I was a kid and also love programming and hacking but have resisted the SDR craze of the last few years mostly due to ongoing projects and a busy life. Zoomdata. Oracle Database 12c Release 2. Fairmont Park Anson 3 Light Empire Chandelier & Reviews. Embossed Ceiling Hook. Trifacta Hortonworks Solutions Brief. What Is Big Data and What Does It Have to Do With IT Audit?
For many years, IT auditors have been able to rely on comparatively elementary data analysis tools to perform analyses to draw conclusions.
With the recent explosion in the volume of data generated for business purposes (e.g., purchase transactions, network device logs, security appliance alerts), current tools may now not be sufficient. By necessity, big data uses data sets that are so large that it becomes difficult to process them using readily available database management tools or traditional data processing applications. The paradigm shift introduced by big data requires a transformation in the way that such information is handled and analyzed, moving away from deriving intelligence from structured data to discerning insights from large volumes of unstructured data. Difference between Machine Learning, Data Science, AI, Deep Learning, and Statistics. In this article, I clarify the various roles of the data scientist, and how data science compares and overlaps with related fields such as machine learning, deep learning, AI, statistics, IoT, operations research, and applied mathematics.
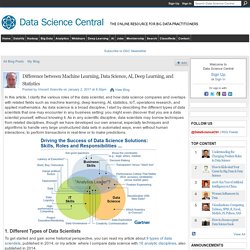
As data science is a broad discipline, I start by describing the different types of data scientists that one may encounter in any business setting: you might even discover that you are a data scientist yourself, without knowing it. As in any scientific discipline, data scientists may borrow techniques from related disciplines, though we have developed our own arsenal, especially techniques and algorithms to handle very large unstructured data sets in automated ways, even without human interactions, to perform transactions in real-time or to make predictions. 1.
Different Types of Data Scientists The following articles, published during the same time period, are still useful: Repurpose backup and archive data to gain value. Historically, backup and archive data has represented the most comprehensive data set in many organizations.
Cybrary ‹ Log In. Project Management 101: The Complete Guide to Agile, Kanban, Scrum and Beyond - The Ultimate Guide to Project Management. "Of all the difficulties facing NASA in its bid to send humans to the Moon in the Apollo program, management was perhaps the greatest challenge.
"- Roger D. Launius, chief historian, NASA Humanity has a track record of wielding some serious project management chops. From building the Great Pyramids to landing on the moon, humanity's greatest endeavors have required thousands of people working together on common goals. Although most of us will never be tasked with goals of such scope, many of us have to manage projects in one way or another. Project Management, simplified, is the organization and strategic execution of everything that needs to get done to tackle a finite goal—on time and within budget.
Register For An Account. Mountain Goat Software. Architecture Envisioning: An Agile Best Practice. A common agile practice is to perform some high-level architectural modeling early in the project to help foster agreement regarding your technical strategy within the team and with critical stakeholders.

The goal at this point is to identify an architectural strategy, not write mounds of documentation, enabling you to do this swiftly. You will work through the design details later during development cycles in model storming sessions and via TDD. Disciplined Agile Delivery: A Practitioner’s Guide to Agile Software Delivery in the Enterprise. The Disciplined Agile Delivery (DAD) process framework, as described in this book, is a hybrid approach which extends Scrum with proven strategies from Agile Modeling (AM), Extreme Programming (XP), and Unified Process (UP), amongst other methods.

DAD extends the construction-focused lifecycle of Scrum to address the full, end-to-end delivery lifecycle from project initiation all the way to delivering the solution to its end users. The DAD process framework includes advice about the technical practices purposely missing from Scrum as well as the modeling, documentation, and governance strategies missing from both Scrum and XP.
More importantly, in many cases DAD provides advice regarding viable alternatives and their trade-offs, enabling you to tailor DAD to effectively address the situation in which you find yourself. By describing what works, what doesn’t work, and more importantly why, DAD helps you to increase your chance of adopting strategies that will work for you. UML 2 Activity Diagrams: An Agile Introduction. UML 2 activity diagrams are typically used for business process modeling, for modeling the logic captured by a single use case or usage scenario, or for modeling the detailed logic of a business rule.

