

Creative Computing. 7 units44 activitiesremixing encouraged download the Scratch 3.0 version of the guide> help learnerscreate new worldswith computing download the Scratch 3.0 version of the guide.
How To Export an SSL Certificate With Private Key (pfx) Using MMC On Windows - Best practices for Active Directory backup and recovery - ManageEngine Blog. It’s easy to make Active Directory (AD) administrators uncomfortable.
Just ask them about their disaster recovery plan. When faced with this question, most AD administrators will only tell you about their object recovery plan. 3.1.6 Registering Users, Groups and Organizational Units. To create an environment for Systemwalker Runbook Automation , register the required user information on a directory service.

This section explains the registration method for each authentication protocol. Register user information in accordance with the authentication protocol being used. Note Users, groups and organizational units only need to be registered with the LDAP directory for the initial setup after installation. Prepare for Zero Touch Installation of Windows 10 with Configuration Manager (Windows 10) Boot Windows to Audit Mode or OOBE. Sysprep (Generalize) a Windows installation. Storage Spaces overview. Understand Storage Space Tiering in Windows Server 2012 R2 – Larryexchange Blog. Background.
Windows Server 2012 R2 - Storage Spaces (Part 1) Windows Server Administration Fundamentals: 04 Monitoring and Troubleshooting Servers. Processes, Threads, and Jobs in the Windows Operating System. This section describes the Windows scheduling policies and algorithms.
The first subsection provides a condensed description of how scheduling works on Windows and a definition of key terms. Then Windows priority levels are described from both the Windows API and the Windows kernel points of view. Using PXE Boot Technologies to Install Windows over a Network. Preboot Execution Environment. A high-level PXE overview In computing, the Preboot eXecution Environment (PXE, sometimes pronounced as pixie[1]) specification describes a standardized client-server environment that boots a software assembly, retrieved from a network, on PXE-enabled clients.
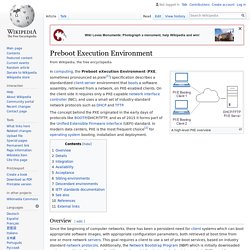
On the client side it requires only a PXE-capable network interface controller (NIC), and uses a small set of industry-standard network protocols such as DHCP and TFTP. The concept behind the PXE originated in the early days of protocols like BOOTP/DHCP/TFTP, and as of 2015[update] it forms part of the Unified Extensible Firmware Interface (UEFI) standard.
GUID Partition Table. Diagram illustrating the layout of GPT scheme.
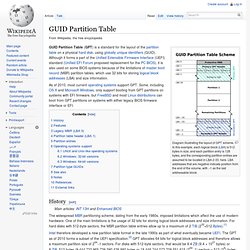
In this example, each logical block (LBA) is 512 bytes in size, and each partition entry is 128 bytes, and the corresponding partition entries are assumed to be located in LBA 2-33, here. LBA addresses that are negative indicate position from the end of the volume, with −1 as the last addressable block. GUID Partition Table. Master boot record. Primary boot sector with partition table in partitioned media of IBM PC compatible systems A master boot record (MBR) is a special type of boot sector at the very beginning of partitioned computer mass storage devices like fixed disks or removable drives intended for use with IBM PC-compatible systems and beyond.
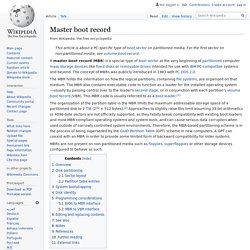
The concept of MBRs was publicly introduced in 1983 with PC DOS 2.0. Volume boot record. The code in volume boot records is invoked either directly by the machine's firmware or indirectly by code in the master boot record or a boot manager.
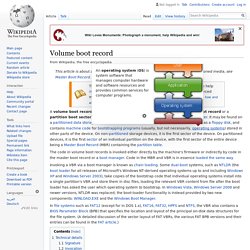
Code in the MBR and VBR is in essence loaded the same way. Invoking a VBR via a boot manager is known as chain loading. Some dual-boot systems, such as NTLDR (the boot loader for all releases of Microsoft's Windows NT-derived operating systems up to and including Windows XP and Windows Server 2003), take copies of the bootstrap code that individual operating systems install into a single partition's VBR and store them in disc files, loading the relevant VBR content from file after the boot loader has asked the user which operating system to bootstrap. In Windows Vista, Windows Server 2008 and newer versions, NTLDR was replaced; the boot-loader functionality is instead provided by two new components: WINLOAD.EXE and the Windows Boot Manager. Technical details[edit] Windows Vista startup process. This article is about startup process in Windows Vista and later versions.
