

COMPUTERs. INTERNET. Your entry to the Deep Web, Darknet, Onionland, Tor, Hidden Wiki, Deepweb. Top 10 Programming Languages to Learn in 2014. Updated on May 5, 2014 Having spent more than 5 years in software development and the computer programming arena, one of the most common questions I am asked is: This is a question that is asked by beginners, as well as experts.
As with many important questions, the answer is not simple. There are many factors that should be taken into account while deciding a programming language to learn. Technology evolves in matter of weeks and by the time you become expert in a particular software technology, it can already be considered obsolete.
In addition to that, another interesting aspect of programming that I noticed is that not only programmers and software engineers are interested in learning new programming languages, but people from totally different walks of life are also into it. Deep web. Technology & learning. Deep web. SEARCH ENGINE 3. Tools. Hackers. Selected Sites. Interfacing PS/2 keyboard to PIC microcontroller. As usually Chris from Pyroelectro suggests his next cool tutorial.
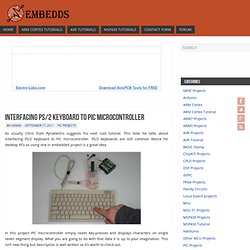
This time he talks about interfacing PS/2 keyboard to PIC microcontroller. PS/2 keyboards are still common device for desktop PCs so using one in embedded project is a great idea. In this project PIC microcontroller simply reads key-presses and displays characters on single seven segment display. SecLists.Org Security Mailing List Archive. How to become a real Computer Geek. Little known to most, there are many benefits to being a computer geek. In our high-tech society, being a computer guru can be one of the most high paying jobs available and they are highly in demand, especially if you want to become a network administrator.
By tapping into your inner geek, you can develop a most useful skill that will be sure to pay off later in life. Here with I am attaching some useful links ,It may help to a person who have real ambition to become a Real Computer Geek,a Geek, Hacker,A Reverse Engineer ….. Things Every Computer Geek Should Know!!. 1.How to hide files in JPEG pictures. If you’re looking to hide files on your PC hard drive, you may have read about ways to encrypt folders or change the attributes on a file so that they cannot be accessed by prying eyes. 2.
Using Google, and some finely crafted searches we can find a lot of interesting information. Top 50 Free Open Source Classes on Computer Science : Comtechtor. Computer science is an interesting field to go into.

There are a number of opportunities in computer science that you can take advantage of. With computers increasingly becoming a regular part of life, those who can work with computers have good opportunities. You can find a good salary with a program in computer science, and as long as you are careful to keep up your skills. Here are 50 free opencourseware classes that can help you learn more about computer science:
¿WEB? Predrax. Zeytinolsa. MySQL.com Compromised & Spreading Malware. The latest story doing the rounds is that MySQL.com got hacked and was serving malware which put it on the Google malware block list.

It appears to be in the clear now though and it’s accessible again via Google. It seems to be a similar case with that of the recent Linux.com and Kernel.org hacks – in which the sites were compromised via developers who had access. In this case it seems MySQL.com was compromised by malware that spreads itself via FTP from client machines, it then uploads malicious JavaScript to any sites the client machine has access to and propagates malware using those sites.
Hackers recently compromised the website hosting the open-source MySQL database management system and caused it to infect the PCs of visitors who used unpatched browsers and plug-ins, security researchers said.MySQL.com was infected with mwjs159, website malware that often spreads when compromised machines are used to access restricted FTP clients, a blog post from Sucuri Security reported. And Beyond… ha.ckers.org web application security lab. Here we are, my friends.

The 1000th post. Whew! It’s quite a load off to have finally made it. Hopefully this doesn’t come as a surprise to anyone since I’ve been announcing it for months, and if you have questions, hopefully the FAQ can answer them. I wrote and re-wrote this post several times. It wasn’t that long ago that I unfortunately lost my love affair with security. Making Fake ATMs Using 3D Printers.
Web Resources. GOOGLE SERVICES. Electronics. Anonymous. .....(-(-_(-_-)_-)-)..... IRC. Hacktivism/Digital Activism/Online Privacy, Security,Anonymity.
Software. NachoFoto - Realtime Image Search Engine. Home Network Security. This section provides a basic introduction to the technologies that underlie the Internet.
It was written with the novice end-user in mind and is not intended to be a comprehensive survey of all Internet-based technologies. Subsections provide a short overview of each topic. This section is a basic primer on the relevant technologies. For those who desire a deeper understanding of the concepts covered here, we include links to additional information. What does broadband mean?
W3. The C0mput3R. Msoft. Trunk.ly.