Although UML activity diagrams could potentially model the internal logic of a complex operation it would be far better to simply rewrite the operation so that it is simple enough that you don't require an activity diagram. In many ways UML activity diagrams are the object-oriented equivalent of flow charts and data flow diagrams (DFDs) from structured development. Let's start by describing the basic notation (there's more) that I've used in Figures 1 and 2: Initial node. The filled in circle is the starting point of the diagram. The activity diagram of Figure 1 depicts one way to model the logic of the Enroll in University use case, a very common use of activity diagrams because they enable you to depict both the basic course of action as well as the alternate courses.
Data Modeling 101. The goals of this article are to overview fundamental data modeling skills that all developers should have, skills that can be applied on both traditional projects that take a serial approach to agile projects that take an evolutionary approach.
My personal philosophy is that every IT professional should have a basic understanding of data modeling. They don’t need to be experts at data modeling, but they should be prepared to be involved in the creation of such a model, be able to read an existing data model, understand when and when not to create a data model, and appreciate fundamental data design techniques. Class Responsibility Collaborator (CRC) Models: An Agile Introduction. A Class Responsibility Collaborator (CRC) model (Beck & Cunningham 1989; Wilkinson 1995; Ambler 1995) is a collection of standard index cards that have been divided into three sections, as depicted in Figure 1.
A class represents a collection of similar objects, a responsibility is something that a class knows or does, and a collaborator is another class that a class interacts with to fulfill its responsibilities. Figure 2 presents an example of two hand-drawn CRC cards. Figure 1. CRC Card Layout. Figure 2. CRC Cards for ATM Example. CRC Cards for ATM Example Using CRC cards to assign responsibiities to various classes for the tasks required by the various use cases leads to the creation of the following cards. The following links can be used to go directly to the CRC cards for the various classes: Class ATM. Pupils studying vocational courses need academic stimulus as well. Young people in Britain are having a hard time: on top of news about soaring university fees and ever increasing youth unemployment, students' future employers are now adding to their worries. Recent research from the Chartered Management Institute (CMI) revealed that 90% of public sector managers feel that young people are less employable than their counterparts 10 years ago, and 73% perceived school leavers' management and commercial skills as poor or very poor.
The root of the problem seems to be the education system, which seven out of 10 managers believe is damaging the UK's economic performance. Public sector managers are not alone in their complaints. This is a cry echoed by all sectors; it seems young people are simply not sufficiently trained in basic skills when they arrive in the workplace. The question is whether this problem is a major priority in the face of savage cuts and worldwide emergencies. Gas Detector Alarm - Fire Protection Online Ltd. Bloom’s Taxonomy. Background Information | The Original Taxonomy | The Revised Taxonomy | Why Use Bloom’s Taxonomy? | Further Information The above graphic is released under a Creative Commons Attribution license.
You’re free to share, reproduce, or otherwise use it, as long as you attribute it to the Vanderbilt University Center for Teaching. For a higher resolution version, visit our Flickr account and look for the “Download this photo” icon. Background Information.
Importing Users into Active Directory from a CSV File Using PowerShell. There are two aspects to this post – first is the CSV file with the user data and then there’s the PowerShell script to import the data into Active Directory. As an example, this how-to post will only set the first name, last name, username and password values for our user objects. Preparing the CSV file A template of the CSV file with sample data can be downloaded here (save it with a .csv extension). Here’s what it looks like: Populate the CSV file with the user data, making sure you enter the Distinguished Name of the Organisational Unit in the OU field.
Easy Import CSV Users into Active Directory. Data archiving best practices: The difference between backups and archives. One of the most common questions that come up again and again in data backup and recovery is "What's the different between data backups and archives? Data backup vs. data archiving: Is data backup closing the gap? The backup vs. archive debate has been raging for a long time, and for years, the data backup and recovery community has advocated that "backup is not archive. " However, with recent moves by vendors to integrate more and more functionality into their backup software, there is a question whether this is still true or not. Workflow engine - Wikipedia. A workflow engine is a software application that manages business processes. It is a key component in workflow technology and typically makes use of a database server.
Introduction to Business Process Management. BPM (Business Process Management), CRM and Cross-Functional Enterpris… Default username/password for Ambari? - Hortonworks. Adding NiFi Server to HDP 2.5 Sandbox - Hortonworks. OMG Business Process Management Portal. Business Process Management (BPM) is a set of techniques for the continuous, iterative improvement of all the processes involved in running a business. In recent years BPM techniques have helped reduce errors, reduce costs and increase productivity at organizations ranging from manufacturing companies to telecoms providers, insurance companies and government departments. BPM's successes stem from both more process automation, and more repeatable, error-free manual processes.