For other uses, see NTLDR. The startup process of Windows Vista, Windows Server 2008 and their successors differs from the startup process part of previous versions of Windows. In this article, unless otherwise specified, what is said about "Windows Vista" also applies to all later NT operating systems. For Windows Vista, the boot sector loads the Windows Boot Manager (a file named BOOTMGR on either the system or the boot partition), accesses the Boot Configuration Data store and uses the information to load the operating system. Winload.exe Definition (Windows Boot Loader) The job of winload.exe is to load essential device drivers, as well as ntoskrnl.exe, a core part of Windows. Kernel Versions. Overview of Boot Options in Windows. UEFI in Windows. Unified Extensible Firmware Interface Forum.
What Is a Chat Bot? A Detailed Guide on How to Create One With Azure Bot Service. A chatbot is an application that simulates a human responding to the user. It’s a more natural way to interact with a system by using conversation. Let’s say, for example, that you want to order a pizza. Instead of wasting your time tapping randomly or searching the Internet to figure out how to use the app, you could just start a conversation as if you were talking with a real human. The chatbot will start asking questions, and as you answer them, the bot will learn who you are and what you like. Changing the Networking Configuration. Features | Documentation | Knowledge Base | Discussion Forums Prev Contents Last Next Changing the Networking Configuration Using the Virtual Machine Control Panel (Edit > Virtual Machine Settings), you can add virtual Ethernet adapters to your virtual machine and change the configuration of existing adapters.
Adding and Modifying Virtual Network Adapters. Certified Big Data and Hadoop Training Course. About Us – Almost There … Virtually Connecting. The purpose of Virtually Connecting is to enliven virtual participation in academic conferences, widening access to a fuller conference experience for those who cannot be physically present at conferences. We are a community of volunteers and it is always free to participate. Using emerging technologies, we connect onsite conference presenters and attendees with virtual participants in small groups. This allows virtual conference participants to meet and talk with conference presenters and attendees in what often feels like those great spontaneous hallway conversations, something not usually possible for a virtual experience. There is only room for 10 in each session but we record and, whenever possible, live stream, to allow additional virtual attendees to participate in the discussion by listening and asking questions via Twitter.
Amazon patents wristband that tracks warehouse workers' movements. Amazon has patented designs for a wristband that can precisely track where warehouse employees are placing their hands and use vibrations to nudge them in a different direction. The concept, which aims to streamline the fulfilment of orders, adds another layer of surveillance to an already challenging working environment. When someone orders a product from Amazon, the details are transmitted to the handheld computers that all warehouse staff carry. Upon receiving the order details, the worker must rush to retrieve the product from one of many inventory bins on shelves, pack it into a delivery box and move on to the next assignment. The proposed wristbands would use ultrasonic tracking to identify the precise location of a worker’s hands as they retrieve items. One of the patents outlines a haptic feedback system that would vibrate against the wearer’s skin to point their hand in the right direction.
Employee Computer Monitoring Software. Humanyze - A U.S. Bank Improves Call Center Productivity and Employee Retention. Identifying What Makes Call Centers More Productive. If Workers Slack Off, the Wristband Will Know. (And Amazon Has a Patent for It.) Docker Tutorial: Get Going From Scratch. Docker is a platform for packaging, deploying, and running applications. Docker applications run in containers that can be used on any system: a developer’s laptop, systems on premises, or in the cloud. How Much Bandwidth and Disk Space Do I Really Need? Dear Developers, Please Support Two Factor Authentication. How to Monitor IIS Performance: Basics to Advanced. Enhanced Logging for IIS 8.5. ManageEngine Applications Manager. Glossary of common Machine Learning, Statistics and Data Science terms - Analytics Vidhya. Configuring Step 1: Install IIS and PHP. How do I change my security settings? Current settings will not.
Connected Toys. Let's Code. Remote Authentication Dial-in User Service (RADIUS) (Building Internet Firewalls, 2nd Edition) 21.7.2. Proxying Characteristics of RADIUS There are numerous RADIUS proxy servers. However, the term is used to refer to two different kinds of server. One of them is a standard RADIUS server speaking to another authentication server (for instance, a RADIUS server that uses NIS or Windows NT domain authentication to determine whether or not users can actually be authenticated).
The other is a RADIUS server that will actually route requests via RADIUS to other RADIUS servers. Global Catalog Servers. The 12 Mighty Chores of Active Directory Administration in Depth. Local Domain groups, Global groups and Universal groups. - Windows CMD.