

Binwalk. Public Lab: ramanPi - The 3D Printable Raspberry Pi Raman Spectrometer. ****If you have Python, pyQt4, matplotlib, signal processing, optics, raman spectroscopy or FPGA experience contact dev @ ramapi .org!
Or go to dev . ramanPi . org and sign up to the developer forums! What I want to do: Build a Raman Spectrometer based on a Raspberry Pi, make it 3D Printable and customizable.. An open source 3D Printable Raman Spectrometer that uses a raspberryPi, a couple of arduino compatible ARM boards, a really bright laser and some parts you can grab from eBay, adafruit, sparkFun, Mouser, or wherever...! BASIC DESIGN GOALS: 1. My attempt and results For the most current information, please visit I keep pretty detailed logs of my progress on that site.. Questions and next steps Finish it and go to space!
Why I'm interested Because Science!!! Here's the new 'Semifinalist' video... There are some pictures below.. just a couple.. News from India on Technology, Electronics, Computers, Open Source & more: EFYTIMES.COM. Hacking tools can be dangerous in the wrong hands.
Hacker Test: A site to test and learn about web hacking. Top 15 Open Source/Free Security/Hacking Tools. 1.
Nmap Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. Nmap homepage. 2. Wireshark is a network protocol analyzer. 3. Metasploit Community Edition simplifies network discovery and vulnerability verification for specific exploits, increasing the effectiveness of vulnerability scanners. 4.
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers. Top 50 Hacking Tools That You Must Have. Whether you are a Penetration tester, a hacker or an aspiring newbie trying to learn Cyber Security, you must have a nice catalogue of tools to make your life easier.
While these tools do make working simpler but cannot compensate for the vast amount of knowledge required in this field. Ethical hacking and online security involves a lot efforts. Many tools are used to test and keep software secure. The same tools can also be used by hackers for exploitation. Reverse Engineering Serial Ports. Given the name of this blog and the number of requests that I’ve had, I think it’s high time we discussed serial ports; specifically, serial ports in embedded systems.
My goal here is to describe the techniques that I’ve found effective in identifying and reverse engineering embedded serial ports through the use of definitive testing and educated guesses, and without the need for expensive equipment. Serial ports are extremely useful to embedded developers, who commonly use them for: Accessing the boot loaderObserving boot and debug messagesInteracting with the system via a shell. Bus Pirate. From DP Bus Pirate v3.6 available now for $30.15, including worldwide shipping Bus Pirate v3.6 is also available at Adafruit Industries (USA) EpicTinker (USA) Watterott Electronic (Germany) Evola (Europe) Anibit (USA) Hackaday (USA) The Bus Pirate is an open source hacker multi-tool that talks to electronic stuff.
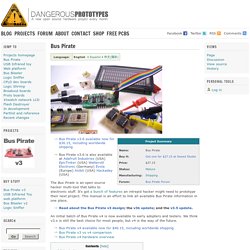
It's got a bunch of features an intrepid hacker might need to prototype their next project. This manual is an effort to link all available Bus Pirate information in one place. Read about the Bus Pirate v3 design; the v3b update; and the v3.5 update. Features overview. The Common Methods of Hardware Hacking.
Hardware Hacking is an art, but there are some common methods to modifying devices that can jump-start any good hacking project.
Favorited Favorite 2 The word “hacking” as it pertains to hardware is often misused. In the commonly accepted definition, “hardware hacking” means modifying a piece of existing electronics to use it in a way that it was not necessarily intended. Even that definition is vague, as it can refer to any method of modifying hardware, be it the enclosure, the electronics, or the behavior. Modifying an enclosure of a device is usually straightforward; drill a hole, cut a slot, etc. If you’re looking to hack a piece of hardware, how you approach the hack depends on what you’re trying to do. Method 1: Patching Into I/O The first (and arguably easiest) method of hacking a device is patching into its control mechanism. With access to button pads, you can attach your own button, relay, or transistor circuit to control it with your own hardware. Image courtesy of Hackaday. Discovering Debug Interfaces with the JTAGulator Part 2 by Joe Grand.
Discovering Debug Interfaces with the JTAGulator Part 1 by Joe Grand. DEF CON® Hacking Conference - Tools.
Firesheep - codebutler. When logging into a website you usually start by submitting your username and password.

The server then checks to see if an account matching this information exists and if so, replies back to you with a "cookie" which is used by your browser for all subsequent requests. It's extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else.
This leaves the cookie (and the user) vulnerable.