BPM complements other approaches to organizational improvement, and in particular fits well with the SOA (Service Oriented Architecture) software design philosophy; BPM prompts managers to continuously change and evolve business processes, while SOA can help software architects create enterprise systems that adapt to these ever-changing requirements. Further Reading: Magic Quadrant for Intelligent Business Process Management Suites.
Already have a Gartner account? Business Process Management Platform.
What Everybody Ought to Know About the BABOK. When working with new and even some very experienced business analysts, I often receive the following questions about the Business Analysis Body of Knowledge® (BABOK®) Guide: The Business Analysis Process: 8 Steps to Being an Effective Business Analyst. What is a Data Flow Diagram. Python & JSON: Working with large datasets using Pandas.
Working with large JSON datasets can be a pain, particularly when they are too large to fit into memory. In cases like this, a combination of command line tools and Python can make for an efficient way to explore and analyze the data. In this post, we’ll look at how to leverage tools like Pandas to explore and map out police activity in Montgomery County, Maryland.
We’ll start with a look at the JSON data, then segue into exploration and analysis of the JSON with Python. Python3 Tutorial: Memoization and Decorators. What is User Experience? Windows Server 2012 Editions comparison - Thomas-Krenn-Wiki. SuperLoader 3 Datasheet [DS00379A] QNAP TS-451U-1G 4 Bay 1U Rackmount NAS. Quantum EC-LLPAE-YE-C superloader 3 , Tekshop247.com. Recommended Backup Media for Circa 2009? - Server Fault. Network Configuration Management, Change Management - Manage Configurations of Switches, Routers, Firewalls. OSCON 2015 : Beyond messaging - Enterprise Dataflow with Apache NiFi. 15 Questions and Answers from Apache NiFi, Kafka & Storm: Better Together - Hortonworks. Apache Kafka, Storm and NiFi: Better Together - Hortonworks. Real World Use Cases of Real-Time DataFlows in Record Time - Hortonworks. A Paradigm Shift to Business as Usual: Real-Time DataFlows in Record Time - Hortonworks.
Real World Use Cases of Real-Time DataFlows in Record Time - Hortonworks. Managing Real-Time DataFlows From the Internet of Things (IoT) Ingest Tips / Getting Started with Apache NiFi - Ingest Tips. What is Apache NiFi? – Keep-It-Simple-Tech-Docs. Apache NiFi Documentation. Apache NiFi Overview. Small Cluster Hardware Requirements - Cloudera Community. Requirements Gathering 101. 4. NiFi User Interface - Hortonworks DataFlow.
Git for Windows. Exablox Releases OneBlox 4312. What Separates Business Routers From Consumer Routers? Cisco 2901 Integrated Services Router - Cisco. How long will a UPS run? APC smart-ups 2200va lcd rackmount 2u UPS. Windows Server 2012: Building a Two-Node Failover Cluster. Select the Right Hardware for Your New Hadoop Cluster. Google. 48 port patch panel, FTP, cat. 6A, 1U, 19", IDC 110. Integral Network Solutions. UPS Run Time/Battery Backup Time Calculator – Battery Backup Power, Inc. Black Box Explains-CAT6A UTP vs. F/UTP. Cotswoldco. Google. BPMN Examples, Patterns and Best Practises. BPMN Tutorial - BPMN 2.0 Tutorial for Beginners - Learn BPMN.
About Business Process Management (BPM) Tools. Firstprocess obpm11g.htm; filename "firstprocess obpm11g. Common BPMN Modeling Mistakes - Activities. Comparison of Business Process Modeling Notation tools. Efficient Use of BPMN: Principles, Practices, and Patterns. BPMN Examples, Patterns and Best Practises. Process Flow Diagram Using Bpmn Notation – Vidim wiring diagram. Troubleshooting bpmn process diagrams. BPMN2 0 Poster EN. Introduction to BPM. What is BPM? Introduction to the BPM Lifecycle. 2. Set Up the Ambari Server - Hortonworks Data Platform. Free Auctioning Service BPMN Templates. Tech Nation 2017.